Since 2016, 539 ransomware attacks on healthcare organizations in the US have been confirmed. These attacks impacted more than 52 million patient records and have had an often-devastating impact on 10,000 separate facilities.
In total, we estimate the cost of these attacks to be around US$77.5 billion in downtime alone.
Ransomware attacks have been a well-known threat to medical organizations for several years. We saw a massive influx of attacks from the pandemic onwards. While ransomware attacks, in general, are destructive, the impacts on healthcare facilities are arguably some of the most catastrophic. They cripple key systems and prevent hospitals from accessing crucial patient data until a fee is paid to the hacker or the ransomware is removed by IT specialists.
For example, CommonSpirit Health, an Illinois-based healthcare system with more than 700 care sites and 142 hospitals, suffered a ransomware attack in October 2022. The overall cost of the attack has hit a minimum amount of $160 million, with the value still expected to rise. It was reported after the attack that 400 care sites were brought offline for three weeks.
So, what is the true cost of these ransomware attacks across the healthcare sector in the US, how has the ransomware threat changed over the last few years, and what has happened so far in 2023?
To find out, Comparitech's team of researchers gathered information on all known ransomware attacks affecting medical organizations since 2016. However, many entities are reluctant to disclose ransomware attacks, especially when ransom amounts have been paid. It is often only when the hospital/clinic has to acknowledge the breach due to disrupted systems or lost patient data that information about the attack is released to the public. If the latter is the case, these reports will have been included in our study.
Our team sifted through several different healthcare resources— specialist IT news, data breach reports, and state reporting tools—to collate as much data as possible on ransomware attacks on US healthcare providers. We then used all of the available data on downtime and ransom amounts to estimate a range for the likely cost of ransomware attacks on medical organizations. Due to the limitations of uncovering these types of breaches, we believe the figures only scratch the surface of the problem.
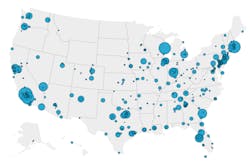
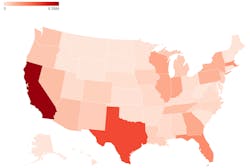
Map of US healthcare ransomware attacks from 2016 to mid-October 2023Please note: we have separated healthcare-based organizations, such as hospitals, clinics, pharmacies, and care homes from businesses that cater solely to the healthcare industry, e.g. pharmaceutical companies and medical manufacturers. The focus of this study is on companies that primarily offer a healthcare service and directly deal with patients and their data. As a result, some figures may differ from previous versions of this study.
Key findings
From 2016 to mid-October 2023, we’ve noted:
- 539 individual ransomware attacks on medical organizations
- 9,780 separate hospitals/clinics/organizations were potentially affected
- 52,298,595 individual patient records were impacted
- Ransomware amounts varied from $1,600 to $10 million
- Downtime varied from minimal disruption (thanks to frequent data backups) to months upon months of recovery time
- On average medical organizations lost nearly 14 days to downtime across all years, with each year varying from 2.6 in 2018 to 18.71 in 2023. In total, this accounted for 6,347 days of downtime
- Hackers demanded more than $39 million across 34 attacks and received payment in 31 out of 160 cases where the medical organizations disclosed whether or not they paid the ransom. They are more likely to disclose that they haven’t paid the ransom than if they have
- The overall cost of these attacks is estimated at around $77.5 billion
- Conti, Maze, Hive, Pysa, and LockBit were the most prolific hackers. The first three dominated in 2020/21 with Hive taking over in 2022 and LockBit accounting for the most attacks so far this year
Ransomware attacks started to take hold in the medical sector in 2020. Just 56 attacks were reported in 2019 but 105 were reported in 2020–an 88 percent year-on-year increase. These figures increased further in 2021 to reach 115 attacks, before dropping to 84 attacks in 2022. So far this year, there have been 66 attacks, suggesting that figures are likely to exceed those from last year.
2021 also saw the highest number of breached records with just over 20 million in total. Since then, the number of records involved in these attacks has declined–dropping to 15 million in 2022 and just over 7 million so far in 2023.
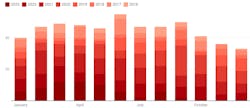
US medical organizations ransomware attacks by month and year
- Number of attacks:
- 2023 (to mid-October) – 66
- 2022 – 84
- 2021 – 115
- 2020 – 105
- 2019 – 56
- 2018 – 28
- 2017 – 51
- 2016 – 34
- Number of patient records impacted:
- 2023 (to mid-October) – 7,318,883
- 2022 – 15,145,901
- 2021 – 20,019,639
- 2020 – 4,856,270
- 2019 – 2,488,107
- 2018 – 481,056
- 2017 – 1,619,824
- 2016 – 368,915
- Average downtime:
- 2023 (to mid-October) – 18.71 days
- 2022 – 15.71 days
- 2021 – 6.74 days
- 2020 – 14.88 days
- 2019 – 13 days
- 2018 – 2.6 days*
- 2017 – 9.5 days
- 2016 – 5 days
- Downtime caused (known cases):
- 2023 (to mid-October) – 262 days (14 cases)
- 2022 – 267 days (17 cases)
- 2021 – 87.6 days (13 cases)
- 2020 – 238 days (16 cases)
- 2019 – 65 days (5 cases)
- 2018 – No known amounts
- 2017 – 19 days (2 cases)
- 2016 – 5 days (1 case)
- Estimated downtime caused (based on known cases and average in unknown):
- 2023 (to mid-October) – 1,235 days
- 2022 – 1,320 days
- 2021 – 775 days
- 2020 – 1,562 days
- 2019 – 728 days
- 2018 – 73 days
- 2017 – 485 days
- 2016 – 170 days
- Estimated cost of downtime:
- 2023 (to mid-October)– $14.7bn
- 2022 – $16.2bn
- 2021 – $9.4bn
- 2020 – $19.3bn
- 2019 – $8.9bn
- 2018 – $908mn
- 2017 – $5.9bn
- 2016 – $2.1bn
*Due to no data being available for 2018 downtime in the US, we used the global average from our worldwide healthcare ransomware study.
The true cost of ransomware attacks on healthcare organizations
Ransom demands varied dramatically from $1,600 to $10 million. Plus, only a handful of providers publicly release the figures involved (we could only find a ransom demand figure for 34 out of the 539 attacks). Understandably, organizations don’t want to discuss ransom amounts or whether they have paid these, as it may incentivize further attacks.
Below are a few attacks where ransom amounts were acknowledged:
- OrthoVirginia was attacked by Ryuk ransomware in February 2021. The attackers demanded a colossal $10 million after an attack on their systems which OrthoVirginia refused to pay. OrthoVirginia reported that it took 18 months to recover from the attack.
- Lehigh Valley Health Network refused to pay $5 million to the ALPHV/BlackCat ransomware group after a February 2023 breach.
- Hackers demanded an extortionate ransom of $5 million from UF Health Central Florida in June 2021. UF Health Central Florida refused to comment on whether the ransom was paid or not but a data breach report was filed for 700,981 patients.
- In April 2023, plastic surgeon, Gary Motykie, M.D., was hit with a $2.5 million ransom demand. When this wasn’t paid, the threat actor proceeded to publish data that included intimate images.
Based on the figures we do have available, we know:
- Average ransom demand:
- 2023 (to mid-October) – $2.08 million
- 2022 – $783,333
- 2021 – $4 million
- 2020 – $535,686
- 2019 – $395,191
- 2018 – $29,500
- 2017 – $54,500
- 2016 – $12,533
- Ransom demanded (known cases):
- 2023 (to mid-October) – $10.4 million (5 cases)
- 2022 – $2.35 million (3 cases)
- 2021 – $20 million (5 cases)
- 2020 – $2.14 million (4 cases)
- 2019 – $3.95 million (10 cases)
- 2018 – $59,000 (2 cases)
- 2017 – $109,000 (2 cases)
- 2016 – $37,600 (3 cases)
Using these figures, we’re able to estimate:
- Estimated ransom demanded:
- 2023 (to October) – $137.3 million
- 2022 – $65.8 million
- 2021 – $460 million
- 2020 – $56.2 million
- 2019 – $22.1 million
- 2018 – $826,000
- 2017 – $2.8 million
- 2016 – $426,133
Adding in downtime
It is difficult to ascertain just how much is lost in these attacks to paid ransom demands, but there is a cost that affects the majority of attacked organizations: downtime.
Downtime occurs when hospitals/clinics shut and/or services are largely unavailable. As we have already seen, servers may be taken offline for hours, weeks, and even months. And in some cases, data and/or computers are unrecoverable.
According to the figures we did find, medical entities suffered an average downtime of nearly 14 days following an attack. So far 2023 has reported the highest average downtime (18.71 days), closely followed by 2022 (15.71 days). Based on these figures, ransomware attacks may have caused 6,347 days, or 17.4 years, of downtime.
So how much could this have cost medical providers?
Only a handful of medical organizations provided an insight into how much these attacks actually cost. Therefore, we used a 2017 estimate that places the average cost per minute of downtime at $8,662 (across 20 different industries) to estimate the cost of ransomware attacks on US healthcare organizations. The cost of downtime to medical organizations over the last three years is estimated at $9.4 million for 2021, $16.2 million for 2022 and $15.5 million so far in 2023. None of these figures exceed 2020’s, however, with an estimated $19.3 million lost to downtime.
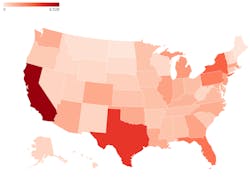
Estimated $ amount lost to ransomware attacks on US medical organizations from 2016 to mid-October 2023While these figures above make for stark reading, they are in line with other losses that come from ransomware attacks. As previously mentioned, CommonSpirit has reported the highest loss of $160 million. Just six other healthcare entities disclosed how much they lost as a result of a ransomware attack, these were:
- Scripps Health, May 2021 = a reported loss of $112.7 million
- Harvard Pilgrim Health Care (Point32Health), March 2023 = a reported loss of $102.7 million
- Universal Health Services, September 2020 = a reported loss of $67 million
- Bio-Rad Laboratories, Inc., December 2019 = a reported loss of $20,000,000
- SmileDirectClub, April 2021 = a reported loss of $15,000,000
- Erie County Medical Center, April 2017 = a reported loss of $10,000,000
- Raleigh Radiology, February 2022 = a reported loss of $330,000 for restoration costs, $685,000 in lost revenue and a further $5,000 for new computer equipment
As we can see from the above map, California had the most ransomware attacks (63), accounting for 12 percent of the 539 attacks since 2016. But with such a large concentration of healthcare providers within this state, perhaps this isn’t too much of a surprise. Texas was a close second with 42 reported healthcare ransomware attacks over the last eight years.
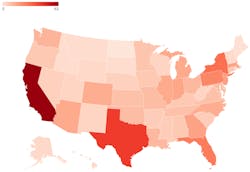
# of patient records impacted by ransomware attacks on US medical organizations in from 2016 to mid-October 2023It’s a similar picture for the number of records affected, too. California saw the most records impacted (nearly 9.6 million in total). The majority of these records stem from two attacks–a December 2022 attack on Regal Medical Group affecting nearly 3.4 million patients’ records and the April 2021 hack on SmileBrands, Inc. which affected 2.6 million patient records.
Texas had the second-highest number of records affected (nearly 6 million patient records).
When it comes to the average number of patient records affected per attack, Wisconsin reports the highest with an average of 608,730 records breached (2.4 million records across four attacks). This is followed by Nevada (295,124) with 1.4 million records across five attacks and New Mexico (236,497) with 945,988 across four attacks.
North Dakota is the only state to have reported zero ransomware attacks over the last eight years. However, patients whose data is compromised could live in any state, and aren’t necessarily from the same state as the breached organization.
Ransomware attacks remain a dominant threat on US healthcare organizations
So far this year, 66 ransomware attacks have taken place on 1,568 medical organizations leading to over 7.3 million breached patient records. With three months still to go until the end of the year, it’s highly likely that 2023 will see a renewed spike in ransomware attacks on healthcare organizations. The same can be said for records impacted, with 15 million reported to be affected already (2022 saw 16 million in total). This reflects hackers ongoing attempts to steal vast quantities of data and cause disruption by encrypting systems.
Another concerning trend is the vast increase in the amount of downtime caused by these attacks. With healthcare organizations witnessing an average of 18.7 days of downtime in 2023, it’s clear that hackers aren’t just succeeding in data theft but are managing to cause unprecedented disruption with their malware.
Methodology
Our research found 539 ransomware attacks in total affecting 9,780 medical organizations. From this, we were able to ascertain how much ransom had been demanded, how much had been paid, and how much downtime had been caused as a result of the attacks. We then used the figures we were able to find to create estimates (an average per year) for the amount of downtime caused by a ransomware attack and applied this to the healthcare entities where no downtime figures were available.
For 2018, where no downtime amounts were available, we used the average from our worldwide healthcare ransomware study. Then, using an average cost per minute of downtime ($8,662) from a recent report, we were then able to create estimates for how much hospital/clinic closures and severe disruptions may have cost. Healthcare organizations that were able to provide a total amount lost due to downtime were included instead of the estimated figures.
We only include ransomware attacks that have specifically targeted a medical facility that offers patient services. Attacks on healthcare-based businesses have been logged separately but aren’t included in downtime figures as patient services aren’t likely to have been impacted, only patient records.
Puerto Rico has been removed this time around.
Data researcher: Charlotte Bond
Author: Paul Bischoff - tech writer, privacy advocate and VPN expert
@pabischoff
Sources
https://healthitsecurity.com/topic/latest-health-data-breaches
https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf
For further sources, please see our US ransomware tracker.