How serious is the notion of compliance in your company? Is your reputation in the marketplace linked to conformance to an established set of laws, rules or standards? Are there protection mandates in the contracts you have with your customers and key suppliers? What are the implications of inadequate security with regard to your insurance? We are a key player in the governance of these internal controls.
Objective: To track, analyze and report on risk-related conditions and events that are subject to mandated or self-imposed compliance. Additionally, to identify root causes so as to eliminate defects in safeguards and establish accountability for corrective actions.
Risk Management Strategy: Every organization experiences serious events or conditions that must be escalated to a designated individual or authority for notification and remedial follow-up. These are the incidents that make it to the Board’s risk management or audit committee. They may require regulatory or customer notification, and they are likely to have noteworthy financial impact. You don’t want them on your watch — especially if the failed control belongs in Security’s portfolio.
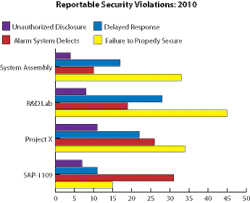
To add insult to injury, most are avoidable. The rules and responsibilities are — or should be — known. The graphic above is typical of Security’s normal approach to metrics: We maintain counts of what and how much. The essential next step is what security management does with this data. If you accept the fact that what you see here indicates avoidable risks, the next step is to dig deep and uncover the root causes.
Compliance standards all possess embedded measures for monitoring conformance. For example, if certain types of information must be protected to a specific standard, inspections will reveal the status of safeguards, and automated tools and protective systems can monitor for and alert to attempts to compromise protection. Processes to ensure or verify personnel reliability may be measured, as can response to potential threats to protected assets. In sum, there is a diverse inventory of sources for actionable metrics.
In the best of circumstances, an internally directed compliance review or risk assessment identifies the internal control defect or security vulnerability, nails the cause, and addresses the exposure before an event occurs. Your value metric is the number of vulnerabilities you have proactively discovered and fixed. In the worst-case scenario, the defective control that you knew about somehow never got fixed. Somewhere between best and worst is the case in which a previously unidentified defect directly contributes to a notable event. Both of these metrics also need to be tracked—at least, while you are around to track them.
Look at the four indicators being tracked by the department in the graphic to the left.
• Unauthorized disclosure relates to proprietary information that has been transmitted by any means in violation of standards of protection.
• Delayed response: We can all envision certain types of incidents, alarms or calls for service that establish standards for first responders. Time from dispatch to arrival is logged for verification of adequate response time.
• Alarm system defects: Alarms installed to monitor sensitive areas or assets must meet specific standards of reliability. Standards for tracking faulty, false or nuisance-induced annunciations are checks on system reliability and responder confidence.
• Failure to properly secure relates to the missteps of persons accountable for following established protection standards, whether the cause is malicious intent, negligence, or a flawed understanding of their responsibility.
Think about what is reportable in your company and what protocols are in place to ensure reporting compliance. The rules are clear if you are in a regulated business environment, but may not be in a less formalized setting.
George Campbell is emeritus faculty of the Security Executive Council (SEC) and former CSO of Fidelity Investments. His book, “Measures and Metrics in Corporate Security,” may be purchased through the SEC Web site. The SEC works with Tier 1 Security Leaders™ to reduce risk and add to corporate profitability. Through its pioneering approach of Collective Knowledge™, the SEC serves all aspects of the security community. To learn more, mail [email protected] or visit www.securityexecutivecouncil.com/?sc=std. The information in this article is copyrighted by the Security Executive Council and reprinted with permission. All rights reserved.