Navigating responsible facial recognition in the U.S.
The market for facial recognition technologies is expected to more than double by 2028, and each month the list of Fortune 500 brands using the technology grows.
Despite all this, an ever-changing mosaic of state regulations around the technology, in addition to public controversy over specific use cases, is making it challenging for security professionals to understand how they’re able to responsibly and legally use it – and where.
Existing laws in various states around the use of facial recognition are not overly restrictive, and in most cases simply require that consent and data privacy standards are in place. Additionally, integrators and end users considering adoption of facial recognition can take extra steps to ensure the software is being used in the best interest of business and consumers alike.
The following overview of facial recognition regulations is meant for informative purposes and should not be used as legal guidance.
Types of Facial Recognition
As you’d expect, the legal framework around facial recognition use in the U.S. largely concerns the context of the use and the way in which the facial recognition system is actually operating in a public space.
There are two primary categories of use as defined in legislation around biometrics which concerns facial recognition: active and passive.
Active facial recognition requires a consumer’s action to initiate the system scanning and matching your face. Consider mobile payment through your facial recognition-enabled smartphone. It’s not reading your face at all times, but when you click to pay, you’re enabling the system to go ahead and scan your face to verify.
In the case of active facial recognition, once you have initiated the system it should only scan the foremost person in the room, even if multiple individuals are present.
Alternately, passive facial recognition runs in the background consistently and does not require any kind of action or permission before scanning faces. A good example of passive facial recognition would be a system at the airport, scanning all individuals as they pass through security. Multiple faces are being scanned simultaneously and there is no action required to initiate it, it’s constantly running.
All existing state legislation on biometrics permits active facial recognition with varying state-by-state requirements on notice of use and opt-in/opt-out.
Data Handling and Retention
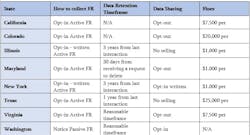
Another important component of compliance with existing facial recognition laws relates to data privacy. Many states with Biometric Information Privacy Acts (BIPAs), such as New York and Maryland, require that data retained by the system is deleted within a certain time period. Similarly, many state regulations prohibit the selling of any data gathered by a facial recognition system.
These standards are incredibly important in ensuring individuals’ data is protected when biometric systems are in use. Additionally, it’s important to note that a variety of facial recognition systems on the market today do not gather or store any photos as they run, making them even safer options.
Here’s an overview of some of the key measures within state-by-state BIPA laws, relating to the use of facial recognition:
Additional Privacy Considerations
While numerous and complicated, the handful of biometric laws in place in the U.S. today are not overly stringent.
In fact, responsible businesses implementing facial recognition should take additional precautions to ensure the privacy and security of their patrons is respected to the furthest extent by the technology. These considerations often come down to software structure and the way the facial recognition system itself operates, which can vary widely.
Consider, does it leverage a database of images gathered through non-consensual mediums such as public social media photos? Does it store photos of faces as it runs? These key questions can differentiate solutions which empower convenience and instill trust with customers, from those that feel invasive.
Here are 4 key considerations you should take into account when evaluating facial recognition solutions on privacy and security:
What FRT Should Never Do
Consent is arguably the most critical concept in the facial recognition ethics debate today, and consent is also at the heart of most legislation being developed around it.
Many consumers want the ability to control when this technology is used on them and what information about them it can divulge to private businesses.
Any solution which operates through the use of photos it does not have consent to leverage should be approached with skepticism. Opt for solutions which come without a pre-installed database, and instead, ask you as the business owner or security integrator to build your own database by entering in photos of consent-providing staff or customers that will interact with the technology.
Facial recognition is not a ticket to know the name of every stranger who enters your store off the street. At its best, it’s a vehicle for convenience, security and personalization for consenting consumers who want it.
What Solutions Should Offer
Solutions which only offer passive facial recognition, or facial recognition which runs constantly scanning all faces in a space, without any kind of initiating action remove the ability for anyone to opt out. Structurally, this software cannot stop itself from scanning any one individual person, it operates by constantly scanning every individual within the frame.
Active solutions have opt-out ability built in because they require a prompt to be completed before they scan. Imagine facial recognition-based mobile payment systems, if you don’t want it to run or you want to opt-out, you simply wouldn’t push the button to pay to have it begin scanning your face.
Once again, consent is a key element.
Regular Software Enhancements Needed
The security space is evolving constantly as new vulnerabilities are discovered and remedied – so too should your software.
Security procedures and data storage should be reviewed twice a year to ensure the latest privacy safeguards are integrated into the technology and it’s not leaving your users at risk of any new threats.
Questions Needed Before Sale
Facial recognition technology is powerful, that’s inarguable. It’s incredibly effective for a vast array of use cases, making it even more important that those use cases are ethical and will actually work well with the capabilities of the software.
Any vendor worth its salt should engage in a serious discussion about your planned use of the technology to both ensure the solution will operate correctly for your use and that it will not be used to unfairly target any individuals or groups.
Using facial recognition technology responsibly entails both abiding by local state and federal guidelines but also taking additional steps to ensure user privacy and security is as protected as possible. Look for partners and vendors who mirror your values and ensure communication and consent are baked into how you implement facial recognition.
Terry Schulenburg is vice president of business development at CyberLink, the maker of FaceMe. Terry’s 35+ years of experience in the technology space include roles at Blackboard, Genetec, Apple and more, and specializations in campus safety and AI security.
About the Author

Terry Schulenburg
vice president of business development
Terry Schulenburg is vice president of business development at CyberLink, the maker of FaceMe. Terry’s 35+ years of experience in the technology space include roles at Blackboard, Genetec, Apple and more, and specializations in campus safety and AI security.