Operational excellence is among a family of business process improvement disciplines including Six Sigma, Total Quality Management, Kaizen and other data-driven approaches to maximize efficiency, eliminate defects and deliver measurable value to the customer that has been adopted by many global corporations.
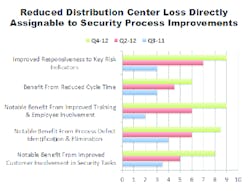
In the example, steadily increasing theft (more than $1 million in 8 months. and confirmation from audit of inadequate internal controls at this company’s central distribution center has led the CSO to craft a collaborative strategy with Internal Audit and Center management employing several principles from the organization’s operational excellence rulebook. The results you see in the chart speak for themselves.
In this particular company, the core process utilized is Six Sigma, which employs a framework with these basic elements:
1. Define the problem and the goals to be achieved;
2. Measure the current process, in this case the homing in on Audit’s documented internal controls;
3. Analyze the data to identify defects and opportunities for defect elimination;
4. Improve the process;
5. Control the improved process; and
6. Measure deviations from the improved processes.
Defect identification involved a process called failure modes and effects analysis (FMEA) — a tool to identify potential process failures and score their consequences. But to give more definitive relevance to this process, the Security team took deep dives into prior investigation findings and then performed a variety of covert risk assessments to further probe vulnerability and internal control process defects. Then they used their findings to postulate several loss scenarios.
Scoring involves several estimates on a 1 (low) to 10 (high) scale: severity is estimated based on potential cost/other consequences; probability is estimated based on how evident the vulnerability might be to one with motive and opportunity; and detectability is the likelihood that the adversary’s attempt would be detected given the effectiveness of the safeguards employed to protect the asset. Finally, the consequence is cost-estimated. This process is useful in demonstrating “what if” and selecting priorities among several scenarios.
What was the result? Several benefits were sought in this analysis given the significance of growing losses and the conclusion that this was clearly an example of avoidable risk.
Improved responsiveness to key risk indicators: As is the case with most recurring loss scenarios, there were a variety of indicators that should have raised red flags for management and for Corporate Security, including the increased use of un-vetted temps; inadequate inventory controls at the receiving dock; refusal to employ video in key areas; lack of secure cages for storage of high-value inventory; and the elimination of a security post within shipping and receiving areas.
Benefit from reduced cycle time: Immediate reconciliation of incoming inventory and assignment of an on-site investigator for immediate response to reported loss.
Notable benefits from improved training and employee involvement: Shift supervisors were engaged as a key element in the improved control processes. Performance reviews highlight loss prevention and security awareness and team meetings are routinely held to review the effectiveness of security procedures and to probe loss incidents.
Notable benefits from process defect identification and elimination: All contractors and temps are now vetted, video coverage was installed in key areas, and secure storage cages were constructed in several areas of the floor.
Notable benefit from improved customer involvement in security tasks: Center management is thoroughly engaged in the protection mission. They have accepted ownership of loss prevention accountability and have seen the advantages of teaming with Security’s expertise. It is also likely that Security has learned to push its involvement in risk mitigation more intelligently.
George Campbell is emeritus faculty of the Security Executive Council (SEC) and former CSO of Fidelity Investments. His book, Measures and Metrics in Corporate Security, may be purchased at www.securityexecutivecouncil.com. The SEC draws on the knowledge of security practitioners, experts and strategic partners to help other security leaders initiate, enhance or innovate security programs and build leadership skills.