Workplace violence and the active attacker continue to register as the highest risk in our risk assessments today. An active attacker typically tops the list due to the expected fatalities associated with such an event. The process to regulate workplace violence in highly impacted industries such as healthcare are too slow in coming. While the Joint Commission has recently amended its expectations for accredited organizations' efforts, there is no federal mandate and states are moving individually and slowly to create criminal penalties for threatening and/or assaulting a healthcare worker.
Outside that industry, the drivers and demands for properly managing workplace violence risks lie in the OSHA General Duty Clause 5 (a) 1 (https://www.osha.gov/laws-regs/oshact/section5-duties) and creating a credible defense against tort law premises liability claims. This article will address some foundational workplace violence prevention program elements and discuss one potential system to determine the appropriate mitigation strategies as risks are identified. As an example of event management in light of evolving risk trends, best practices and tips will be provided to manage to suspend employees when there is an allegation of a workplace violence policy violation.
So, what does implementing a good workplace violence prevention program entail for organizations? There are some clear fundamental building blocks that must be in place to withstand legal scrutiny; but it is more important to simply do the right thing to protect staff from acts of workplace violence, ranging from a lack of civility and verbal abuse all the way to lethal attacks with a variety of weapons. No discussion would be complete without a brief review of the five types of workplace violence offenders. I continue to see training and other references that highlight only four, leaving out “Type Five“extremists. That is not current thinking. The five types of workplace violence offenders are:
- Type One -- The offender has no legitimate relationship to the organization or its employee(s). Rather, the violence is incidental to another crime, such as robbery, trespassing or seeking social media fame.
- Type Two -- The violent person has a legitimate relationship with the organization—for example, the person is a customer or client —and becomes violent while being served by a staff member.
- Type Three -- The offender of this type of violence could be a current or past employee (or contractor) who attacks or threatens other employee(s) in the workplace.
- Type Four -- The offender may or may not have a relationship with the organization but has a personal (or perceived personal) relationship with the victim.
- Type Five -- Ideological workplace violence is directed at the organization, its people, and/or property for ideological, religious or political reasons. The violence is perpetrated by extremists and value-driven groups justified by their beliefs.
Workplace Violence Prevention and Intervention Policy
We have seen an array of policies over the years, some better than others. A good workplace violence policy will have the following characteristics:
- Overarching statement about what constitutes unacceptable violence on organizationally owned or leased property, at an organization-sponsored event, or under circumstances that may negatively impact the organization’s business operations.
- What constitutes prohibited behaviors?
- A conversation on weapons, in light of applicable state laws.
- Search (may or may not need to be embedded, but if not should be stand-alone).
- Reporting and recordkeeping
- The organization’s response to actual or potential policy violations
- No retaliation clause for “good faith” reporting
- Cross-reference to other related employment policies (e.g., sexual harassment)
Some Cautions:
- Be careful about overstating a no-tolerance policy for workplace violence when it is not going to be possible to enforce it, such as in healthcare. A brain injury patient strikes a nurse. While unfortunate, the hospital is not going to be immediately discontinuing care to that patient.
- Avoid conflicts in the policy. For example, it is an interesting paradox when in one breath the employer says that at no time should an employee resort to violence as a solution, then in the next thirty minutes when training on active shooter situations, encourages that same employee to take off someone’s head with a fire extinguisher. The policy should be written with clarity on these matters.
- Don't forget to set behavioral expectations with clients. It is not entirely dependent on the staff to prevent workplace, especially in organizations where a Type Two offender (person receiving service becomes violent while being served by staff), is likely. Examples of setting expectations with the Type Two offender (client, student, customer) can include posting signage, having written codes of conduct, or, in the face of bad behavior, setting up behavioral contracts to set limits for future interactions and outline consequences for continued violations.
Workplace Violence Prevention Workplace Analysis
It is essential to examine the workplace for potential hazards related to workplace violence. This examination can include several activities to inform the process:
- Consider surveying employees. Employees can be an excellent source of important information regarding the type, frequency and triggers of workplace violence. Questions you can ask include:
Ø In the past twelve months and associated with your work, how many times have you experienced a lack of civility, verbal abuse, threats, physical contact with no injury, physical contact with an injury or someone brandishing a weapon?
Ø What was the relationship between you and the offender? An outsider with no affiliation (criminal or extremist), customer, co-worker, intimate or domestic partner.
Ø Ask the same questions to cover the entire employment duration of each employee.
Ø Did you report the incident?
Ø What type of events are most likely to become volatile and why? (One would typically look at stressful events such as denial of service, taking something away from someone, poor performance review, a person being bullied, passed over for promotion, a person feeling disrespected)
- Analyze the workflow and physical space. The analysis of physical space is an assessment of whether employees have a secure work area where they are free from the violent acts of others while performing their work.
o Once you have identified the specific scenarios when violence is most likely to occur, it becomes possible to study the physical environment and identify vulnerabilities that contribute to a higher risk of injury. This step is essential to determine whether there are cost-effective mitigation measures that can be implemented. A mitigation planning framework is presented next.
Mitigation of Workplace Violence
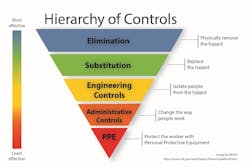
The National Institute of Occupational Safety and Health (NIOSH) has established a framework for workplace violence mitigation—the hierarchy of controls as depicted below. The hierarchy of controls is a way of determining which actions will best control exposures. The hierarchy of controls has five levels of actions to reduce or remove hazards. The preferred order of action based on general effectiveness is:
- Elimination – Elimination removes the hazard at the source. Examples of this mitigation strategy would include 1) Conducting termination via telephone versus having an employee that has been suspended pending investigation return to the workplace for the termination meeting or 2) screening to prevent the introduction of weapons into the workplace.
- ·Substitution – Substitution is using a safer alternative to the source of the hazard. After the 9-11 terrorist attacks, there was a concern about the potential use of silverware on planes being used as weapons, therefore the metal cutlery was replaced with plastic knives, forks and spoons. This is also a tactic often used in behavioral healthcare settings.
- ·Engineering controls – Engineering controls reduce or limit access to workers. Engineering controls can include modifying the workspace, using protective barriers such as hardened or bullet-resistant transaction windows, raising counter heights or extending counter widths to create more distance between a potential attacker and staff or simply enhancing access control measures to ensure only authorized persons may enter a staff-only area.
- ·Administrative controls – Administrative controls establish work practices that reduce the duration, frequency, or intensity of exposure to hazards. Examples of administrative controls for workplace violence would include training, behavioral contracts, a performance improvement plan (PIP) when the offender is an employee, banning offenders from returning to a workplace (when the offender is a client or customer), patient restraints in a hospital setting, body-worn panic alarms, or ensuring special security precautions are taken when a client with a track record of disruptive or violent behavior must be served.
- ·Personal protective equipment (PPE) – PPE is equipment worn to minimize exposure to hazards. Examples of PPE include bullet or puncture-resistant vests worn by security or law enforcement personnel, protective headgear and face shields.
Some Tips on Managing Risks Associated with Current or Former Employees
We have seen a consistent increase in workplace disputes and violations of the workplace violence policies where employees threaten each other, argue and in some cases use improvised weapons in “heat of the moment” disputes. A typical response from the human resources (HR) department is to suspend those employees in conflict pending investigation. These often-overlooked conversations can be potentially dangerous, as evidenced in one such case where an employee who was suspended pending investigation was discovered with a handgun when things became combative between the two employees in dispute. Some things security professionals can coach local HR teams on include:
- Selecting a safe meeting location (when possible) to have the suspension discussion. Some characteristics might include the following:
o Multiple exits
o Close to a facility exit
o Asking for a security presence at or nearby
o Managing the positioning of people (giving staff preference with proximity to the exit(s))
- Considering options for the management of employees’ personal property. It is not typically a good idea to turn a suspended or terminated employee loose in the workplace to go and retrieve personal property. Typical alternatives include:
o Carefully package and ship personal property to the home
o Ask a responsible supervisor to collect the personal property and provide it to the employee when departing
o As a last resort and only in special circumstances schedule a time during off-hours for the former employee to return and pick up items when there will not be a lot of other employees in the facility.
- Be careful during the escort out of the facility. Try to have more than one employee present. Walk behind the employee, not in front, and ensure that if two employees are being suspended, the escorts out are done at separate times and locations (where possible).
- Be mindful of states that allow for weapons to be stored in employees' personal vehicles. It is advisable to have local police on standby for quick response should a situation rapidly degrade. Be sure to diligently observe that the employee leaves the property, not just the building.
- Have a written plan as to how security will be managed after the employee(s) depart the property and particularly post-termination if that is the disposition of the investigation. Having agreements in place well in advance for the provision of armed security is sensible because those agreements can take weeks to execute and you may need to beef up security rapidly.
Conclusion
Mature organizations are taking a disciplined and intentional approach to identify and mitigate risks for the various types of offenders an organization may encounter using the NIOSH model or something comparable. Mitigation strategies should be fully documented for tracking and training purposes. Workplace violence prevention measures should not be deployed in a “set it and forget it “manner. Maintenance of the program requires continuous monitoring, measurement and adjustments.
In closing, there is much more that could be said about identifying and mitigating workplace violence. This article was designed to cover some “tried and true” processes to work through these challenges with the intention of keeping employees safe and reducing the legal exposure associated with having an incident.