From the first time I used a Hertz GPS navigation system in lieu of a paper map on the front passenger’s seat, I have found the technology to be an almost indispensable tool. Its adoption over the last 10 years has been remarkable and, for many, a must-have feature in cars and phones. Not surprisingly, GPS has security applications — and vulnerabilities.
First, let’s address the difference between “GIS” and “GPS.” Geographic Information Systems (GIS) analyze spatial information in a database about a location with respect to other locations and displays it in a desired format. The Global Positioning System (GPS) is a technology that can provide location inputs to a GIS system, to be added to other inputs such as satellite imagery and topographic maps. While GPS is a U.S.-deployed system, other systems are deployed or planned by Russia, the European Union, China (PRC), India and Japan.
GPS is a satellite-based navigation system made up of a network of 24 satellites circling the earth twice daily at about 12,600 miles altitude. GPS satellites transmit 50-watt signals (@ 1575.42 MHz in the UHF band for civilian use) which GPS receivers use to determine time of transmission and, using the signal speed (nearly the 186,000 miles per second speed of light), calculate a distance to each one seen. With three satellites in view, latitude and longitude (2-D) can be derived; and altitude can be calculated (3-D) when four or more satellites are visible. Many GPS units show derived information such as direction and speed, calculated from position changes.
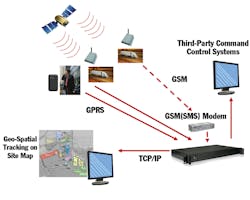
GPS has been used in security to provide monitoring and security of people and assets. Cellular (GSM, GPRS, CDMA), satellite radio (SATCOM), text (SMS) and e-mail are commonly used to send real-time position data and, in some products, device information including system health and status and alarm information. Some manufacturers also employ short and long-range FM radio transmission. Alternatively, data may be stored on a device local to the GPS receiver for later analysis.
Applications include personnel tracking and safety, vehicle tracking, fleet management, container and trailer monitoring, taxi management, ATM tracking, school buses, oil-tank truck monitoring, police patrol management and ambulance management. An interesting variation is “geo-fencing,” where a virtual perimeter is established using coordinate information, allowing the determination of when a person or object has crossed the boundary. With the growing use of smart phones as portals, data repositories and authentication devices for security systems, techniques for locating and recovering lost or stolen devices — such as Apple’s “Find My iPhone” — take on additional importance.
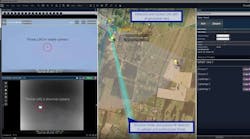
Within GIS systems, establishing a geo-reference of known camera locations, combined with other, tag or sensor data, allows very accurate visual tracking of people or objects on a map display, enhancing situational awareness. Applying location coordinates to digital objects such as photographs, videos and documents adds another dimension to the creation of evidentiary history of an event or situation.
With every technology, however, comes exposure, particularly in the digital domain. Recent press has highlighted the fact that meta-data is often included in digital photos and videos. Both Apple and Android devices are not only capable of this, but also the way their applications are presented to consumers makes it probable this feature is active. As images are posted and shared, it becomes possible for an outsider to learn where a person or target of interest lives, works, plays, or goes to school.
One of the malware threats mentioned at the recent RSA Conference dealt with the threat to travelling executives from having their geographic position discoverable. For family and co-workers, knowing exact location can be interesting and appealing, but that same information in the wrong hands creates a potentially dangerous vulnerability.
The integration of GPS functionality with increasingly powerful mobile electronics (cell phones, PDAs, laptops) and other sensor technologies, such as laser rangefinders, will continue to present new possibilities for position and situational awareness. Users should be sure to understand both the power and the vulnerabilities of these new capabilities to ensure maximum net benefit.
Ray Coulombe is Founder and Managing Director of SecuritySpecifiers.com, enabling interaction with specifiers in the physical security and ITS markets; and Principal Consultant for Gilwell Technology Services. He can be reached at [email protected] or through LinkedIn or followed on Twitter at RayCoulombe.