The impact of video data on an IT network is a common concern. Selecting the proper data transmission techniques can assist and play a major role in managing video on the network.
Two data transmission methods, unicast and multicast, are used by most video cameras and encoders on the market. And while many cameras support both types of data transmission, it’s up to the systems designer to decide which to use. Learning some of the differences and network requirements for each transmission technique will result in an informed, purposeful decision.
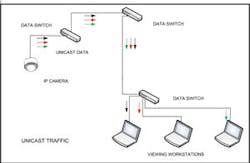
Unicast data transmission allows sending data from one device, or host, to another device/host using specific addresses to set up point-to-point communication. This can be compared to a telephone call between two people. Only the two phones connected can hear the conversation.
Multicast allows data transmission from one multicast server to a group of hosts with only one stream of data from the source. Compare this to a conference call; one person speaks and all on the line can hear the message. Unlike the conference call, multicast data is passed in only one direction.
In a security application consider a single camera sending a stream of video to the shipping dock, the reception desk and the security office. Using unicast techniques the camera would have to open up three streams of communication, one for each of the viewing locations. With multicast, the device would simply transmit the information and all three of the workstations viewing the data would look for that data on the network. The network would be configured so that the single data stream only goes to the switch serving those stations looking for the data thus minimizing traffic on the network.
Clearly, network traffic can be positively impacted through the use of multicast. The challenge is making sure that the network can effectively manage multicast traffic. Key to managing this traffic is the Internet Group Management Protocol (IGMP). Using IGMP each camera would be listed as a multicast server and each viewing station would be considered a multicast host. An important concept to understand is that the data receiving host must register via network protocols its need to receive the Multicast traffic. The IGMP protocol is supported by many layer 2 switches through what is known as IGMP snooping. However, IGMP traffic is best managed at the layer 3 level by use of an addressing table. The addressing table controls what IP addresses receive the multicast traffic in order to prevent broadcast of the traffic to all ports. Some switch manufacturers implement a proprietary version of IGMP so it is important to understand the brand of switches used in the network. Once the groups have been established, i.e. the hosts have joined the groups, a multicast distribution tree is created and managed by a different protocol on the network. This management protocol is called Protocol Independent Multicast (PIM).
Developing a complete understanding and using these protocols will require close interaction with the IT group responsible for the management of your customer’s network. In the case of a complete network design, diligence will be required to ensure data traffic is managed using all the tools available.