Editor’s note: This is the 55th article in the “Real Words or Buzzwords?” series from SecurityInfoWatch.com contributor Ray Bernard about how real words can become empty words and stifle technology progress.
Future Vision
Compared to how we need to be thinking, our current approaches to security technology are like to trying to drive down a freeway by watching the rearview mirror. It won’t get you where you need to go. But what I just described couldn’t happen. By driving in the rearview mirror you’ll never end up on a freeway, as once you get out of the driveway or parking space and onto a street, you’re not likely to get far.
The only way to drive is by looking forward and glancing at the rear-view and side mirrors to maintain an adequate mental map of what’s happening on the road. Rear-view and side mirrors are great assets when backing into a parking space, parallel parking, and backing out of a parking space.
Obviously, this analogy has limits, but it helps me to emphasize the fact that looking forward is what allows us to get somewhere as opposed to remaining stuck where we are.
The Biggest Challenge
The biggest challenge of exponential technology advancement is not the deployment and operation of advanced technology. That gets easier the more advanced the technology is. A good example is Calipsa’s cloud-based false alarm filtering video analytics platform. It takes less than five minutes to apply it to a single camera, but only if you need to outline the areas in the camera where people or vehicle motion is meaningful alarm-wise. Otherwise it takes seconds. This is possible because no additional equipment is needed, and it uses existing capabilities of the camera or VMS. In short order you have eliminated 90% to 98% of false alarms for the cameras where that matters.
This wasn’t possible just five years ago, but you can see why leading alarm monitoring services are using it today. It’s now become available for any organization with security video cameras.
Deploying and using this and other advanced technology is not the challenge. The challenge relates to our design thinking.
Primary Design Thinking Flaw
The primary flaw in our design thinking today is not thinking broadly enough. We still think primarily about responding to intrusions, access violations and detecting early stage prohibited behavior using machine-learning based video analytics. And we certainly can’t ignore those use cases.
However, in a modern organization any business unit must consider all the ways that it could advance the company mission, including non-traditional ways. That applies to the corporate security function as well.
Only a few leading security integrators are thinking along those lines, as I mentioned in my recent article for Security Business magazine titled, AI Readiness as a Service. About 50% of business digital transformation initiatives have already reached the point where they are considered successful in terms of improving business results. However, physical security has only been included in a few of those initiatives.
I asked Eric Yunag, Convergint’s VP of Technology & Innovation, about the potential importance of company digital transformation initiatives. He told me that he spent the previous year talking to customers about such initiatives, to gain an understanding of their dynamics, including their success factors. Eric explained, “As we advise some of the more forward-thinking customers, we think about what digital transformation, AI and computer vision mean to their businesses in a broader context.”
Yunag further explained that he asks these customers: What if you and your smartest people could stand here 24/7/365 and observe what goes on and log it to achieve full insight into the behavior and activities over time, and how would you optimize or better understand your most important customer or employee processes? “We know we are just scratching the surface on how we would turn those observations into data, how we would act on those insights, and ultimately the value that creates for customers,” Yunag says. "That’s the kind of discussion that company leaders want to have about digital transformation and how we can make the case for additional investment in visual intelligence infrastructure.”
Deon Chatterton, former Senior Manager of Corporate Security Technology for Cisco Systems, calls the emerging generation of AI-enabled video systems “enterprise video,” because the information generated by such systems is of value to many functional areas of a business, not just security.
Yunag adds, “While I am not saying such discussions are highly fruitful every time, there is always value in having them. Sometimes it is immediate, sometimes it pays off further down the road.” Such discussions enable security practitioners to think creatively and productively about non-traditional values that electronic security could provide, including visual intelligence derived from facility video.
Thinking Exponentially
There are two IT related megatrends that are fundamental to thinking about exponential technology advancement. The first is technology advancement, an upward trend, and the second is cost reduction, a downward trend. What’s important to know is that the previous unfulfilled promises of video analytics are now becoming possible, and the previously unaffordable technology deployments are becoming affordable.
In previous decades, the cost, complexity and difficulty of electronic security technology deployments was the primary barrier to achieving desired results. Today, the primary barrier is the shortcomings in our thinking.
What Is Exponential Technology?
It is a little known but provable fact, that all information technology advances follow the same type of growth curve. It starts out slow, starts to build, and then takes off like a rocket.
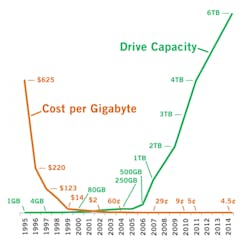
A number of individuals have closely examined these technology trends. Chief among them is Ray Kurzweil, a highly accomplished inventor, futurist and author. In 2012, Kurzweil became the Director of Engineering at Google. About technology advancement, Kurzweil says, “. . . if a technology is an information technology, the basic measures of price/performance and capacity (per unit of time or cost, or other resource) follow amazingly precise exponential trajectories.”
The two hard drive cost and capacity trends are well-illustrated by plotting out the cost and capacity trends of computer hard drives, shown in Figure 1 below. I created this diagram in 2015 for an article in Security Technology Executive magazine.
Figure 1. Hard drive exponential trends.
According to the Fiscal Year 2020 Summary section of Seagate’s 2020 Form 10 K report, the price of hard drives had just fallen from 3 cents per gigabyte in to 2 cents in two years’ time. And we still have to remember that the two IT megatrends of falling prices and rising capabilities are still accelerating.
The impact of these technology advancement trends on security video surveillance is that today affordable enterprise video storage systems measure their capacities in tens or hundreds of terabytes, and soon that will become petabytes (1,000 terabytes).
The computer processing required for deep learning-based video analytics exceeds what legacy video servers are capable of. However, such processing capability is available now from Dell, for example, both on-site and in cloud-based systems.
Stop Thinking About Technology
Even though this article has been discussing technology advances, the most important think we can do is stop thinking about technology itself. Current and emerging technology is affordable enough and capable enough that instead, we should be thinking about use cases. Instead of taking pride in the size of the security technology deployments they achieve, integrators, consultants and security practitioners should take pride in the use cases that their systems support.
What uses of the technology bring the greatest value to the business? That is the key question and the primary focus of attention. Today’s most valuable use cases involve three elements:
- Data collection
- Data integration
- Data correlation and analysis
This applies to real-time applications, such as live responses to in-store customer behavior via mobile app instant offerings and human staff response, and trend discovery and tracking. What kinds of data can electronic security systems and devices provide? How can that data be correlated with other data to provide actionable insights?
Organization stakeholders include a variety of functional areas plus IT Data Governance – whose responsibilities include discovery of data valuable to the business and making sure that the business makes maximum use of that data. Conversations with folks having data governance responsibilities can be very informative, and it’s their job to help functional areas explore potential data value opportunities.
Initially It’s a Learning Experience
For the first time in history, both technology trends and business trends are making it increasingly more feasible for security practitioners to participate in AI-enabled and data-driven organizational advancement occurring across all functional areas.
At the start, it is a learning experience for security practitioners, who can benefit from the lessons learned and insights gained by the progress to date of digital transformation initiatives. Given that most practitioners are already fully tasked, it is a realistic expectation that learning about the work of data governance and gaining knowledge about the expanding roles of analytics and automation in the organization, could easily take a year or more of progressive discussion and discovery.
At some point in that process, possible use cases will start becoming apparent for electronic security technology and devices, and their data integrations, to provide actionable business information in big and small ways. This will accelerate as technology continues to advance, and as successes are shared through security and industry associations and their communities, as well as personal networking.
It is exponentially advancing information technology – with which we build and expand our electronic security systems – that is making it possible for business security functions to become a larger participant in providing value that forwards the business mission.
About the Author:
Ray Bernard, PSP CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s Top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon. Follow Ray on Twitter: @RayBernardRBCS.