The higher education security standard of care continues to evolve, with technology playing a more important role than ever. Today's more security-conscious environment requires much more than a well-thought-out plan. Effective implementation of key strategies is paramount to both security program perception and reality.
Campus administrators are getting much better at understanding security technologies, their limitations, and how they should fit into their security program. This article expands on four strategies the nation's leading universities are successfully implementing to take maximum advantage of what security technology has to offer.
Strategy 1: Widest Net Mass Notification
Keeping students, staff, faculty and parents informed in a crisis and maintaining a sense of order is appropriately high on everyone's list of important issues. Given the saturation of instant communication technologies like twitter into our daily lives, Clery Act interpretations of how fast notifications must occur to be considered "timely" are expected to shorten significantly (Note: The Clery Act requires all colleges and universities that participate in federal financial aid programs to keep and disclose information about crime on and near their respective campuses).
Historically, the industry push for "silver bullet" application solutions has overshadowed some of the real limitations of some of these technology interdependent applications. E-mail, text messaging and Web-enabled devices are so engrained in our daily lives that their application as universal saviors in a crisis seems on its face to be sound judgment. However, real-world realities have shown us that, for larger institutions at least, there are fundamental flaws in the execution of an approach relying on only one or two notification technologies.
No matter how robust the infrastructure or confident the promises, the logistics of maintaining massive lists of high turnover populations and real limitations of technology in a crisis has proven to be a bigger challenge than anticipated. Fundamental misperceptions about what certain systems are capable of doing are still a regular occurrence, sometimes resulting in an incomplete emergency notification strategy and unfulfilled campus needs.
Sending tens of thousands of e-mails and/or text messages at once has overwhelmed systems and caused embarrassing delays in getting word to intended recipients. In many cases, alerts have been received many hours after an incident's conclusion and after media reporting has occurred. In a recent incident report on the Virginia Tech incident, administrative staff warned their own families nearly 90 minutes before the rest of the campus was notified.
The good news is campuses that have deployed solutions are re-evaluating their notification systems and replacing insufficient systems with more robust and flexible services. New purchasers of notification systems are taking advantage of the lessons learned by early technology adopters. The new standard-of-care focuses on a multi-mode system strategy that incorporates high-tech, low-tech and no-tech solutions into their notification plan. While text messaging still remains an important component of the alert program, comprehensive solutions now include radio, television, audio paging, instant messaging, phone calls, digital message boards, improved continuous awareness training, and even old-fashioned emergency lights and sirens.
One technology that promises to ease the performance problems associated with cell phone messaging even further is "cellular broadcasting." Instead of needing to acquire and maintain massive user lists, cellular broadcasting allows for transmitting a message simultaneously to anyone near a particular cell tower. This technology greatly reduces drain on network resources which will lead to significantly increased performance and system effectiveness.
Strategy 2: Intelligent Video Analytics Ready for Prime Time
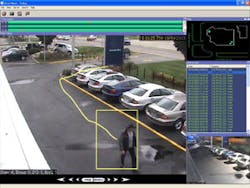
Effectively enhancing the eyes and ears of increasingly strained campus security resources with advanced intelligent video systems is now a viable reality. For many years, we have heard the promises, seen the trade show demonstrations, and in some cases, deployed "Beta systems" to gauge the security and safety enhancement possibilities of these systems. Unfortunately for those early adopters, the promise did not come close to justifying the hype.
Initially, these "military rooted," processor-heavy applications were designed for government entities not concerned about price, complexity or false alarm rates, and came with more than their share of challenges. Rightfully, campus administrators became skittish about these over-promised systems.
However, the industry has undergone a virtual makeover. Healthy competition by a number of emerging manufacturers combined with maturing technology has finally resulted in significantly lower prices. Legacy manufacturers have applied many lessons learned from their field deployments over a number of generation cycles to improve the accuracy and functionality of their products. Systems now offer many more "a la carte" options to suit a particular application and clients are no longer forced into a bundled suite of detection sets at a high fixed cost.
Analytics can now be deployed using a centralized or decentralized model as appropriate for the application and available resources. Cameras from a number of manufacturers now can be ordered with specific analytic features or a combination of features built directly into cameras at the factory. Cameras now can come loaded with an entire suite of password-activated features so that detection features can be upgraded remotely via software with just a few keystrokes.
Systems now use advanced and easier to use "learning modes" and "masking" features to facilitate better system "tuning," which reduces nuisance and false alarms to a manageable level.
Intelligent video is now easier to deploy, offers better condition adaptive "learning," requires much less processing power to function, and is much less costly. Analytics systems that not that long ago cost $3,000-$5,000 per camera while using intense server processing resources can now achieve many of the most essential features for a few hundred dollars per camera or less.
The University of Southern California (USC) for example, has deployed the latest generation intelligent video analytics to improve incident detection, assessment and response. The campus and others are now effectively using video analytics to extend the reach and effectiveness of public safety staff in areas where undesired activities could occur.
Strategy 3: Instant Building Perimeter Lockdown
For traditionally open and unrestricted education environments, closing access to campus facilities during an emergency or security incident has been an challenge. Campus public safety officials have for years struggled with the inability to quickly lock down a building or series of buildings when necessary. Some campuses still use antiquated and inefficient phone trees, relying on land line phone calls to individual departments to instruct staff to manually close and lock facility access one building at a time, door by door. Once the all-clear decision is ultimately made, an equally tedious reverse process is required to return facilities to their normal state.
The trend at campuses is to upgrade traditional locks around the building perimeter to electrified locks connected to a centralized system. Using USC as an example, "perimeter" doors can be anywhere from the basement, up to the 3rd floor, depending on site elevation, exterior stairs, or connection to nearby structures. When electronic perimeter door locks are connected to an access control system, an authorized person could initiate "one-click" locking of a building, a series of buildings, or even an entire campus at the touch of a button, within seconds. Such a system can automate this process further, by attaching pre-determined actions to a specific threat level such that when the campus or building threat level is raised, buildings can quickly and automatically be locked and placed under the control of the access control system.
The locks can also be put on a time schedule, so that all or part of the campus can automatically be secured or opened at different times of the day and different days of the week. At all other times, the system can keep the doors unlocked, allowing free access, or have them locked, requiring a campus identification card for entry.
Editor's Note: For more on perimeter lockdown technology, see the East L.A. College (page 27) and University of Virginia (page 34) case studies.
Strategy 4: Security Systems Commissioning
Sophisticated, software-based security systems can provide powerful tools to support campus security and safety efforts. By nature, such systems are very flexible, with many provisions and capabilities that can act in a multitude of ways to manage the process of physical protection, if properly configured and programmed. However, the full potential of these systems to support enhanced security is often overlooked due to unfamiliarity with the products, weaknesses in security planning, and constraints associated with the design and construction process. Further, most campus safety and security personnel cannot anticipate every specific systems operational programming need until they get their "feet wet" with the new systems.
Commissioning (a concept more familiar to mechanical and industrial engineers) ensures that security systems are designed, installed, functionally tested, and capable of being operated and maintained according to the owner's real operational needs rather than what the manufacturer's boiler plate user manual prescribes.
Traditionally, security installations require a level of testing, called "Final," "Functional," or "Acceptance" testing, as the final requirement for completion of the project. Most of these requirements only scratch the surface of system capabilities and usually do not involve simulating of actual security incidents and adapting systems programming and operational protocols to account for the results of these tests. The complete commissioning process goes further in seeking to guarantee that the system operates properly, that it properly addresses campus vulnerabilities, that it can be adequately supported in the future, and that it can be used effectively by staff as part of the total security program.
This is especially important where sophisticated systems interact with each other, such as with access control, intrusion, video, fire alarm, electrified locking and elevator control systems. In addition, operating and maintenance improvements can be realized when stakeholders are cognizant of the goals of the system, its performance and operational boundaries, and the methods and quality of the initial installation. Commissioning uses a more thorough series of program validation exercises during a burn-in period and enhances customer satisfaction by verifying that systems operate as effectively as possible. The results ensure that security concepts have been properly integrated into the final product. An enhanced Commissioning approach helps protect not only the campus security investments, but develops confidence in every security technology deployed throughout the campus.
Ultimately, successfully deploying proven security strategies and the elimination of chancy "beta" technologies shortens the security learning curve and improves the overall security program. As a result, the perception of campus security is steadily improving and campus security "visions" are becoming reality.