Physical Security’s #1 Cybersecurity Requirement
Q: IT security group has asked me what our top security system cybersecurity concerns are. How do I answer that both for myself and them?
A: Although a quick answer may be needed immediately, a worthwhile non-trivial answer can be framed in terms of the information security triad: confidentiality, integrity and availability.
Quick Answer
A quick answer can be simple. Based on highly publicized cybersecurity attacks on electronic physical security systems in recent years, the top concerns are security device (particularly cameras) firmware vulnerabilities, and security device password compromises. However, a better answer would be one based on the current physical security system cybersecurity profile, including an assessment of the security of data based on the type and use of the data generated by electronic physical security systems and recorded in investigation case management software. Availability for physical security systems means not just availability of information, but the availability of the security devices to perform their job, which in most cases is a 24/7/365 operational requirement.
Are the depth and breadth of cybersecurity protections for the company’s physical security systems at the same level as to how IT protects the company’s information systems? The answer should be “yes”, but typically is “no.”
Information Security Triad
The three classic information security principles known as the CIA Triad (for confidentiality, integrity and availability) or Information Security Triad, are the foundation of information protection and are very familiar to your IT security group. Any cybersecurity attack is going to violate one or more of these principles. Although originally designed for information systems, the Security Triad is also applicable to electronic physical security systems. To get a good idea of the depth and breadth of security system cybersecurity concerns, see the Viakoo white paper titled, “Three Indispensable Elements of IoT Security”, downloadable from www.viakoo.com/resources.
Privacy concerns are included in the Confidentiality element, which applies to most of the information that a company’s physical security management deals with, including investigations information. This can be a point for collaboration with HR and Legal departments, as well as IT.
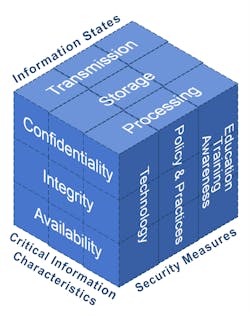
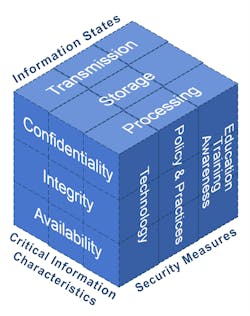
The McCumber Cube
The McCumber Cube (see Figure 1), a framework for establishing and evaluating information security programs, was developed by another STE columnist, John McCumber. First published when he was a Captain in the Joint Staff of the Pentagon, the model was also published in his 1991 book, Assessing and Managing Security Risk in IT Systems: A Structured Methodology. The cube provided a first-ever method for analyzing information protection elements independent of technology evolution, which is part of basic information security education.The basis of the methodology is the inter-relationship among the critical information characteristics of confidentiality, integrity and availability; the information states of data storage, transmission and processing; and the security measures realms of policy, procedures, and human factors (education, training and awareness).
Most security functions haven’t actually performed a data risk assessment – they consider most security-related information confidential and control access to it as seems reasonable. Some security functions collaborate with IT on this – which is a very good idea. To prepare for a discussion with IT security, you can take inventory of the data that Security collects and generates, and document basic information about it.
This simple yet comprehensive approach provides the perspectives needed to cover all the bases when it comes to identifying information security requirements.
Perform a Cybersecurity Risk Assessment
Only with a data inventory on hand, it is possible to do a complete assessment and identify all gaps in data security measures. Completing the risk assessment as quickly as possible is important. During the inventory work, it can be tempting to start addressing risks to data and to the security systems as risks are discovered during the inventory process.
However, without having a complete picture to assess, risk treatment is much more likely to be a weak patchwork of independent fixes than a strong system of comprehensive and cost-effective protection. A find/fix approach doesn’t allow for prioritization, and it is possible to run out of resources (time, money, or availability of personnel) before the most important issues are discovered and addressed. This can result in a low return on security investment and an unknown level of residual risk that is unaddressable because it’s unknown.
Once you have a data inventory, if you don’t have someone familiar with cybersecurity risk assessments, IT will likely be able to guide you in performing one.
Data Inventory
What is the information that Security collects from all sources, including video, access control records, security officer logs and reports, “hotlines” or company Intranet forms for reporting security concerns and investigations? List the types of information that Security handles and describe the lifecycle of each type of information, including who it goes to and where it originates and is stored, and what networks it crosses. Surveillance video typically constitutes the largest volume of security data but documenting all the other types of data can reveal a bigger data landscape than expected.
State of System Security
Part of any security risk assessment is the evaluation of existing security controls. In the case of cybersecurity risk to electronic physical security systems, that involves determining the state of system hardening. Utilize manufacturer hardening guides (https://bit.ly/phys-sec-hardening-guides-2021) and vendor cybersecurity guidance to create a basic list of applicable security measures and document the extent to which they have been applied (None, Partly, Mostly, All).
Cybersecurity for Electronic Physical Security Systems
Find out to what extent (resource availability and possible scope of assistance) IT can help you with your cybersecurity risk assessment and risk treatment planning. Many security consultants, and a few integrators, have expertise and experience in performing such work.
About the Author

Ray Bernard, PSP, CHS-III
Ray Bernard, PSP, CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon. Ray has recently released an insightful downloadable eBook titled, Future-Ready Network Design for Physical Security Systems, available in English and Spanish.
Follow him on LinkedIn: www.linkedin.com/in/raybernard.
Follow him on Twitter: @RayBernardRBCS.