Technology Enhances Access Control
Today’s access control systems represent an important element of the complete networked security solution. Access control components are merged on the corporate network backbone with other systems and devices. Whether it be physical doors, logical access control, intrusion detection, manufacturing equipment, HVAC or fire, network management is the key. At a minimum, these devices and systems must coexist. Optimally, they will collaborate or even converge on the network.
As an industry, access control manufacturers are improving operating standards and working toward interoperable systems and components. Integrators and end users benefit from access control manufacturers who implement technology advances as they become available. The advances improve features and performance, and often reduce the total security solution cost. Benefits include ease and speed of installation, ease of speed of maintenance, greater performance with increasing amounts of data, and convergence on the network.
Increased Interoperability
Interoperability is possible at any interface — card to reader, reader to panel, panel to server, etc. To a great degree, interoperability has been established between the reader and panel. To a lesser degree, some interoperability has been established between the card and reader. When will we see interoperability between the panel and server application? The complexity, sheer number of features and variations in features represent significant challenges to standardization at this level.
Once upon a time, a panel with an 8-bit processor, 64K of memory and a 1200 BAUD modem for a dial up connection to a DOS application represented value in access control security. As computer, software, communications and electronics advance, access control manufacturers must promptly adopt and incorporate the new technologies. As they do, the solution value can increase geometrically.
Configured on the Fly
Once such technology advancement is the Field Programmable Gate Array (FPGA), which provides flexible, configurable hardware. “Hardware” changes can be made after the product is manufactured. The microprocessor, communication interfaces, network controller, and other hardware devices previously consisted of individual chips soldered to a board; now, they are all loaded into the FPGA on startup.
Does your equipment manufacturer need to add an interface or fix a hardware problem on the panel? You used to have to wait months for changes to the physical hardware; now, these changes are made in a software-like language, compiled like software, and then distributed like a software update. Without ever removing you panel from the enclosure, the hardware update is loaded to your panel.
The implementation and use of FPGA technology can resolve the problem of electronic component obsolescence — a challenge for all security electronics manufacturers. FPGA greatly prolongs the manufacturing life of access control panels. This flexibility and longevity is very important to the industry, allowing rapid adaptation to changes in the marketplace and retention of investments.
Removable Media Memory
Another state-of-the-art technology is removable media memory. Inexpensive and non-volatile, it allows a great deal of flexibility. The local database is stored on the memory card, and if a panel needs to be replaced, the memory card can be moved to the new panel to provide immediate, full functionality without waiting for a database update from the server.
This technology is also an excellent tool for integrators. If an integrator has a typical configuration of doors and other devices, that configuration can be loaded to a panel’s memory card in a new installation. Full operation of the local doors, inputs, and outputs can be tested and demonstrated without a server connection.
In some cases the integrator may be waiting for the customer’s network to be completed before going ahead with the project; but, with the removable media memory, the integrator can immediately validate and sign off on the local installation without waiting for the network infrastructure to be completed.
Onboard Ethernet
Another important technology adaptation by security manufacturers is onboard Ethernet. Access control panels have traditionally used third-party plug-in modules for Ethernet connectivity that typically have a bottleneck connection to the onboard processor, reducing the effective communication speed and throughput.
FPGA technology enables manufacturers to include an Ethernet MAC (Ethernet controller) at no additional manufacturing cost, providing native, onboard Ethernet connectivity to the processor. This eliminates the third-party module and avoids dependence on the third party for maintenance and support. This also provides communication data to the processor at actual network speed
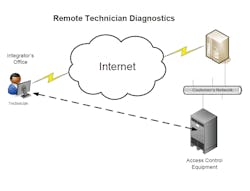
Onboard, native Ethernet provides additional value. Acting as a Web server, the panel can provide complete, browser-based remote diagnostic and maintenance capability for the panel. Third-party plug-in Ethernet modules provide a Web interface and remote maintenance to the module. Onboard Ethernet allows for remote maintenance of the panel itself. This reduces the number of service calls and improves panel uptime.
Single Cards
Many end-users need cards for multiple systems. Students may need cards for ID, physical access, library vending, and other campus services. Government agencies issue CAC, TWIC, or PIV cards. These cards are used for both logical access and physical access. Technology advancements and standards have resulted in cards that can be used in multiple systems.
Equipment and systems manufacturers must converge on the use of a single, common card for any given installation.
Mark Isaacson is Vice President of Engineering at Sielox, Runnemede, NJ. He began with a degree in computer science from Brigham Young University, Provo, UT. He has been professionally involved in software and hardware development, systems architecture, technology development and application in the evolving access control industry for more than twenty years.
About the Author
Mark Isaacson
Mark Isaacson is Vice President of Engineering at Sielox, Runnemede, NJ. He began with a degree in computer science from Brigham Young University, Provo, UT. He has been professionally involved in software and hardware development, systems architecture, technology development and application in the evolving access control industry for more than twenty years.