Metrics for Success: Aligning Incident Impact with “Acceptable” Risk
What is an “acceptable” risk in your world of exposure to security risk management? How much loss can be tolerated before some threshold of damage is breached? We know that zero risk is as unachievable as 100-percent protection — but without somehow pushing a consensus notion around some baseline target, we cannot get a handle on how much resource to devote to protection activities.
Essentially, we are probing the company’s tolerance for risk, and this is a critical discussion that too few security managers are prepared to have with senior management. What factors help define an appropriate level of acceptance or tolerance? Here are a few:
- From our history, it is not probable and below what we can accept as intolerable.
- The consequences of occurrence are reasonably deemed to be minimal and manageable.
- The cost of protection is likely more than what we can estimate for total impact cost.
- Our insurers, regulators and authorities say it is acceptable.
- The benefits outweigh the potential risks (for example, we will do business in a risky region with significantly lower costs and higher payoff).
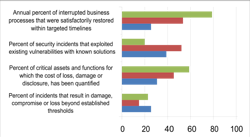
The four measures seen in the chart are linked to the need to identify potential, probable and known impact from security-related events. But, of importance to a business-centered security manager, each one contributes to considerations around return on security investments, assessment of cost effectiveness and program performance measurement.
Percent of critical assets for which a cost of loss, damage or disclosure has been quantified- This is absolutely key to protection planning and program management. Our whole risk management scheme relies on the ability to understand, in real economic terms, what the consequences of compromise could be given a set of rational, not absurd, scenarios. This is why linking what is learned from business continuity planning about recovery timing and cost is relevant to security resource management. All security planning should reside on a foundation of delivering the requisite level of protection at the lowest possible cost. “Requisite” means measurably consistent with criticality and consequences of loss.
Percent of incidents that result in damage, compromise or loss beyond established thresholds- This is a key risk indicator that clearly implies concern for the quality of detective, preventive and response activities. Here, we have taken the quantified estimate of loss noted above and track those incidents that exceed that threshold. Obviously, our goal is to see that no incident has an impact beyond that standard and that can help define protection plans and safeguard capabilities. A simple example is a five-minute standard for response to certain types of calls or alarms.
Annual percent of interrupted business processes that were restored within targeted timelines- This is the counterpoint to the one immediately above, at least as it applies to business continuity risk. But you could extend to “percent of theft incidents with acceptable levels of recovery” or “investigations completed within planned cost” or any number of similar measures. These are important key performance indicators.
Percent of security incidents that exploited existing vulnerabilities with known solutions- I hope and trust that you are doing risk assessments. This should be a compulsory metric in every security presentation since it tells a number of compelling stories about security’s proactive diligence and business unit accountability.
If you are not tracking metrics like these, I’d recommend that you have a discussion with your corporate risk management or finance team. They can advise on how they are approaching larger business process risk tolerance considerations and factors they deem appropriate to impact measurement.
George Campbell is emeritus faculty of the Security Executive Council (SEC) and former CSO of Fidelity Investments. His book, Measures and Metrics in Corporate Security, may be purchased at www.securityexecutivecouncil.com. The SEC draws on the knowledge of security practitioners, experts and strategic partners to help other security leaders initiate, enhance or innovate security programs and build leadership skills.
About the Author

George Campbell
George Campbell is emeritus faculty of the Security Executive Council and former CSO of Fidelity Investments. His book, “Measures and Metrics in Corporate Security,” may be purchased through the Security Executive Council Web site. The Security Executive Council is an innovative problem-solving research and services organization that works with Tier 1 Security Leaders™ to reduce risk and add to corporate profitability in the process. A faculty of more than 100 experienced security executives provides strategy, insight and proven practices that cannot be found anywhere else. Through its pioneering approach of Collective Knowledge™, the Council serves all aspects of the security community. To learn about becoming involved, e-mail [email protected] or visit www.securityexecutivecouncil.com/?sourceCode=std. The information in this article is copyrighted by the Security Executive Council and reprinted with permission. All rights reserved.