Real words or buzzwords?: AI and automation
Editor’s note: This is the 65th article in the “Real Words or Buzzwords?” series about how real words become empty words and stifle technology progress.
The domain of physical security has existed since the early days of humanity. The electronic physical security industry essentially came into being when electronic device capabilities emerged that were useful for physical security purposes.
The electronic physical security industry’s technology evolution has followed the evolution of business information technology (IT), and the evolution of computer-controlled machinery and equipment. Thus, as IT advances, so does physical security technology.
Physical Security Industry Advances
Many of the physical security industry’s leading companies have come from IT domains outside the physical security industry.
In spite of many nay-sayers – including security industry pundits who asserted they could not be successful – these companies grew to become dominant industry leaders.
Well-known examples are Lenel Systems, Milestone Systems, Axis Communications and Eagle Eye Networks. Their company stories are about founders from outside the security industry who used business information technology to vastly improve security product capabilities in key categories.
These situations are about to be repeated again, but with much greater effect due to the state of two major IT megatrends.
The Two Major IT Megatrends
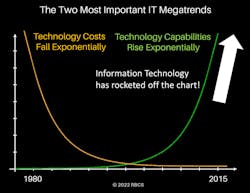
It is a well-proven but little-known fact that all information technologies follow the same two exponential trends. Technology costs fall at exponential rate. Technology capabilities rise at a corresponding exponential rate. See Figure 1 below.
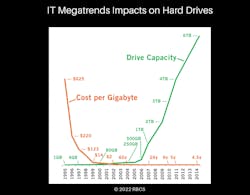
Thus, in the 1980s and 1990s, electronic physical security technology improved only slightly (the green line), while technology costs continued to fall dramatically over the same time period (the gold line). For an example of these two trends, see Figure 2 regarding the impacts of these trends on hard drives.
A Form 10-K is a comprehensive report filed annually by a publicly-traded company about its financial performance and is required by the U.S. Securities and Exchange Commission (SEC). In late 2018, Seagate reported in its Form 10-K that hard disk price erosion was a significant risk to the company, citing that in the previous 2 years storage pricing had fallen from 3 cents to 2 cents per gigabyte. That’s a 33% drop – and the trend is still ongoing. This is why the cost of video surveillance hard drive storage is no longer an issue, when it used to be a major constraint.
This is representative of the impact of the two IT megatrends on all physical security system information technology elements. The cost per measure of technology capability remains low, while the measures of technology capabilities are skyrocketing.
Security System Performance
Constraints are Disappearing
Until now, security systems deployments were constrained in two ways: security device and system shortcomings and high product costs. That’s the story of the previous 50 years of electronic security technology, where technology costs were relatively high and technology capabilities were improving only incrementally.
Now we’re at a historic point where that situation is reversing. From now on – if we apply emerging technology correctly – we’ll be achieving never-before-possible security system capabilities.
Using AI-enabled emerging technologies to automate many security operations actions, we’ll be able for the first time to accomplish two important things:
- Effectively utilize large-scale security system deployments easily.
- Move from a reactive risk management posture to a proactive one.
Previous technology capabilities, including two generations of video analytics, that have kept security operations capabilities primarily in a reactive and after-the-fact mode, limiting situational awareness to “what has happened” instead of “what’s unfolding now” and “what’s about to happen.” Security operations is most often running in “catch-up” mode.
Existing security deployments do include many more security monitoring and control devices than in the past and can collect much more information than ever before. But that information that hasn’t been digestible by humans at the scales of the deployments.
The more security situations and incidents there are, the further behind the security personnel get. Additionally, the cost and limited capabilities of earlier generations of technologies still haven’t enabled end-user customers to solve the age-old access control problem of tailgating.
Game-Changing Technologies
Our intelligent devices and platforms haven’t been intelligent enough, until now. We’ve now reached a physical security industry watershed moment, in which exponential information technology advancement – fueled by artificial intelligence and automation – has brought us to the point where we’re making a complete break in security technology capabilities from the products and deployments of the past.
It has been hard to see but now the evidence is appearing. The next 10 years of physical security will be a radical transformation from the previous 50 years.
These major technology breakthroughs are coming from outside the physical security industry, as is the funding for many of them. The funding is performed by firms who understand the value of well-engineered AI, and who have the ability to evaluate the knowledge and capabilities of the AI engineering teams involved.
These firms can accurately assess the business risks as well as the business potential, allowing them to provide greater funding than traditional security industry sources typically provide to startup companies. Such funding is enables startup companies to utilize highly talented product engineers – expert in AI and automation – in greater numbers than traditional security companies have ever staffed product development.
One such company is Ambient (ambient.ai). Backed by a16z and other venture capital firms, Ambient’s computer vision intelligence platform has incorporated powerful video-based AI tools into its patented physical security solution. The company addresses with its enterprise customers some of the most pervasive and stubborn physical security issues, including tailgating and persons brandishing weapons.
Ambient’s rapid growth and success – doubling its customer base year-over-year – has surprised many within the industry. They now boast a number of Fortune 500 companies as customers, as well as six of the largest tech companies in the U.S.
Proactive vs. Reactive Security Operations
Proactive security involves early real-time detection of potential incidents, instead of belatedly discovering incidents that have already taken place.
It means being able to respond instantly to what is detected, to prevent escalation, and then taking precision control actions that provide maximum safety to people and material assets while minimizing risk and danger.
Proactive security means monitoring, protecting, and autonomously acting and reacting constantly, with a solution that does not get distracted or tired.
This requires a kind of precision control at any scale the likes of which we haven’t been able to achieve because the actions required are beyond human capability to perform quickly enough.
The more devices there are to monitor and control (the more cameras and doors, for example), or the more individual attackers there are to deal with (such as a team that splits up to move through multiple hallways and into multiple areas), the sooner the limits of human-only response are reached.
Today’s attackers know the limitations of today’s security deployments, and the Internet’s dark web makes such knowledge available to anyone who wants it.
AI and Automation
Proactive security requires both AI and automation, to a degree that has not been possible until now.
For example, lockdowns have been available only for groups of doors, because individual doors couldn’t be manually managed quickly enough to react to perform such actions in real time. If we have to track multiple intruders simultaneously, manual lockdown of individual doors simply isn’t feasible.
However, AI that tracks the location intruders in real time can use rules-based automation to perform precision lockdowns that protect people and provide only exit paths to the intruders regardless of their number and locations.
AI can simultaneously plan evacuations that move people away from areas of danger with complete certainty of orchestrating the right moves and verifying in real time as they happen.
AI can populate an incident-specific dashboard of status information that can be instantly digested by human operators. AI can notify police of intruder locations, provide live video feeds of those locations, without the need for at-risk human observers.
Advanced AI-enabled security system capabilities can prepare response actions that humans can then initiate – specific actions that people wouldn’t be able to perform otherwise.
An example is to trigger cell phone notifications to certain individuals, not just groups, and engage directly with individuals who have information to report or questions to be answered based on their real-time locations, or their specific skills or training.
AI can’t give human comfort, and it can’t act on needs that arise beyond the AI’s scope. But AI can evaluate an entire field of response and timely inform humans when such actions are needed.
AI systems and automated systems require human involvement to account for unpredicted factors and unplanned-for situations, and to make judgements and take action for situations that go beyond the intended scope of the AI or the range of automation capabilities.
Having proactive security capabilities changes the way we can approach security officer post orders and SOPs for security operations centers, as well as personnel selection and training.
The ability to detect security and safety incidents with nearly zero false positives means that organizations can staff for true event workloads as opposed to staffing and servicing for the typical false positive alarm volumes.
Some security staff can now be repurposed toward more highly skilled work, a long-held goal of the physical security industry.
The traditional security mission of “Observe and Report” can be achieved more effectively using AI-enabled computer vision solutions through greater automation of SOP’s and the ability to monitor results against service level agreement (SLA) requirements.
Organizations that have traditional patrol or static security officer posts with high turnover, or that face increasingly difficult recruiting challenges, can attain a more stable and effective security officer force with less personnel risk, while improving security and safety programs.
Data-Centric Design
Security system design that maximally and smartly uses AI, automation and human involvement goes way beyond traditional device placement and facility hardening thinking. Previous design thinking has been product- and system-centric. Now it can be and must be data-centric.
Security design thinking must now consider how to enable preventive actions as well as response and do so at any scale and for any combination of risk situations and incident activities possible.
It must determine what kind of data are needed to fuel AI functions, and that what data AI functions must generate to properly trigger automation rules, and to fully inform human participants.
Security systems design must include dashboards that can convey real-time status of risk situations and unfolding incidents in a way that is instantly comprehensible to human operators, with the capability to share just the right information to any or all stakeholders.
Systems can be designed so that if data generated by or for AI and automation is complex, the data produced for humans is still simple, insightful and instantly actionable at the human operator level.
We have never had the need, the possibility or the responsibility to design data-centric security systems until now.
This article is the first in a series of articles that will delve into what kind of new thinking regarding people, process and technology is required for emerging new products and systems enabled by AI and automation.
Ray Bernard is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s Top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon. Follow Ray on Twitter: @RayBernardRBCS.
About the Author

Ray Bernard, PSP, CHS-III
Ray Bernard, PSP, CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon. Ray has recently released an insightful downloadable eBook titled, Future-Ready Network Design for Physical Security Systems, available in English and Spanish.
Follow him on LinkedIn: www.linkedin.com/in/raybernard.
Follow him on Twitter: @RayBernardRBCS.