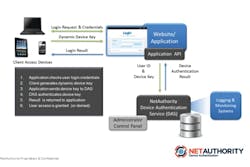
Looking to build upon its’ existing service, NetAuthority, a provider of technology that can uniquely identify Internet-enabled devices and also verify online transactions, recently launched version 1.5 of its authentication solution. The purpose behind updating their current authentication offering was three-fold: To introduce new security features, enhance compliance and improve ease of use for mass deployment by customers.
According to Talbot Harty, the company’s vice president of product management and development, these new features include; a self-registration process for consumer-facing applications; out-of-band/one-time password support to independently verify the user in possession of the device when it’s being authenticated; adaptive elements for their multi-factor authentication engine, increasing the sophistication of the ID and authentication process; the ability to inject synthetic keys; multi-tenant key pair rotation, which provides the ability to rotate public key infrastructure (PKIs) key pairs on-demand; and, FIPS 140 compliance.
“Obviously from a service standpoint, we need to provide a high-performance, scalable and efficient device-authentication service. One of the beautiful parts about the architecture of this product is that it scales so incredibly and efficiently and the reason for that is this white-listing approach where I am not scouring through a plethora of historical data to try to find a record that resembles the historical behavior of this device or the use of it,” explained Harty. “Instead, we are looking at basically known, good device registration and comparing it against authentication of what is supposed to be the correct device for the user.”
Harty added that the company has a large portfolio intellectual property and patents that they continue to develop.
“That’s a core element of our company and one of our guiding principles,” he said. “We also focus on making sure our security solutions are dynamic in nature. In other words, we don’t utilize static information as a sole protection mechanism for security. We have this concept of a constantly moving target for device authentication, which is very unique and the basis of a lot of our patents.”
The proliferation of bring your own device (BYOD) policies within organizations and the need to accommodate a wide range of devices and operating systems has been a growth driver for NetAuthority, according to Harty.
“It is really forcing IT organizations into a more open stance with their policies,” he said. “I was just talking with someone about this and the dissatisfaction, for example, with the solutions that are in place controlling SaaS (software-as-a-service) access and they’re forcing their employees to basically to go through the enterprise network and VPN (virtual private network) tunnels and so forth to then traverse back to the cloud to those services. There is a tremendous growing dissatisfaction with not only the performance of that, but also the fact that that solution does not support a BYOD environment.”
Despite ideas put forth by some in the IT community with regards to replacing traditional passwords with hardware devices or supplementing them with additional logical access products, Harty believes there isn’t a single solution to this problem, which is why things such as device authentication are needed to create multiple layers of security.
“If you were to do device identity alone, as you can imagine, when your device leaves you or gets stolen then it becomes the only factor for authentication for access,” he said. “In that case, a user password would be valuable. As far as an online account is concerned, (username and password) is the weakest form of solution and when that’s the only solution out there, you’re incredibly vulnerable.”
Perhaps the biggest roadblock to getting organizations to adopt more robust IT security solutions, according to Harty, is the complexity in using many of the products that are on the market.
“I think the biggest problem is ease of use,” he said. “That’s one of the main tenants we founded this company to address. If you’re going to make it any more complicated, if you’re going to make there be any more prerequisites or other things that the user has to possess, carry, know or do, I think what you’re running into is companies recognize they can’t throw a lot of obstacles in the way of the user or customers without risking losing them.”
About the Author
Joel Griffin
Editor-in-Chief, SecurityInfoWatch.com
Joel Griffin is the Editor-in-Chief of SecurityInfoWatch.com, a business-to-business news website published by Endeavor Business Media that covers all aspects of the physical security industry. Joel has covered the security industry since May 2008 when he first joined the site as assistant editor. Prior to SecurityInfoWatch, Joel worked as a staff reporter for two years at the Newton Citizen, a daily newspaper located in the suburban Atlanta city of Covington, Ga.