Guidelines for the Use of PIV Credentials in Facility Access
As the SP 800-116-1 states, “…this recommendation provides a technical guideline to use Personal Identity Verification (PIV) Cards in facility access…”. Unless otherwise mandated compliance with this publication is recommended. However, the overarching mandate to use a PIV card for physical access to Federal Facilities is rooted within the tenets of Homeland Security Presidential Directive-12 (HSPD-12).
HSPD-12 mandated the establishment of a government-wide standard for identity credentials to improve physical security in federally-controlled facilities. HSPD-12 required government employees and contractors be issued a new identity credential based on Federal Information Processing Standard, (FIPS)-201, Personal Identity Verification (PIV) for Federal Employees and Contractors, in accordance with the United States Office of Management and Budget, (OMB) and Office Personnel Management, (OPM) guidance.
Revision Updates Faced Many Challenges
This revision updates and bring into clear focus the methodology to apply the secure attributes of the PIV card for access to Federal owned and controlled facilities. That said, the genesis of this publication had a rocky start. The basic document was predicated by a migration study I wrote in 2007. The strategy and plan developed the effective and efficient co-operation between the physical security and information technology disciplines. The convergence of these disciplines was needed to meet the mandates of HSPD-12 and to achieve the desired end-state compliance with FIPS 201-1. Many within the physical security community, both inside and outside the federal government, felt this mandate was in the “TO HARD TO DO” box. There were many meetings and discussion throughout the government as to how the industry would be able to respond to the requirements of FIPS 201.
The Smart Card Alliance[1] Physical Access Council in collaboration with the Open Security Exchange, Security Industry Association, and International Biometric Industry Association published in September 2007 the Physical Access Control System, (PACS) Migration Options for Using FIPS 201-1 Compliant Credentials. A key conclusion of this report was:
“…In transitioning to accepting PIV credentials, it is recommended that the security director first define the end-state identification verification goals, then decide the equipment, if any, needed to help accomplish this goal and finally, develop a transition and migration plan that meets the agency's needs and budget…”
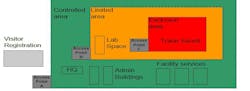
The leadership of the Office of Management and Budget, (OMB) requested that the National Institute for Standards and Technology, (NIST) prepare a guideline document for Federal agencies to use the PIV Card in a PACS. SP 800-116 was the result. NIST, under the leadership of the late William “Bill” MacGregor, organized a team of Information Technology and physical security analysts to develop this special publication. In my role as the Convergence Subcommittee Chairman, to the Department of Homeland Security’s Interagency Security Committee (ISC) Lead the physical security perspective for the publication. One important contribution to the document was to adopt the United States Army’s Field Manual (FM) 19-30, Titled Physical Security Restricted Area concept.
This concept is in the Examples of Mapping PIV Authentication Mechanisms shown as Figure 5-5 on page 25 of SP 800-116-1.
The Technical Challenges are many. The PIV credential is Smart Card technology, essentially a computer on a chip embedded in plastic. NIST FIPS 201-1 mandates that the PIV credential is to also include two backward compatible technologies, magnetic stripe and barcodes. However, FIPS 201-1 did not include the most common technology in use today for PACS with wireless low-frequency proximity technology[2]. This technology (in 2007) was deployed in about 70 percent of existing government installations[3]. By adding low-frequency proximity technology to the PIV card for initial deployments, the utility of the existing installed PACS could be extended. This will provide a smoother migration to end state PIV-enabled PACS. It was understood that this was a temporary, short-term strategy that enables an agency to leverage its investment in its’ existing installed base of PACS, that utilizes proximity technology. The inclusion of the low-frequency proximity technology is not necessary if the agency’s existing PACS use the technologies already included on the PIV credential (magnetic stripe and/or barcode). It is also understood that inter-agency credential interoperability, a key HSPD-12/FIPS 201-1 goal, will most likely not exist during this transition phase with any of the backward compatible technologies. Adoption of the 125 kHz proximity on the PIV card save agencies thousands of dollars by not having to “fork-lift” replaces all the thousands of 125 kHz proximity readers with 13.56 MHz high-frequency proximity technology mandated by FIPS 201-1.
Getting to Down to the Nitty Gritty
Now, let’s get down to the basics. Bill MacGregor, provided to the federal government in SP 800-116, a sound methodology with multiple-application leverages of trust. All the PIV electronic authentication mechanisms rely on Public Key Infrastructure, (PKI) trust. As suggested in the Smart Cad Alliance 2007, “… the Security Director must define access requirements…” This definition, of course, must be based on area sensitivity. Simply put, each PIV card has a certificate that must be validated. This validation reinforces the trust.
This revision improved the guidance to federal agencies. The essence of HSPD-12 and FIPS 201 was to strengthen the protocols needed to access physical and logical resources. The directive and standard mandated the development of a secure, verifiable and interoperable “medium”[4] that would be used across the federal government. The information Technology folks were way ahead in the authentication for secure access process. The PACS architectures were antiquated, proprietary, stove-piped[5] and lacked secure access attributes. To highlight this to the physical security community, SP 800-116 provides an extensive section on the threat environment.
Prior to the issuance of HSPD-12 the preponderance of federal government facilities used the “Flash-Pass or Flash-then-Pass” system of access, which led to visual counterfeiting, card duplication[6] and social engineering[7]. In addition, many agencies used electronic access using the 125KHz proximity technology. This technology is susceptible to skimming, sniffing, social engineering and electronic cloning. The guideline recognizes the complexities of PACS. It proposes the use of the cryptographic algorithms of the PIV card reducing the probability of a successful unauthorized physical access.
Mandating the Card Features
To accomplish this, the guideline supports the FIPS 201 mandated authentication features of the PIV card. The core authentication features are known as K-H-A. The “K” refers to something you know. Each PIV card has a Personal Identification Number or PIN. This PIN is a 6-digit number generated by the PIV cardholder or may be given to the cardholder by the issuing organization. The “H” refers to something you have. Each PIV card has a unique authorization Public Key Infrastructure, (PKI) Certificate. This certificate is issued by the organization and is managed by an approved certificate authority, (CA). The CA must adhere to strict common policy requirements[8]. Finally, there is the “A”. “A” stands for something you are. This is the cardholder’s biometric. The latest FIPS 201-2 allows for two types of biometrics. They are fingerprints and iris. Therefore, the use of these card features will provide to the organization physical access option commensurate with the sensitivity of the area. In chapter 4, PIV Authentication Mechanisms in PACS Applications, an extensive use-case describes how to apply these mechanisms within a facility with various sensitivity locations.
To implement SP 800-116-1, the guideline strongly suggested organizations integrate these concepts with the Identity, Credential and Access Management, (ICAM) program. As organizations are operating in a constantly shifting threat environment, what with data breaches being all too common, rising incidents of identity theft and inconsistent enforcement of trust relationships, cybersecurity must be addressed in a comprehensive manner across the enterprise to meet the growing threats.
The cybersecurity threat is compounded by the increasing need for improved physical security at the organization’s owned and leased facilities sites. The ICAM Construct is a collection of functions and programs that support the intersection of identities (with associated attributes), credentials and access (cyber and physical) and control into one comprehensive management approach for organizational decision making. Using the ICAM construct “… An integrated PACS enables information sharing across systems and agencies with common access controls and policies. The agency’s ICAM infrastructure would serve as the central Chain of Trust of identity that many applications can trust and consumer authorization decisions—specifically applications that leverage PIV for physical and logical access…”
Final Thought
Countries that deployed PIV-like smart cards as their national identification card should leverage the ICAM Construct along with the guidelines set forth in SP 800-116-1 to their installed base, they could have a secure means to deliver government services. For Private industry, this could be an expensive undertaking. However, companies should weigh these measures to the value of their organizational holdings and operations.
About the author: Ron Martin, CPP, has business relationships with a diverse mix of businesses. Ron retired from the United States Army in 1999 and the U. S. Government in 2011. In between his tours of Federal Service, he served five years as a civilian police officer in the Commonwealth of Virginia. During his Federal Service e served with the U. S. Department of Commerce, where he led the initial implementation of Homeland Security Presidential Directive 12 (HSPD-12). At the U. S. Department of Health and Human Services, he served as the Program Director for the development and Implementation of the Department’s Identity, Credentialing and Access Management (ICAM) Program. Ron is an Adjunct Professor at Capitol Technology University in Laurel MD, where he teaches a graduate course in Identity, Credential and Access Management (ICAM).
Resources:
[1] Now known as the Secure Technology Alliance
[2] Proximity Technology – also known as 125 kHz, low-frequency proximity. This is different than the NIST mandated 13.56 MHz high-frequency proximity technology mandated by FIPS 201-1 as a port into the Smart Card chip. 125 kHz proximity functionality is enabled by incorporating a separate chip and antenna on a PIV card.
[3] Information Provided by the Security Industry Association, http://www.siaonline.org/
[4] Medium is used to represent the use protocol in “Derived Credentials” See: https://www.nccoe.nist.gov/projects/building-blocks/piv-credentials
[5] A stove-pipe is a structure which largely or entirely restricts the flow of information to within the application. It inhibits or prevents interoperability across systems.
[6] The person claiming the card lost, stolen and/or destroyed. They use the “extra” card or pass it to someone to use.
[7] Reproducing the card attributes that are not protected by a Personal Identification Number, (PIN).
[8] https://www.idmanagement.gov/wp-content/uploads/sites/1171/uploads/Common-Policy-Framework.pdf