Organizations today face a myriad of security challenges at their facilities. Managing the access of authorized personnel into a facility is a major concern. The primary challenge for many organizations is to secure their facility from unwanted personnel while also allowing a free-flow of guests, contractors, vendors and business partners who have a legitimate purpose in engaging with the organization.
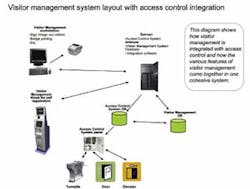
The integration of visitor management with access control becomes necessary when guests are allowed free access to a facility and are not always escorted by a host. An obvious solution is to integrate an organization’s visitor management system with its access control system, allowing the two systems to work in concert to grant entry to authorized outside personnel.
In many organizations – even those that use an access control system – visitors and contractors are still being asked to sign a paper visitor log, which presents a number of problems, including the following:
- Names are often illegible or are false,
- In an emergency such as a fire, it is impossible to quickly determine who is still in the building (check out times are not always required or enforced),
- Information regarding who has visited the company is readily available for everyone to see, but this information should be confidential (and in some environments it is mandated by law to be confidential), and
- The paper log and handwritten visitor badges presents a poor image to visitors and communicates a message of lax security.
An accepted process of integrating visitor management with access control should be a one-step process, doing away with the need to send people to the security office for access credentials. Access for guests can be granted right from the visitor management system so the lobby attendant does not have to interact with the access control system at all.
The integration allows organizations to grant temporary card or barcode access to certain visitors or contractors directly from the visitor management system at the time of check in. The information entered into visitor management is seamlessly passed to the access control system. A proximity card for the visitor is activated in the access control system using the information entered into the visitor management system.
Once an integration is established, using the access control system graphic user interface or GUI, customers can create access levels appropriate for visitors and/or contractors, and then create matching categories or clearances in the visitor management system GUI.
Integration with a visitor management system will ensure that visitors are granted access to specific areas of your facility determined by the administrator, with the specific access level assigned by the host employee or lobby personnel.
When a visitor is checked out of the visitor management system, an integration trigger is executed, which deletes the visitor and badge from the access control database.
If you want to provide visitors with unescorted access to your facility, here are some reasons for integrating your visitor management with access control systems. You want to be able to do the following:
- Allow certain authorized visitors or contractors the ability to move through the facility unescorted (when appropriate, or as an option),
- Limit unauthorized personnel from entering restricted areas, and
- Track activity of everyone – including visitors – who have entered and left the facility.
Today’s security managers routinely expect that their access control system will have integration hooks to these other systems, including their visitor management solutions. For most end-users, the bottom line on integration equates to dollars – getting more functionality and flexibility in economy of scale out of their security equipment as well as more effective total cost of ownership.
By gaining control of your environment through highly integrated access control and visitor management solutions, you can strengthen your overall security, improve user productivity, reduce administration costs, enable regulatory compliance and greatly enhance the image of the organization as being more security-conscious.
Visitor management integration with your access control system helps ensure that your organization is controlling its security infrastructure rather than being controlled by it.
John Murzycki is the director of Marketing for EasyLobby Inc., based in Needham, Mass.,www.easylobby.com.
-------
Pluses of Integrated Access
- Single point of control and management
- Stronger and more secure business infrastructure
- Better functionality from access control
- Ability to scale up or down readily