Use Cases for Edge-Based Video Surveillance and How to Keep It Secure
Closed circuit television (CCTV) is what the industry used to refer to video surveillance solutions as. Even today some people (usually those who have been in the industry for decades) will still refer to video surveillance solutions as CCTV systems. The origin of the term is rooted in its analog technology. Typically, there was a system of cameras connected by coaxial cables which transmitted video to a bank of monitors, one camera to a monitor. As the name depicts, these systems were closed loop systems. The camera and monitor were independent of other technology or connections.
Video Through the Ages
The earliest recorded use of CCTV systems was by the German military in 1942 to watch live launches of V-2 rockets.[1] It wasn’t until 1956 that CCTV video was being recorded commercially. [2] However, it wasn’t until the mid to late 1970s that CCTV systems became more commonplace in the non-government space. At the same time improvements in the image, sensors made recording video in low light conditions possible. The following 30 years included improvements in recording solutions with the introduction of the time-lapse VHS recorder and multiplexer which afforded security professionals the ability to record multiple cameras to one VHS tape making for lower cost in infrastructure and faster investigations.
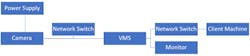
The anatomy of the modern video surveillance solution was relatively consistent from the late 2000s to the late 2010s. A camera, powered by a power supply or Power over Ethernet (PoE), was connected to a video management server (VMS) via a network switch. The VMS had multiple network interface cards (NIC). One was dedicated to the camera network and the other was dedicated to the operational network where the client machine lived. Many physical security integrators preferred building out their own segmented network for multiple reasons. First, it was to avoid working with the end customer’s IT department because they were often met with resistance, and secondly, video transmission over operational networks posed a huge bandwidth issue. Placing too many video streams on a data network would wreak havoc on an operational data network.
By the late 2010s, the adoption of digital video was ubiquitous. It was at this time that the term “the edge” began picking up traction. The edge refers to the technology at the end point of the network. In most cases, it would be a camera or thermal imaging device. Today, the edge includes access control readers, radar sensors, and many other devices which contribute to the aggregation of data.
As solutions become more complex, end users were looking for redundancy for recording. Relying on 24/7 network connectivity came with its drawbacks and critical video was getting lost. Video camera manufacturers began providing SD card slots on cameras for redundant video storage at “the edge” in an effort to mitigate the network issues with large video files requiring so much bandwidth. In addition to using SD cards, tremendous improvements to video compression algorithms and improved bandwidth capabilities of network switches allowed more cameras to be placed on networks at higher resolutions.
Today we see many driving forces for transitioning much of the technology we traditionally saw at the head end to the edge. Improvement in processing power in edge technology has created an opportunity to add video analytics to edge devices alleviating the need for separate servers. In the case of more process-intensive analytics, shared processing between an anality appliance and the edge device also lowers the cost of the appliance.
Benefits of Pushing It to the Edge
Pushing recording and processing to the edge has several benefits. There is a reduction in infrastructure costs. Processing analytics and recording at the edge are faster and reduce the need for greater storage and bandwidth at the headend. There are fewer or no servers required which also reduces the carbon footprint. With processing done at the camera, the system is also far more efficient.
With the reduction of servers and network infrastructure edge processing affords, there is also a lower cost for maintenance of the overall system. In the traditional configuration of centralized recording, if the server went down, all of the devices connected to that server were offline. By pushing the processing and recording to the edge there is less downtime. If a camera goes down, it is only one device out of many. Fewer devices on the network also reduce the attack vector from a cybersecurity perspective.
The improvement of edge device processing power also creates an affordable means for business intelligence. Utilizing existing infrastructure from traditional security cameras to implement analytics that will provide actionable business intelligence improves ROI for the overall solution. Additionally, analytics can be licensed at the device level rather than using blocks of licenses on servers.
Finally, there is a future-proofing element to push it to the edge. Implementing edge solutions provides a means for transitioning towards cloud adoption of video surveillance. Although many argue that video surveillance in the cloud is not yet mature, hybrid solutions are already available to take advantage of on-premise and cloud solutions. With recording taking place at high resolution and framerate on the edge device, hybrid solutions take advantage of low-cost cloud storage options for offloading video for archiving purposes.
Use Cases for Edge Video Surveillance
There are several significant use cases for edge video surveillance solutions. Some organizations have limited IT resources to manage and maintain servers and device lifecycle. Without complex servers to maintain, edge solutions provide an excellent alternative to the traditional surveillance environment that is often maintenance intensive. Additionally, with the right infrastructure engineering, many manufacturers will offer the ability to automatically push firmware updated to edge devices ensuring that they are not posing a threat to the network by using out-of-date firmware.
In the case of remote sites, using edge surveillance solutions provide an excellent opportunity for capturing video without a large investment in hardware and infrastructure. All that is required is a camera with an SD card, power, and network connection if remote access is necessary. This is an extremely cost-effective option.
As mentioned earlier, processing video at the edge reduces the bandwidth requirements for the overall system. Storing at the edge at higher resolutions means that live video can be viewed as thumbnails until activity is detected, which can also significantly reduce infrastructure requirements.
When Do Centralized On-Prem Solutions Make More Sense?
Although edge video surveillance solutions seem like the next greatest trend in security, it is not a one solution fits all situation. There are scenarios in which edge solutions are not practical. For example, if an organization does not need cameras with edge analytics capabilities, they could select a camera with lower processing power and maintain an on-premise server, reducing the cost of the total solution.
In addition, many of the manufacturers that offer edge solutions are proprietary in nature. The end user is required to use the manufacturer’s end-to-end solution. This limits the end user when it comes to using “best in breed” integrated solutions. The industry has gotten used to VMS solutions that are agnostic to camera manufacturers and the ability to select from a variety of technologies without getting locked into any one solution.
There are also some highly regulated environments that do not permit any devices to be connected to the Internet for cybersecurity purposes. In these cases, edge solutions are not an option. Traditional server-based on-premise solutions are a natural fit for these applications.
There’s a Solution for Everyone
Whether your organization is looking to adopt the latest in cloud computing or to just dip a toe in the water with a hybrid solution, there is a system out there for everyone. One of the most exciting things about being in the security industry today is the new and creative ways in which security solutions are being implemented. Video surveillance is no longer simply a cost center but is now being used as a source of business intelligence, marketing and customer experience purposes with the addition of analytics. Utilizing edge processing will no doubt continue to drive innovation in the security industry for years to come.
Footnotes:
[1] http://scihi.org/walter-bruch/
[2] https://www.verizon.com/business/small-business-essentials/resources/edison-internet-history-video-surveillance-105000047/
Drawing on her more than two decades of experience, Antoinette founded Credo Cyber Consulting in 2020 with the goal of providing her clients a holistic perspective on a cyber-physical security program with a focus on data privacy and protection. Antoinette is a Board-Certified Physical Security Professional (PSP), as well as a certified Data Privacy Protection Specialist (DPPS). She has an associate degree in Criminal Justice, a Bachelor of Science in Managing Security Systems, and a master’s degree in Cybersecurity Policy and Risk Management.
KAYLA: CAN YOU GIVE THIS A BOXED 3-D TYPE OF EFFECT FOR THE SIDEBAR?????
10-Steps to Securing Edge Devices
Here are some steps that can be taken to harden edge devices:
1. Conduct an annual risk assessment – Knowing your risks is the first step in addressing them
2. Consult the hardware manufacturer’s device hardening guide – the manufacturer should provide you with a detailed hardening guide for their product.
3. Identify all connectivity to your devices –
a. Are your devices connected directly to the Internet?
b. Is there a firewall?
c. Is there an alternative way to connect to your devices through the production network?
d. Do you employ network segmentation?
4. Create and implement a user policy –
a. Not all users need the same privileges
b. Not all users need access to all devices
c. Be sure to have a process to remove users if they no longer require access
5. Create and implement a password policy –
a. Require strong passwords for each account on the device – DO NOT USE DEFAULT USER ACCOUNTS AND PASSWORDS
b. Do not use the same password on every device
c. Use a password vault to store passwords securely
6. Create and implement a lifecycle management process –
a. firmware updates – always ensure your device is operating on the latest firmware
b. Hardware lifecycle program (End of Life/End of Support)
7. Disable all processes that are not necessary to operate the device –
a. ftp
b. audio
c. any other service or process that is no needed
8. Enable secure communication –
a. Whenever possible enable HTTPS to ensure that the data in transit is secured.
b. Use signed certificates whenever possible
c. DO NOT USE PORT FOWARDING
9. Enable encryption of the stored data whenever possible.
10. Block inbound traffic to the device whenever possible
About the Author

Antoinette King, PSP, DPPS, SICC, CMMC-RP
founder of Credo Cyber Consulting, LLC
Antoinette King has over two decades of experience in the security industry, with a focus on integration, manufacturing, and consulting. Antoinette founded Credo Cyber Consulting in 2020, with the intention of providing her clients with a holistic perspective on security, bridging the gap between the physical and cybersecurity domains, and focusing on data privacy and protection. Her first book, The Digital Citizen’s Guide to Cybersecurity: How to Stay Safe and Empowered Online, hit the Amazon Best Sellers list for all its categories in the first 48 hours of release. Her latest book, co-authored with Michelle Kreiger and released in October 2025, is From Chalk Dust to Digital Trust:
A guide in Data Privacy and Security for K-12 Leaders was #1 in Cloud-Based Computing books in the first week of release.