NetAuthority offers new authentication solution for IT security
In the ever-evolving cat and mouse game of safeguarding sensitive information from cyber criminals, a newly launched company is looking to provide users with another layer of security for their corporate networks.
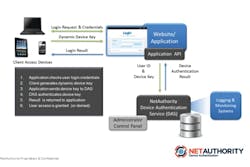
Founded last September and officially launching this week, NetAuthority has developed technology that uniquely identifies and authenticates Internet-enabled devices, thereby providing organizations with the ability to link specific computers, smartphones, tablets, etc., with their network and helping to prevent outside intrusions. The company’s products, dubbed "Device Authentication Service" and "Device Authentication Engine," are currently in beta testing.
"The purpose of (the technology) is to protect assets and those forms of assets are either information assets or, in some situations currencies," said NetAuthority Chairman and CEO Chris Brennan. "By preventing people from being able to access that information from unauthorized devices, it will enable organizations to protect both their account information and assets that are at risk."
Brennan said the challenge for NetAuthority was to develop a solution that could be widely deployed, was affordable and provided organizations with a good user experience, which is in stark contrast to what’s current available to businesses.
"The problem that we observed and recognized was that there was no prevalent technology existing in the form of strong authentication that had been widely adopted in the marketplace," explained Brennan. "As we sort of vetted out that challenge… we realized that there were various reasons, many of which were tied to the complexity, the costs and expense of the alternatives, the vulnerabilities and some of the exposed vulnerabilities of the alternatives. And at the same time, user experience with some of the alternatives to strong authentication yielded some fairly frustrated customer experiences."
The NetAuthority solution works by having users download a “device key generator” application on their device, which will subsequently install a small “plugin” on their credential login page. When the user enters their login credentials, the key requester will get a challenge from NetAuthority’s backend system, which then works to authenticate the user’s device while they are logging into their network.
"The keys that we’re generating to identify and authenticate devices are unique for every single session," explained Talbot Harty, the company’s vice president of product management and development. "This is not a static piece of information that we’re passing back and forth between the device and the authentication system. It is uniquely generated, non-replayable and completely versatile in terms of its expansion going forward."
NetAuthority’s solution is also open architecture and integrates with an organization’s existing IT security infrastructure.
"Our goal here is not to build a whole large platform of our own," Harty said. "It is to provide a very seamless integration into existing security solutions and management solutions so we have a very lightweight integration strategy and a very open architecture when it comes to both a northbound and southbound interface strategy. What that means is you can trigger the registration functions from other applications. This is intended to be kind of behind the scenes happening and then on the backend, all of your logging, reporting and alarms can feed existing systems."
One of the most important aspects of the NetAuthority solution, according to Harty, is creating a positive user experience.
"For the user, the authentication process is unchanged, even though the security associated with it has improved dramatically," Harty said. "The authentication of the device happens in sub-second response time and is basically undetectable from the previous (process) of when I was only providing my user name and password."
Brennan said the NetAuthority solution is ideal for companies involved in the financial services and healthcare sectors, as well as cloud-based service providers and online merchants.
"There is a solution to your problem," said Brennan, speaking of security executives. "You’ve been challenged by this problem for a long period of time; you’ve been exposed from a legal perspective; you’ve been exposed from a vulnerability perspective and a customer satisfaction perspective; and, yet now there is a solution that satisfies all of those requirements that is easy to deploy and very affordable. Clearly, that is the problem we were trying to solve."
About the Author
Joel Griffin
Editor-in-Chief, SecurityInfoWatch.com
Joel Griffin is the Editor-in-Chief of SecurityInfoWatch.com, a business-to-business news website published by Endeavor Business Media that covers all aspects of the physical security industry. Joel has covered the security industry since May 2008 when he first joined the site as assistant editor. Prior to SecurityInfoWatch, Joel worked as a staff reporter for two years at the Newton Citizen, a daily newspaper located in the suburban Atlanta city of Covington, Ga.