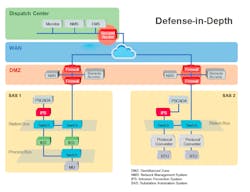
Are our substations safe from cyber attacks?
To answer the call for a future with net-zero carbon emissions, the global energy industry is embracing the digital transformation of the power grid. Consequently, all data must be digitalized and connected. However, where there is data, there is a chance of it being hacked. In most countries, the energy flow and information/data flow of substations are separated. Substations today mainly execute electricity transmission and distribution. Yet it is foreseeable that both energy flow and data flow will be delivered through substations soon. That is why substation automation systems (SAS) will then take an important role in facilitating energy distribution and why it is so critical to protect SAS from cyber threats.
Securing The Digital Power Grid Is National Security
In today’s world of highly connected systems, the power grid, too, is connected to a myriad of digital networks. Substation automation has become a textbook example of OT and IT convergence, as monitoring or control by Supervisory Control and Data Acquisition (SCADA) systems and other applications automate repetitive and error-prone work, relieving the burden of constant human inputs. Despite these benefits, digitalizing the power grid also introduces new risks should system integrity be compromised by cyberattacks.
In April 2022, two months after Russia invaded Ukraine, the Ukrainian government revealed that its largest electricity utility averted a serious cyberattack that would have caused a blackout for two million people. Cybersecurity researchers point out that hackers attempted to deploy Industroyer malware against high-voltage power substations in Ukraine as well as deploying several destructive malware types, including CaddyWiper. CaddyWiper, a variety of wiper software, was spread around Ukraine by hackers in order to delete data on infected computer systems. The lessons from Ukraine serve as yet another cautionary tale for governments, regulators, and power utilities to act now and catch up with rising cyber threats. In war as well as in peacetime, protecting critical power infrastructure should always be a top national priority.Cybersecurity Guidelines for Substation Automation
For this reason, governmental organizations, such as the North American Electric Reliability (NERC) and even the European Union (EU) are requesting more cybersecurity regulations and guidelines for power grid utilities. For example, in December 2022, NERC announced a new “Security Integration Strategy” and the EU released its Network and Information Security Directive 2.0 (NIS 2.0).
Although new regulations continue to be developed for the industry, from a network security point of view, these regulations focus on addressing the following three challenges to securing power grid automation systems:
1. Visibility of Critical Assets
Substation automation systems consist of a wide variety of configurable and controllable components, such as protection relays, power meters, HMI, controllers, and network devices. These critical assets from different suppliers do not offer an easy or uniform management platform, leading to poor asset visibility. Vulnerabilities, if present, are not easily detected and are prone to be exploited by hackers, cybercriminals, or cyber terrorists. That is why it is important to regularly update the firmware or install security patches as part of routine maintenance. If possible, choose vendors that have a Product Security and Incident Response Team (PSIRT) that could help you to identify potential flaws and deliver the latest security patches.
2. Access Control
Even if physical access control stays robust, inattentive logical access control policies or management practices may expose the system to risks. Third-party vendors may have security standards that are not aligned with those of the system operator, or OT personnel unfamiliar with IT may have inadvertently made incorrect settings or erroneously granted access to illegitimate users. As a result, it is important to cooperate with both internal and third-party operational teams to align with the maintenance guidelines and security settings of the relevant system equipment and software.
3. Proactive Security
Firewalls may protect critical assets within a defined security perimeter, but external cyberattacks increasingly exploit remote access, which is a common weak point in modern digitalized electricity distribution systems. Proactive protection that includes consistent monitoring of communication patterns and effective detection of possible cyber threats is necessary for engineers to protect their power systems in today’s threat landscape. Consider a new generation firewall (NGFW), which includes an advanced intrusion protection system (IPS) and intrusion detection system (IDS) to detect suspicious and abnormal communications.
Summary
There is no perfect cyber threat-free solution to secure substation automation systems. But understanding the key challenges and operations with best practices could help minimize the risk and improve the resilience of the entire power grid.
To learn more about how Moxa can help protect your substation automation system, download the Moxa white paper "How to Protect Substation Automation Systems From Cyberthreats."
About Moxa
Moxa is a leader in edge connectivity, industrial computing, and network infrastructure solutions for enabling connectivity for the Industrial Internet of Things. With over 30 years of industry experience, Moxa has connected more than 71 million devices worldwide and has a distribution and service network to serve customers in more than 80 countries. Learn more at www.moxa.com.