We just experienced a devastating data breach at the Office of Personnel Management -- at least four million and maybe as many as 14 million records (including those of Congressional personnel) stolen; purportedly by an organized Chinese hacking group. The breach is really more of the same scourge that has been plaguing government and enterprise organizations in recent years, attributed to the same type of attack as the Anthem breach (70 million records) earlier this year. Anthem reportedly was a phishing attack originating at the endpoint.
What’s been in place to thwart such attacks obviously doesn’t work. We need to stop these attacks at the endpoint. Clearly, software security hasn’t done the trick, and I suggest it is time for hardware-based security at the endpoint.
We saw this coming over 10 years ago.
By 2005, hackers were launching organized phishing attacks on the end user to gain access to network data. In “No Phishing Allowed”, published in infotoday.com in June 2005, author Phillip Britt reported that:
- “phishing has become the most prevalent Internet security threat”
- “criminals are constantly honing their phishing techniques”
- “many of these attacks, if they can be traced at all, originate overseas”
Fast forward 10 years, and these types of attacks are as prevalent and harmful as ever.
The OPM breach comes as no surprise.
There is no doubt that in recent years, organized phishing attacks are alive and well. Just ask Home Depot, Target, JPMorgan, the DHS (several times), Sony, the White House, Premera and of course, Anthem. There are also other widespread attacks that have gone on for years, particularly steeling governmental data, known as Operation Pawn Storm/APT28, APT30 and Cleaver. The number of records stolen and the economic harm caused, in just the last 18 months or so when the Target breach was first reported, can only encourage these types of endpoint attacks. Where’s the surprise that this kind of attack was used to intrude the OPM database?
Everything helps, but doesn’t do the trick.
In recent years, product vendors have worked hard to create methods to mitigate the network threats from phishing and similar attacks on the end user. The essential concept is data separation; that is, separating data segments whereby access to particular data is limited and restricted through authentication. The theory is that on the one hand, business activity will be subject to reasonably stringent access requirements, while personal activity has little or no constraints. By and large, these methods are known as “dual persona”, largely relying on technologies developed and heavily promoted in recent years employing containerization or virtualization. Of course, the overall security approach tends to include multiple layers of other methods as well, such as a variety of authentication methods, firewalls, MDM, etc.
Whatever is being used to thwart organized phishing attacks on the endpoint hasn’t worked. End users are still the low-hanging fruit; a decade after the trend in phishing and similar attacks was already well recognized.
Even when security works, it doesn’t necessarily work.
According to published reports, Target had systems in place to trigger alerts in response to the type of breach it experienced. But it was the victim of a perfect storm. Alerts were triggered routinely; the events occurred over a holiday weekend; and the follow-up processes effectively failed. With extensively layered network protection, we may need to watch out what we wish for — complex systems that trigger alerts constantly and require exacting follow up, can easily allow the intruder to fall through the cracks. Clearly it did at Target.
Hardware-separated OS’s: A simple way the Target breach (and others) could have been prevented.
Target fell victim to malware introduced through a successful phishing attack on an HVAC contractor. When the contractor accessed Target’s vendor payment system, the malware went along for the ride.
But what if the HVAC contractor had a dedicated computer solely for Target activity, and another for everything else? Then the phishing attack would have been kept physically separate from the contractor’s Target activity.
However, most of us have laptops, mobile phones and tablets, so asking someone to buy two of each to physically separate and isolate important business activity from everything else is not practical. This creates issues of cost, carrying and power supply.
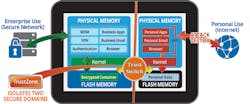
InZero Systems, a tech company out of Herndon, Virginia has come up with a unique solution it calls WorkPlay Technology. It helps solve this dilemma by creating multiple, hardware-separated operating systems whereby each OS has its own resources — kernel, flash memory, RAMS and drivers. Only one OS is active at a time. Switching between OS’s takes one to three seconds. On switching, the active OS is put to sleep mode, and second OS is activated and automatically picks up where the user left off (no need to save and reopen). The relatively small code size (less than 10,000 lines) lessons the likelihood of inadvertent vulnerabilities, as has continually plagued dual persona technologies. (Indeed, as I write this, it was reported that 600 million Samsung Galaxy phones suffered from a security flaw that was discovered several months ago, that Samsung reported it was fixed, but researchers claim the flaw still exists.)
WorkPlay Technology is especially valuable to thwart and discourage phishing and similar attacks. By providing two (or three) OS’s, it becomes much more practical to truly lock down one OS, limiting use and access to authorized activity and resources. Another OS can be used for everything else, and in a triple OS scenario, two can be dedicated to business, and the third for everything else.
The malicious link presents a simple example. When the link is introduced into an OS used for personal activity and not network access, inadvertently opening the link will only infect the personal OS; it cannot migrate to the Work OS and access the network. Furthermore, when untrusted data is received in the Work OS, the user can remove all security doubts by forwarding to the personal OS before opening. The combination of dedicated OS for trusted business activity, and a separate OS for all other activity, goes a very long way to thwart — and therefore discourage — phishing and similar end-user attacks which try to surreptitiously try to access the network.
It would have been sensible and feasible for Target to require its contractors to use the technology, and dedicate one OS solely to Target.
Hardware-separated OS’s a new genre of security technology.
The difference between WorkPlay’s hardware-separation of OS’s and other data separation methods is simple but critical. Malware in one OS cannot obtain the privileges to access another OS, including network access from the second OS. What happens in one OS stays in that OS.
Moreover, significant administrative costs and burden is reduced. There is less need for intrusion detection, device management and employee behavioral management.
Use cases are easy to envision. This technology is appropriate for use cases where data is regulated by law or industry standards, such as HIPAA (healthcare), GLBA (financial institutions), SOX (publically traded companies) and others. When in use the enterprise automatically has elevated its compliance in protecting regulated data. For many years, the American Banking Association has recommended that a separate computer be dedicated to online transactions. Now the same effect is possible using WorkPlay Technology.
Consider the VDI environment. One OS can be dedicated solely to the VDI thin client, another OS to browsing, etc., that could be subject to phishing or other end point attacks. This is a simple way to eliminate end point vulnerabilities of the VDI environment.
What about the OPM Breach?
As I write, the exact OPM attack vector has not been reported, but the correlation to the Anthem attack indicates that one or more individuals were lured into providing access credentials to the OPM network.
Back in 2013, the OPM was encouraging employees to telecommute and reported, “Virtual desktop infrastructure (VDI) is making all necessary applications, data and information available on any computer with an active Internet connection.” (http://publicsectorview.com/federal/winter-approaching-opm-tells-agencies-telework/)
In 2014, Federal News Radio reported that, “by the end of 2014, the General Services Administration expects half of its employees to use a virtual desktop interface (VDI) as a path to using their personal smartphones and tablets on the network.” And “by end of 2015, 75 percent of employees could be using VDI, which would expand the bring-your-own-device approach to GSA.”
When a mobile device or for example, a Chromebook, can provide one OS dedicated to the Government VDI environment and a second OS for everything else, phishing and other malware targeting the end point cannot obtain the credentials to access the VDI environment. Yet the user is not hindered in all other activity; that can occur in another OS.
The Government is migrating to VDI environments for cost-savings reasons. If the VDI access is not physically isolated at the end point, we can expect that the “savings” from this approach will continue to be needed in order to pay for the remediation of OPM-like breaches.
About the Author: Chuck Brooks is a frequent writer and speaker on cybersecurity issues. He is Director of Strategy & Partnering for Inzero Systems, an R & D Technology company in Virginia. In government, he served at the Department of Homeland Security as the first Director of Legislative Affairs for the Science & Technology Directorate. He also spent six years on Capitol Hill as a Senior Advisor to the late Senator Arlen Specter where he covered foreign affairs, business, and technology issues. In academia, Chuck was an Adjunct Faculty Member at Johns Hopkins University where he taught graduate level students about homeland security and Congress. He has an MA in International relations from the University of Chicago, and a BA in Political Science from DePauw University, and a Certificate in International Law from The Hague.