How to assess whether security outsourcing will work for your organization
While outsourcing to a Managed Security Service Provider (MSSP) has become a fundamental business strategy for many organizations over the last decade to help them achieve a sharper focus on their core competencies and streamline business operations for better cost-efficiencies. But when it comes to cybersecurity, preventing cyber attacks encompasses myriad threat vectors that may cry out for a more strategic approach. Dealing with cyber issues like DDoS protection, intrusion prevention systems (IPS), web application firewalls, data loss prevention, security information and data management requires a thorough risk assessment.
Securityinfowatch.com (SIW) and editorial director Steve Lasky recently discussed this topic with Matthew Rogers, the Global CISO for Syntax. Rogers joined Syntax as the company's Chief Information Security Officer of the Americas in August 2020and in this role works with Syntax's Global Product Management team to develop security solutions for Syntax's global customers. He has designed, implemented and staffed cybersecurity programs and strategies for almost 15 years.Securityinfowatch.com: How should a company decide between in-house vs outsourcing security? What are the factors to evaluate?
Matthew Rogers: Cybersecurity is a specialized skill set that comes with its own specialized tools and software systems that require continuous development and maintenance in order to work without disruption. Companies that lack enough projects to keep their security resources properly engaged and challenged should consider outsourcing these responsibilities.
Hiring a world-class surgeon who typically does four days of surgery a week to only do one operation a quarter will decrease this person's skill set as they fall out of practice. Then, as a result, it reduces their overall value to value to the company. It’s a bad fit for both parties. Security management works the same way. As new threats emerge, any professional that is not regularly monitoring environments and keeping up their practice will lose their skills.
SIW: What should CISOs look for in an MSSP or SOC team?
Rogers: The variation of quality in the SOC or MSSP model is dramatic, and many companies are racing to commoditization while using the lowest skill labor possible. Others are striving for a more specialized, skilled approach. True leaders will share things back to the industry, others will consume those things.
The right security partner should have a proven track record of successful projects and an innovative approach to implementation and carrying out strategies. You’ll want a partner with experience securing and monitoring industry-standard systems, platforms, and applications. For example, can they secure your private cloud, hybrid cloud, SAP and Oracle systems, and Microsoft Office 365? Does their staff have the certifications that are needed to monitor these systems? If your production system goes down and you can’t afford to wait in a support queue or play phone tag with a technician, how easy is it for you to reach the right person if something goes wrong? These questions can help you decide if it's a good fit for your security needs.
Rogers: Losing control is often a fear of business leaders looking to outsource parts of their security. But a partnership with an experienced SOC or MSSP results in no loss of control – more so, a company will gain new capacity and capabilities with the right partner. A good MSP is like having a good lawyer on retainer, invaluable when needed.
Another misconception may be that leaders think the larger their security investments and budgets are, the better protected they are. It’s ill-advised for companies to amass giant arsenals of preventive tools without first putting in place a coherent strategy for what they’re trying to do or even training their people to use the technology they buy. The result is billions of dollars in wasted cybersecurity spending each year. Luckily, outsourcing security can help a company make sure their security investments, whatever they may be, aren’t going to waste.
SIW: How can in-house security teams build a productive partnership with MSSPs and SOCs?
Rogers: The best way to ensure your internal security teams are getting the most out of an MSSP or SOC partner is to give them feedback and ask for advice. The SOC is made up of a group of people trying to protect numerous companies, not just yours, so their people are working on a wide range of complicated security issues. It’s possible that you’ll have a vendor notice before they do (depending on your vendor status), so the more you share, the better you can work with each other to derive value.
Another important consideration to build a productive partnership with a SOC or MSSP is time zones. A business’s security risks increase during the hours that their employees work, so it’s critical to choose a partner that works similar office hours. That way, the SOC will be available to support when a company is at its most vulnerable.
There are undoubtedly several applications that are mission-critical for your business. Many security providers boast experiences securing complex and business-critical SAP and Oracle solutions for their customers, but in reality, their underlying structure is not built on best practices and solid architecture principles. This can lead to poor service levels. Before choosing a security partner, find out what architecture they used to build their solution and where they deliver it from. Also, it’s important to look for a partner that has a solid business foundation, healthy finances, and a plan for long-term growth. This can help avoid any contract or responsibility issues down the line.
SIW: How do you make the argument that it is not just enterprise organizations that need strong cybersecurity protocols when confronted by smaller organizations that can be just as impacted by an attack or a breach?
Rogers: Company size doesn’t mitigate legal requirements to protect confidential data, CUI data, employee data, and the functional systems that support a business. All organizations are required to adhere to new compliance standards, so a security partner can help especially small teams keep up with evolving regulations.
Additionally, the right partner will help small organizations with limited talent seamlessly navigate an ever-changing digital landscape and secure their IT environment for the benefit of supporting your business. By taking the day-to-day management of your environment off your plate, your internal team can spend less time on mundane tasks and more time on projects that drive strategic value for your enterprise.
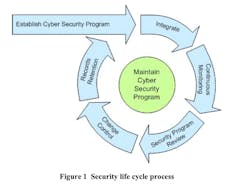
Rogers: A great public document from 2010 published by the NRC titled REGULATORY GUIDE 5.71 has a wonderful diagram describing the lifecycle of a Cyber Security Program – I’ve included the image below. The moral of the story is that true security is never finished. If you’re standing still, you’re falling behind. If a security strategy isn’t adjusted or validated yearly, or even quarterly, you’re absorbing risk without proper acceptance.
The cloud has helped companies quickly scale their environments so they can keep pace with the speed of business. A security partner needs to scale alongside a business partner in order to future-proof their cybersecurity strategies. Enterprises should also look for a partner who isn’t locked into one vendor so that they can use their preferred technology.
About the Author
Steve Lasky
Editorial Director, Editor-in-Chief/Security Technology Executive
Steve Lasky is Editorial Director of the Endeavor Business Media Security Group, which includes SecurityInfoWatch.com, as well as Security Business, Security Technology Executive, and Locksmith Ledger magazines. He is also the host of the SecurityDNA podcast series. Reach him at [email protected].