Phishing during the holidays: Why hackers see your employees as opportunities
Trojan horses, DNS spoofing, DDoS attacks, viruses, and worms—these are considered to be tools of the trade for malicious hackers. Yet, one of the first, and arguably most important, tools hackers use to penetrate your organization are people.
According to Symantec, one in 131 emails sent in 2016 were malicious, the highest rate in five years. Phishing attacks (sending unsuspecting people emails with malicious attachments or links) are remarkably effective, and have been the first line of attack from some of the highest profile, state-sponsored cyberattacks to the less noteworthy. Despite significant investments made in security solutions, policies, and processes, hackers still find a way in. Employees are often that conduit; we are all prone to making errors, and attackers understand that we are more apt to act in haste when under time pressure, feeling anxiety or anger, or presented with an enticing opportunity. And despite its many joys, one of the most stressful times of the year is, of course, the holiday season.
How might a cyber attacker turn the season of joy into the land of (their) opportunity? In this article, we will temporarily put on the black hat and present some ways an attacker may use the holidays to gain inroads to the enterprise, as well as discuss some best practices to protect you against these types of attacks and others.
Why the Holidays Are Prime Time for Hackers
During the pre-holiday rush, employees may be more likely to login to personal email and other accounts from work computers to do online shopping or other tasks. Because of the unusually large quantity of incoming emails (order confirmations, shipping updates, and correspondence with friends and family), employees may be less suspicious of unexpected emails. Shoppers have additional concerns from packages that don't arrive on time (or at all), to the fears of identity theft and credit card fraud. Savvy attackers play into these fears to create emotional, knee-jerk reactions in their targets, which makes them less likely to think critically.
Unlike corporate email, which often blocks suspicious links and attachments, personal email cannot be easily filtered for malicious content by the enterprise. Webmail content is typically delivered over end-to-end encrypted communications, such as HTTPS, allowing attachments received via personal accounts to completely bypass the organization's content filters. Malware hidden inside common filetypes such as Microsoft Office documents can be used to execute code on the system while bypassing application whitelisting and other common endpoint protection solutions.
Malware from such campaigns can pose numerous risks to the organization such as allowing the attacker remote access into the corporate network or, in the case of ransomware attacks, encrypting critical files until a ransom is paid for the decryption key.
How We Could Use the Holidays against You: Three Phishing Methods
Social engineering is both an art and a science, and the variety of methods is nearly endless. Below are a few examples that could be exploited during the holidays, but they are by no means comprehensive:
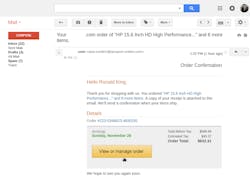
Example #1: I Didn’t Order That! The Unexpected "Order Notification" Phishing Example
By sending the victim a realistic-looking order confirmation, often for a high-dollar purchase the victim knows they did not make, they would be anxious to quickly investigate and rectify the error. In this example:
- No special design skills are required on the part of the attacker. We created this phish just by modifying a real email from a major online shopping portal
- Target domain names from the original email have been changed to the attacker-controlled domain name that closely matches the real shopping portal
- Malware can be delivered either when the victim clicks the link or by including a malicious receipt/invoice as an attachment to the email
- The lightly customized attack may include the victim's first and last name to make the email more convincing. This information is often easy to discover by the attacker and requires only minimal effort to greatly increase the chance of success
Example #2: "Failed Delivery Notification" Phishing Example
This attack example is recreated from a real-world phishing attack conducted by cyber criminals. It plays on the victim's fears that they will not receive their package in time for the holidays (if at all). The malware would be attached as a malicious document or PDF.
Example #3: "Holiday e-Card" Phishing Example
Again, emotion comes into play here, since who doesn’t like holiday greetings? In this attack, we modified a real e-card delivery from a major online greeting card portal.
- Malware is delivered when the user clicks any link within the email. This can include downloadable files or browser-based exploits
- Target domain names from the original email have been changed to an attacker-controlled domain name that closely matches the real greeting card portal
Defending Against These Attacks and Others
It’s an inarguable fact that solutions, policy, and process alone are not ironclad safeguards against breaches. We repeatedly see enterprises heavily invested in such methods getting compromised. These efforts are still needed and such practices and investments must be made. However, in each of the examples above, attackers targeted employees and bypassed organizational email/web filters going through personal email accounts—meaning, your employees are still a significant vulnerability that open a gap beyond your investments. An important key to securing your enterprise is employee education, building a strong organizational security culture. The goal of training must be to develop critical awareness among the employee population using effective and engaging training for each user, followed by realistic phishing and social engineering exercises conducted on a regular basis. Training should have the rigor to teach employees that emails are designed to catch them off guard or evoke an emotional response, and they must always stop, think, and react carefully.
We recommend sending employees reminder emails this holiday season with some anti-phishing best practices: Stop and evaluate emails carefully. Did it catch me off guard? Is it suspicious? Can I get to same information another way besides the email? We recommend accessing the same information directly through an application (rather than the link, which may be just a few characters off of the legitimate address), through a bookmark, a phone call, or through a trusted search engine, saving the company from a potential breach.
Additional Enterprise Safeguards
No matter how rigorous your InfoSec training, there are no guarantees that employees will all heed your warnings or make no mistakes. Every enterprise must have a solid foundation in security best practices, adhered to consistently across the enterprise. Consider these top five additional safeguards:
- Keep all applications up to date and patched. Many of the attacks that have occurred were due to outdated browsers and applications running on the endpoint. Assure all applications on every machine enterprise-wide are up to date.
- Harden your endpoints. Employ a secure configuration of your endpoints and work relentlessly to ensure that every endpoint uses the latest configuration. Avoid making end users members of the local administrator's group, as bad actors look to acquire privileged credentials, and this approach provides them with an easy way to access them. There are a number of solutions on the market that allow the ability to administer a device without enabling this fundamental security weakness. Also, consider blocking access to personal email account providers to improve your overall security posture.
- Deploy signature-based endpoint protection solutions. Deploying and maintaining a signature-based endpoint protection solution is a necessary layer of the defense-in-depth security model. Many of the attack vectors in the wild are known, and resistance can be improved by establishing a good foundation.
- Leverage advanced detection and resistance solutions. Advanced attackers often use zero-day vulnerabilities or new attack vectors where no known signature exists. Using these types of solutions can speed up the ability to detect and respond. The better products on the market enable a resistance capability to isolate the malicious activity to the single endpoint.
- Establish and rehearse your Incident Response Plan. Once malicious attackers are detected, it is critical to quickly contain the threat before they can harvest administrator credentials and crawl your network. Every company should have a robust Incident Response Plan (IRP), with defined processes, metrics, and established roles and responsibilities, to enable your organization to respond, recover, and continue to operate. Rehearse your IRP with all business stakeholders (such as Human Resources, Legal, and Operational Units, e.g., Supply Chain) representing real-world simulations, such as zero-day attacks.
AAbout the Authors: Michael Allen is a Senior Consultant with Coalfire Labs and he can be followed at Twitter: @Wh1t3Rh1n0. Rob Otten is a Senior Director of Cyber Risk Advisory at Coalfire