Sage Conversations: Are you an an agent of change or a 'changed' agent?
Every so often you hear a remark that seems to capture the state of an entire industry. Anyone who sat in the Security Industry Association’s State of the Industry Panel at ISC West 2012 would have heard just such a remark toward the end of the panel discussion. But first some context:
Unique to this discussion was the interchange between the data Gary Wong, an IMS Research analyst that studies the physical security market, was able to display on a video projector and the interpretation of the data by the moderator, Mike Faddis of Microsoft. Maddis had additional panelists besides Wong; they included Francis D'Addario, CPP, CFE, Security Executive Council; Bill Taylor, Security Industry Association Board of Directors; and Jason Bohrer, HID Global.
For approximately 45 minutes, Wong displayed data around the following:
- The Explosion of Big Data: A hockey stick projection of the year over year growth in data including a projection of a 44X growth in digital data through 2020 will require a different mindset. What do we do with this information? How do we process, store, interpret and act on this data in a way that will make us valuable to the organization? Wong forecasted that the “cloud” will be required to offset much of this and will handle approximately 34% of the IT capabilities for big data.
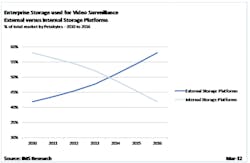
- As-a-Service: Software, platform, and infrastructure services that utilize the cloud will be driving much of the growth as a response to the enormous cost savings and upside organizational value that is inherent in the promise of the cloud. One example, Video-Surveillance-as-a-Service (VSaaS), is projected to grow to $1B by 2014 with two-thirds of the camera market network enabled. One result will be a transition from internal to external storage platforms. According to IMS, “Despite the strong growth for both storage platforms, external storage is forecast to displace internal storage as the dominant storage platform in 2014 (see accompany image , Chart 1). “External storage platforms offer greater advantages over internal storage equivalents by processing and storing much greater quantities of data in comparison to DVRs, NVRs and other internal storage platforms. This is a result of the scalability of external storage platforms; this means that a greater number of hard disk drives (HDDs) can be installed within the device, which creates a much greater data storage capacity.” That’s the prediction from the IMS Research report “The World Market for CCTV and Video Surveillance Equipment – 2011 Edition”.
- Consumerization: The BYOD (Bring Your Own Device) movement of putting more smart devices in the workplace will demand smart security. Only 8 percent of the mobile devices used in organizations are purchased by IT these days. IT professionals are attempting to create value from a highly volatile and risky situation where individual and crowd-sourced data (such as social media) and devices (such as smart phones) are becoming pervasive inside their organizations. Some of them know they need physical security. Some physical security executives know they need IT. The demands of the problem will begin to force accommodation and negotiation between the two.
- Standards and Interoperability: The dearth of standards within the physical security market products has held back the promise of standards, i.e., interoperability between devices and applications. In addition, as it was pointed out by the panel, the interoperability between disciplines also must be a priority. There is interdependence between risk, operations, technology and integration, and that interdependence must be attended to for maximum impact.
Finally, the panel tackled a discussion of the changing nature of identity provisioning and how authentication is being influenced by the cloud, consumerization and standards. One example was HID’s strategy briefing around the “soft key”.
How were the participants reacting to and navigating these changes? This is where “The Great Conversation” gets interesting and where the past becomes prologue to the future.
Francis D’Addario, ex-CSO of Starbucks, published author, and a Security Executive Council emeritus faculty member, was sitting at the far end of the panel. The room was full of product and service vendors and a number of end users. D’Addario began to talk business:
- The organization and its executives need confidence. So how do we take steps that build our intelligence around risk, ‘proof-up’ solutions to demonstrate understanding and relevance, and report on the impact to the business?
- Interoperability must be supported by product vendors and integrators. They also must ‘proof-up’ the value equation to help drive the solutions into the enterprise.
- Leadership and execution: Navigating change is our responsibility. Helping the organization make sense of the balance between risk and reward to their people, their processes and to the organization is a functional business problem requiring a depth of leadership that may not be present today.
And it is that last problem that D’Addario is spending much of his time on these days. As he would tell you, the “Next Generation" security executive can be made, not just found. “The question is whether we become ‘agents of change’ or ‘changed agents’,” D’Addario concluded. We all have this choice – whether we want to be part of the creation of change or whether we are simply going to stand on the sidelines and let ourselves be affected by these coming changes.
About the author: Ronald Worman is the founder and managing director of The Sage Group, and is a regular contributor to SecurityInfoWatch.com, Security Technology Executive magazine and Security Dealer & Integrator magazine.
About the Author
Ronald Worman
Ronald Worman is the founder and managing director of The Sage Group, host of The Great Conversation events, and is a regular contributor to SecurityInfoWatch.com, Security Technology Executive magazine and Security Dealer & Integrator magazine.