We've all watched a three-dimensional (3D) film at one point or another. The technology is defined as something having three-dimensions, i.e. width, length and space. And while the technology in the raw sense has not transcended into the electronic security space per say, a number of technology developers and manufacturers, software providers and integrators are applying the concept of 3D to their business practices. And for systems integrators, leveraging 3D software technologies will allow them to simplify their installations through operational, benefits, allowing them to provide a different type of value-add service to their customer.
Check Point Software Technologies, Redwood City, Calif., is one software development company that uses this multi-dimensional approach to its business practices and solutions.
"The term '3D' is well-understood-we don't have to explain what it is and we can leverage that identity to articulate a conversation that we want to have around security," explained John Vecchi, head of global product marketing for the company. "We are using the term '3D' metaphorically. For us, 3D security is a vision-it's a concept and a blueprint. And security needs to become more of this type of blueprint whereby it's made up of three critical categories, and those are the three dimensions we talk about-people, policy and enforcement."
Vecchi attributed the idea behind this concept to numerous internal discussions as to the critical element that company policies uphold and the disparate environment that many businesses are faced with. Check Point's 3D security concept enables organizations to transform security into a business process by integrating the three dimensions.
"3D is the starting point," said Vecchi. "It's how we say, 'look, security is changing. It's ridiculously complex. There are way too many point products which end up making you more insecure than secure. It's not seamless or secure. Policies are disparate, they are not well-understood and they are not well-aligned to your business needs.' 3D is a way for us to say that security needs to move to be automated, it needs to be a process, it needs to be more seamless and has to involve people. And folks that I've talked to are ready for security to change-they know it has to," Vecchi continued.
Check Point's R75 is a network security solution that implements elements of this multi-dimensional approach. Based on its software blade architecture, it enables customers to extend the firewall into a multi-function and multi-dimensional gateway that consolidates protection into a single, unified solution. Check Point R75 works off of four new software blades for application control, identity awareness, data loss prevention and mobile access. This enables businesses to gain greater visibility and control over data, Web 2.0 applications, and mobile access-bringing organizations multi-dimensional security in a single, integrated solution.
A step above GUIs
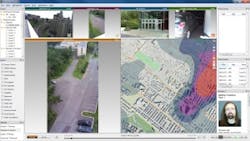
Feeling Software's Omnipresence 3D is another platform that goes beyond traditional solutions in delivering improved situational awareness and faster response to emergencies, confirmed Christian Laforte, president, Feeling Software, Montreal. The company's platform is a 3D surveillance visualization tool which also serves as an advanced Command & Control (PSIM) system for applications with complex security and safety needs. Omnipresence 3D provides a common monitoring and alarm platform for multiple security and safety systems, including CCTV, fire, access control and other third-party systems.
"It's extremely beneficial for end-users and integrators alike," said Laforte. "All we ask of our integrators is that they understand the high-end market and have good project management skills. We can handle the 3D aspects for them-convert their 2D floor plans into realistic 3D models-introduce them to 3D content creation partners or train them on how to do it themselves using standard off-the-shelf tools. We will support whatever equipment the end-user or integrator wants us to. They don't have to worry about eventually ending up with incompatible systems or poorly integrated ones," he explained.
Systems integrator Security Consulting & Integration, (SCI), San Diego, is working closely with Feeling Software to deploy their Omnipresence 3D platform for Strategic Operations Inc. (ST/OPS) in San Diego to enhance their unique tactical military training. Ed Michelson, SCI founder and owner, applauded the company's efforts in developing the Omnipresence 3D technology, citing many of its benefits, from cutting down on the time and effort that an end-user is required to provide in watching video; to the software's capability to track an individual as they move from place to place; the provided 3D view of the floor plan of a particular site or campus that an installer may be working in; and even using the Omnipresence 3D in a forensic mode. This would allow a user to view recorded video after an event and track a person's moves backwards. If a person who had stolen equipment off a site and was heading back to their vehicle, it would be possible to get a license plate number off the car in the case that facial recognition of the culprit was not detected.
"Another issue common in the video surveillance industry is in the scenario where there are a lot of cameras on site," Michelson continued. "And I've seen this happen with monitoring people who have worked for a company for years-they see a person in the upper lefthand corner of a monitor screen walking from left to right and that person walks out of that camera's view and shows up in some other camera monitor view. Let's say there is a lot of activity in all these camera views and you're tracking this one person who looks suspicious-you have to know what camera view on the monitor he is going to show up in next because there is so much activity going on that it's not a matter of looking for motion." Michelson confirmed that utilizing the 3D floor plan view of a site that Omnipresence provides also helps to eliminate this issue.
"Two things are going to happen," continued Michelson."Number one, more and more end-users are going to start using something like this, whether it's from Feeling Software or somebody else; and number two, the price of this technology is going to come down. The problem right now is that the expense and perceived complexity of doing this is probably holding back some dealers from getting into it. But it's not that complex. Several years into the future, whether it's two, three, or five years, everyone will be using something like this to review video," Michelson said.
The cost of the system varies based on the number of cameras and sensors and the number of subsystems that must be integrated, in addition to other factors, according to Laforte. "Our system is priced so it represents five-to-10 percent of the total cost of a large security installation," he confirmed.
And while the patented Omnipresence 3D platform provides users with a real-world approach to monitoring their premises, Laforte advised folks to identify what solutions truly provide 3D capabilities and which don't.
"Customers and integrators will need to be careful to distinguish the hype from actually viable solutions," he confirmed. "It's not hard to slap a simplistic 3D map interface onto existing software. By itself, a simple 3D map delivers almost no value. The real benefits are only unlocked once you rethink the whole user interface and deliver a solid solution that scales well across thousands of cameras and other sensors, and dozens of simultaneous users."
So what's the difference between Omnipresence 3D and a standard Graphical User Interface (GUI)?
Feeling Software's patent-pending 3D algorithms, such as its 3D Video Fusion and Fast Track, present operators a realistic view of their facility. The 3D Fusion allows operators to see many videos at once in their actual locations. "It feels more like flying over a facility and seeing through the roof," explained Laforte. "A standard GUI shows an abstract interface. When people solve problems or monitor and investigate a complex situation, they don't think in terms of 2D floor plans or individual cameras. They think in terms of real-world objects (their facility) and threats."
Omnipresence 3D is integrated with OnSSI's Ocularis Physical Security Information Management (PSIM) platform. The 3D map interface of Omnipresence 3D is combined with the live and archived video from Ocularis to provide a solution with an enhanced level of situational awareness.
Additional features such as 3D pan-tilt-zoom (PTZ) tracking and Fast Track (the ability to go from camera to camera with one click) "are the features that make the difference between eye candy (a simplistic 3D map) and actually delivering operationally useful benefits such as monitoring many cameras at once, more easily time-tracking suspects across cameras, and more," confirmed Laforte.
Other 3D security developments
Bosch Security Systems,' Fairport, N.Y., 3D Diffuser technology is embedded in some of its infrared illuminators and infrared imagers, which enables the beam pattern of an LED array to be altered. "Most LED illuminators use a circular beam pattern, which means that much of the infrared illumination is wasted up into the sky," said Anne Insero, manager of Public Relations and Media for Bosch. "3D Diffuser takes this energy and redirects it (via micro-refracting technology) toward the back of the scene to increase the viewing distance and to create a more evenly illuminated image (not a 3D image in the traditional sense of the word)."
"An end-user who implements this technology would benefit from full and accurate video information in low light situations, as these devices help to produce night-time surveillance video that more closely resembles the crisp, monochrome images captured during daylight hours," added Willem Ryan, senior product manager for Bosch. "3D Diffuser technology eliminates hotspots and underexposure by lighting the entire scene," as seen in the figure centered below. "It is ideally suited for high definition surveillance as its beam pattern matches the wider field of view captured by cameras that produce images in a 16:9 aspect ratio," he said.
An area which Laforte sees as exciting is in 3D cameras, of which he claimed the Microsoft Kinect is the best representative. "Capturing 3D video with depth will unlock new benefits like better video analytics and more reliable and unintrusive facial recognition," he confirmed. "I expect it will take three to five years before video surveillance manufacturers offer mainstream 3D cameras with specifications that go beyond the Kinect."
Yet in the realm of monitors for video surveillance, High Definition (HD) continues to heavily outweigh the need for 3D capabilities.
"For the purpose of monitoring or forensic research, I don't see a hook yet for 3D," said Sergio Collazo, director, Sales & Marketing, Imaging Systems Division, Toshiba America Information Systems, Irvine, Calif. "Video surveillance in our world-the technology really follows the consumer, especially in the imaging. I think there is a possible play for 3D in the future, but right now what seems to be catching on well is the high resolution images that a megapixel can provide."
Collazo stressed the importance in the ability of the monitor to support the resolution of a camera. "That is critical right now," he said. "Not every monitor can support the resolution of a two megapixel camera, let alone support a four- or five-megapixel camera. Matching the resolution of the monitor to the resolution of the camera-that is something that is not considered enough." (To see a remote monitoring live demonstration, visit http://www.toshibasecurity.com/products/prod_demo.jsp).
In addition to this, Collazo attributed the shift of the monitor business in the security industry to the consumer products. "We used to sell thousands of security monitors but that business is gone because from an economic perspective, one can go to Best Buy and purchase a VGA computer monitor," he continued. "If a dealer wants to sell a megapixel system, my guess is that he will buy a consumer television that has the resolution support-and I imagine a lot of that business is not going to the security channel. And the reason goes back to the technology. The display technology is not as prolific in the security industry as it is in the consumer market."
The concept of 3D is familiar and while the technology is still far from being heavily adopted in the electronic security industry, systems integrators and dealers must stay abreast of its developments. Maximize your IP investment and get in-tune with your network and IT skills to better prepare yourself for 3D technologies.
About the Author