Tips to secure your enterprise
October marks the 10th annual National Cyber Security Awareness Month (NCSAM), encouraging organizations to focus on online safety. With that in mind, I'd like to offer enterprises three tips to prevent their corporate data from being hacked.
2013 has been full of advancements and changes that significantly alter enterprises' security needs and how they manage employees who use their own mobile devices at work, or BYOD. At first, the focus was solely on managing the devices, but after Edward Snowden's shocking exposé and Kalinin's attack on financials, including NASDAQ, securing identities, cloud resources, and mobile apps has become paramount.
So here are some recommendations to follow to help better secure online identities and enterprise information.
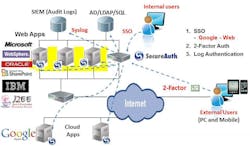
1. Focus on securing applications and resources, not devices. More consumers are accessing corporate applications from their mobile devices for work-related functions, such as email and collaboration tools. Businesses should focus on securing the applications with two-factor authentication rather than devices, which enables users to access an app from any device without requiring hardware control.
2. Regain Control of Enterprise Identities. Companies often relinquish their internal control of employee or customer identities. This practice has not only been proven to be unwise by major hacks like Living Social, Evernote, and LinkedIn; but it is also incredibly costly for companies. Instead, enterprises need to uphold the management of identities, utilizing the same on-premise credentials for authenticated access into Microsoft Office 365, Google Apps, and other corporate resources.
3. Rethink Two-Factor Authentication. Hard tokens have always been common for authentication, but are also costly and cumbersome to maintain. Modern methods of authentication that increase security as well as ease-of-use are instead necessary. There are many different authentication mechanisms available, such as SMS, telephony, email, and PUSH OTPs that facilitate rapid first-time registration; as well as more advanced forms of authentication, like Device Fingerprinting to decrease friction in subsequent authentications
About the Author:
Garret Grajek is the Chief Technology Officer at SecureAuth, Located in Irvine, California, SecureAuth is a technology leader in providing single secured access to mobile, cloud, web, and network resources, serving over 10 million users worldwide. The SecureAuth IdP all-in-one, completely scalable solution delivers to IT departments a simplified way of managing and enforcing access based on existing user entitlements. For the latest insight on enterprise security, follow the SecureAuth Blog, follow @SecureAuth on Twitter, or visit www.secureauth.com for additional information