Intelligent physical security system devices—especially AI-enabled video cameras—have become high-value targets for hackers, who now deploy malware explicitly designed to infect these devices and lie dormant until the right opportunity arises to exfiltrate data, disrupt operations, join a botnet, or spread deeper into the network.
Q: What should I do about the fact that my physical security system devices, especially those with AI processing capabilities, are now a primary target for hackers?
A: The most critical approach, encompassing a coordinated set of measures, is for IT and Physical Security teams to establish and maintain a securely managed zero-trust physical security system network.
This approach is critical as the number of AI-enabled cameras and sensors in enterprise environments continues to surge, each representing a potential entry point for cyber threats. A zero-trust network ensures the integrity of security data that increasingly informs business decisions, from retail analytics to workplace optimization. However, implementing Zero Trust networking for physical security systems across a large enterprise can be more challenging than necessary without a clear understanding of the organizational and technological contexts.
The exponential advancement of technology has created a watershed moment for the physical security industry—a dividing line after which security system design, deployment, and management have undergone fundamental changes. Historically, many security teams have relied on IT for network design and security, as well as for implementation. Over the past two decades, business computing, Ethernet technology, network architecture, and physical security technology have undergone significant transformations, necessitating a new approach to IT-security collaboration on Zero Trust for security system networks.
IT’s Evolving Landscape
- Enterprises now rely on cloud software platforms rather than on-premises solutions.
- Paper workflows have largely vanished; employees use myriad cloud applications and cross-platform workflows.
- Securing networking and tightly controlling access to cloud applications are top IT priorities, as data and applications shift to the cloud while BYOD devices remain dispersed.
- The number of on-site computers IT manages has decreased, but its end-user population has grown significantly.
- Security devices have proliferated across corporate networks, but most lack sufficient security or management to safely reside on or connect to these networks.
Security’s Technological Shift
- For enterprise-caliber security systems, value growth lies in the scope and utility of security operations enabled by front-end software and integrations, rather than just the number of devices (e.g., readers, cameras) that can be supported.
- Cloud-based security platforms are proliferating because cloud data centers’ processing power far surpasses on-site computing, especially for AI’s parallel processing needs.
- Large enterprises manage hundreds to thousands of intelligent devices — cameras or control mechanisms like door locks, not end-user devices.
- Over the past two decades, the use of security devices has grown tremendously. The emergence of AI-enabled devices and the increasing business value of security data will likely continue to drive the deployment of devices at sites, thereby enhancing business network connectivity to these systems.
- Security system end-users remain few, typically a few to a dozen or so security personnel per site. Facility occupants primarily interact with devices like card readers and intercoms, but expect simpler, faster, and more reliable performance due to consumer technology standards.
Physical Security Zero Trust Implementation Challenges
Why can’t security teams rely on IT for Zero Trust guidance? IT faces immense pressure to transform complex infrastructures while maintaining business continuity, operational integrity, and cost-effectiveness. Five developments have reshaped IT operations, straining cybersecurity resources:
- Advanced AI Models: New AI models enable real-time parallel processing of vast data streams, accelerating AI training time, and enabling faster and more adaptive decision-making and integration capabilities for cloud-based applications.
- Automated Data Centers: Advanced computing hardware and orchestration software have driven highly automated—and in some cases autonomous—data center operations, reducing large-scale computing costs.
- IT-OT Convergence: AI-enabled devices and Ethernet networking blur the boundaries between IT and operational technology (OT), with new long-range Power over Ethernet (PoE) technologies reducing the cost and complexity of industrial and physical security system networking.
- Automated B2B Transactions: Increased inter-platform data exchanges introduce new IT infrastructure risks and complexity.
- Expanding Attack Surface: Surging cyber threats demand proactive, automated defenses.
Applying Zero Trust across enterprise networks is more complex for IT than for security teams. Security networks are smaller, contained, and operate as closed systems with few integration points. Unlike corporate systems that support dynamic user populations, security environments are generally stable, with devices like cameras often lasting a decade. This makes Zero Trust implementation for security networks different from, but also more straightforward than, Zero Trust for corporate business system networks.
The Slow Adoption of Zero Trust Networking
Despite its importance, the adoption of Zero Trust in enterprise IT remains slow. A 2023 Gartner press release notes that few organizations have completed Zero Trust implementations, predicting only 10% of large enterprises will have mature programs by 2026, up from less than 1% in 2023. This reflects the complexity of enterprise IT, with legacy systems and diverse technology stacks
Given IT’s focus, it is expedient for security teams to lead Zero Trust initiatives for the security system network, collaborating with IT for support. That said, IT’s supporting role is still critical and includes the following collaboration focal points:
- Identifying network infrastructure (e.g., switches, routers) supporting segmentation and authentication, including Modern LAN technologies (described on the following pages).
- Determining device- and network-level authentication measures, such as strong device passwords and unique logon credentials for each device.
- Leveraging enterprise-approved Certificate Authorities for authentication.
- Align on identity management practices for security system user interfaces.
- Selecting a Cyber-Physical Systems (CPS) protection platform to automate attack surface hardening, including password and certificate management, firmware updates, and monitoring.
Zero-trust network designs are most effective when they accurately reflect the real-world network usage of the systems they are meant to protect. Physical Security teams and their technology service provider partners are the ones who understand the usage of security systems and their network requirements. Thus, they must prepare for and drive the Zero Trust initiative.
A practical resource for examining network usage in the context of modern networking technologies is the free eBook Future-Ready Network Design for Physical Security Systems. The book takes a closer look at Zero Trust for physical security systems, networking and also examines the requirements for an enterprise-caliber physical security system CPS protection platform.
Zero Trust Basics
Zero Trust is a cybersecurity approach — not a product — that assumes no device, user, or system is inherently trusted, whether inside or outside the network. Trust is continuously verified through authentication, authorization, and health checks. Its principles suit security systems due to their predictability and limited scope.
1. Never Trust, Always Verify—Assume Breach
No device or user is trusted by default; every action requires verification. Networks are designed to limit harm if a device is compromised, assuming a breach may already exist.
2. Device Identity and Network Integrity
Connections require verified identities, with encrypted data to prevent eavesdropping or malicious traffic. This involves:
- Authentic digital certificates for all devices and systems.
- Certificate-based encryption using strong standards.
- Mutual authentication between devices making a connection is a cornerstone of Zero Trust.
Vendors such as Avigilon, Axis Communications, Hanwha Vision, and Bosch support mutual authentication (see their product documentation and hardening guides, e.g., the Axis Hardening Guide). Security teams must collect product hardening guides and device network security specifications to prepare for collaboration with IT.
3. Microsegmentation
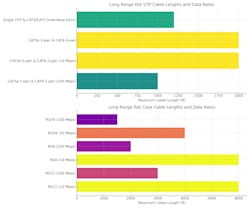
Networks are divided into isolated segments (microsegmentation) by function, thereby limiting the potential spread of threats. For example, card readers and controllers are grouped separately from cameras. VLANs often isolate video traffic, a common practice. Microsegmentation supports Industrial IoT Ethernet, a Modern LAN practice that reduces costs. Access control devices, with lower bandwidth requirements, are well-suited for long-range Ethernet segments.
Modern LAN enables cost-effective Zero Trust over long distances, using long-range Power over Ethernet (PoE) with standard unshielded twisted pair (UTP) or reused coaxial cabling. The tables below show supported cable lengths and data rates.
4. Least Privilege Access
Devices and users receive minimal access necessary for their functions, which is already a standard practice among leading security teams.
5. Continuous Monitoring
Devices and users are continuously evaluated for compliance with expected behavior, firmware versions, and configurations, with device errors or deviations indicating potential security compromises (e.g., malware, hacking attempts).
6. Incremental Implementation
Zero Trust is not an all-or-nothing approach. It can be deployed in stages, starting with simple network segmentation and device isolation. A practical starting point could be to create isolated VLANs for cameras, access control systems, and intercoms. Then restrict device communication pathways and implement authentication at key connection points. Most existing infrastructure supports this.
In any existing physical security system deployment, the degree of device and application support for Zero Trust networking will vary, partly based on the age of the products deployed. A key step for Security teams in preparing for a zero-trust collaboration with IT is the inventory and assessment of the physical security system software and hardware landscape, including product age, warranty, and other product lifecycle information.
Zero Trust Advocacy
Physical security professionals need not be Zero Trust experts, but should advocate for it, defining their systems’ overall network design and usage. IT can assist with certificate infrastructure, cybersecurity details, and tasks such as switch and router configuration (if not outsourced to a technology service provider), as well as network validation and testing. But security teams and partners must lead design, ensuring alignment with the system functionality on which site security operations depend.