Real Words or Buzzwords: Bluetooth vs. Bluetooth LE
Bluetooth
Early Bluetooth-enabled physical security products were severely criticized by IT security folks because the product designers didn’t give any thought to data and communications security. Way back in 1989 – when Ericsson Mobile in Sweden began the development of the short-range wireless technology later named Bluetooth® – no physical security industry companies were paying attention to data security. It took almost two decades for physical security to start taking data security seriously.
Meanwhile, in 1998, Ericsson, IBM, Intel Corporation, Nokia and Toshiba formed the Bluetooth Special Interest Group (SIG) as its initial members. The first consumer Bluetooth device – a hands-free mobile headset – was launched in 1999 and earned the “Best of Show Technology Award” at COMDEX. Today, on the Bluetooth SIG website, there are over 36,000 member companies listed, and billions of Bluetooth-enabled devices ship every year.
Bluetooth-enabled products are now emerging in many fields, including security and safety, with a wide variety of implementations for a myriad of use cases. It has become important to understand Bluetooth due to the value Bluetooth-enabled products provide, but also because from one product to another the Bluetooth implementations – and their security – are not all the same. The devil is in the details, as the expression goes.
The Bluetooth SIG states, “Bluetooth specifications include a collection of features that provide developers the tools they need to secure communications between Bluetooth devices and implement the appropriate level of security for their products.
“All Bluetooth specifications are subject to security reviews during the development process. In addition, Bluetooth technology is an open, global standard, and the Bluetooth SIG encourages active review of the specifications by the security research community.”
Note that the security tools are there, but it’s up to manufacturers to design a security product or system. And it’s up to security designers and specifiers, security integrators, and end-user customers to pay close attention to the security aspects of their implementations.
Classic and Modern Bluetooth
The original Bluetooth radio technology – what we’re familiar with from our smartphones linking to cars – is now known as Bluetooth Classic radio. Supporting point-to-point device communication, Bluetooth Classic is mainly used to enable wireless audio streaming and has become the standard radio protocol behind wireless speakers, headphones, and in-car entertainment systems. Bluetooth Classic radio also enables data transfer applications, including mobile printing. It transmits over 79 channels in the 2.4 GHz unlicensed industrial, scientific, and medical (ISM) frequency band.
Bluetooth Low Energy (LE)
Bluetooth LE radio, originally marketed as Bluetooth Smart and commonly referred to as BLE, is designed for very low power operation while maintaining a similar communication range. However, BLE is much more than a low-power version of Bluetooth Classic. BLE operates in the same radio spectrum range as Bluetooth Classic, but uses a different set of 40 channels at typically about half or less the data rate of Bluetooth Classic.
Solution Areas
Differences in how the devices communicate make possible a wider set of applications and use cases for Bluetooth LE than for Bluetooth Classic. See Figure 1 below.
Bluetooth Piconets
Piconet means "tiny" network, as explained by the PCMag Encyclopedia. A piconet is a Bluetooth network composed of two or more Bluetooth devices that operate in close proximity on the same channel and frequency hopping sequence. Piconets operate in both ad hoc (peer-to-peer) and infrastructure (central base station) modes of operation.
In a piconet, one device is the master, which establishes the frequency hopping scheme, and there can be up to seven active and 255 inactive slave devices. Only a master device can send data; slave devices can only receive. However, a slave in one piconet can be a master in another, creating a chain of piconets called a "scatternet" that extends the distance between all devices. While Bluetooth Classic is limited to point-to-point communication topologies, Bluetooth LE is not.
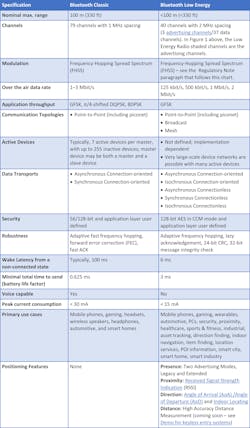
Bluetooth Technology Technical Differences
The Figure 2 chart below shows a few similarities and many differences between the two technologies (data from both the Bluetooth SIG website and Wikipedia).
Figure 2 Links
- Advertising channels
- Received Signal Strength Indication (RSSI)
- Angle of Arrival (AoA) /Angle of Departure (AoD)
- Indoor Locating
- Demo for keyless entry systems
Regulatory Note
Bluetooth Low Energy uses frequency hopping to counteract narrowband interference problems. Classic Bluetooth also uses frequency hopping, but the details are different; as a result, while both FCC and ETSI classify Bluetooth Classic as an FHSS scheme, Bluetooth Low Energy is classified as a system using digital modulation techniques (FCC) or a direct-sequence spread spectrum (ETSI). These requirements have implications for the Bluetooth LE physical and link layers. (Bluetooth Low Energy Regulatory Aspects white paper, Bluetooth SIG, pages 6 and 12).
Bluetooth Myth vs. Fact
Bluetooth technology is more than 20 years old. Thus, depending on which types of Bluetooth applications people have been exposed to, their impressions of Bluetooth technology may be outdated. This is especially true because, like other information and communication technologies that are exponentially advancing, BLE is continually being improved by the Bluetooth SIG.
Large scale device networks of all types are feasible. Luminaire-level lighting controls (LLLC) are currently being championed for smart buildings. The Bluetooth Blog states, “The effective, reliable distance between Bluetooth® devices can be greater than a kilometer and can even support reliable remote control of beyond-visual-range (BVR) drones. Though several factors can influence the effective range of Bluetooth technology — from radio spectrum and transmit power to antenna gain and path loss — the variable range is proof of the technology’s versatility. Unlike other wireless technologies, the wide spectrum of achievable and reliable distances gives developers tremendous flexibility to create solutions that meet the precise needs of their target use case.”
Implications for Security and Safety Devices
Key limitations of Bluetooth classic don’t apply to Bluetooth Low Energy. A variety of network topologies can be used. Thus, when a device is stated to be a BLE device – the same type of device by another manufacturer may be significantly different in design and functionality. As stated above, BLE capabilities give product developers tremendous flexibility to create solutions that meet the precise needs of their target use case. Each target use case brings its own user experience requirements, as well as insider threat risks.
Bluetooth LE doesn’t require device pairing to a smartphone, like what a modern car requires for smartphone calls or audio playlist use. A smartphone can connect to a BLE-enabled access control reader and exchange mobile credential information in a fraction of a second, from a much longer range than typical smart credentials require. However, each manufacturer’s implementation of mobile credential use may provide a different user experience, depending on the mobile app required and what reader and mobile device capabilities are supported.
Multiple User Experience Requirements
This was apparent in my recent review of several different manufacturers’ multi-technology BLE-enabled card readers with support for smartphone mobile credentials. Each reader provided a different user experience. One reader could be configured to talk to the smartphone app and require the user provide a fingerprint or facial image – using the two-factor authentication capabilities of the phone. There is no requirement to hold the phone up to the reader. This can be configured to be a user-specific and/or reader specific requirement.
Another card reader does require holding up the smartphone within an inch of the reader for a second or two. Yet another card reader allows the smartphone to remain in pocket or purse, and only requires waving a hand in front of the reader. Still another reader also allows the smartphone to remain in pocket or purse but requires a two-finger touch to the reader, to signal that the user is not just a bystander but has intent to enter the door.
Use Case Convenience vs. Security
For someone driving a warehouse vehicle, the reader that only required a hand wave as the vehicle drives by could be most desirable. For senior management offices or areas containing highly sensitive information, two-factor authentication may be the most important capability. For doors where most of the pedestrian traffic involves users not authorized for access, there could be a significant insider threat risk if an unauthorized individual could follow behind an authorized user, wave a hand in front of the reader and gain entry. That’s an entirely new kind of tailgating. A capacitive two-finger touch for an office reader near an outdoor entryway would not be convenient in a situation where winter weather required gloves or mittens.
Fortunately, all of the readers I reviewed supported multiple configurations with options to suit the access control capabilities appropriate for each specific door.
Additionally, a modern access control system would allow the integration of IoT devices, so that – for example – a card reader in a warehouse vehicle pathway would only accept a credential presentation when a vehicle was also present in front of the reader. A pedestrian would be required to use a different reader at the door.
Understanding the access risks that apply to each door is even more important with modern technology, as it’s no longer a one-type fits all reader and credential situation as it has been in past decades.
The reader story just presented highlights the importance of keeping keep two things in mind about modern technology:
- Deployment requirements and user requirements of any modern device or system can vary significantly between various brands of the same type of product.
- Modern technology is evolving at a rapid pace, and so each device or system purchase requires the utmost diligence in examining current product capabilities to ensure that the highest security ROI is obtained.
About the Author:
Ray Bernard, PSP CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s Top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon. Follow Ray on Twitter: @RayBernardRBCS.
About the Author

Ray Bernard, PSP, CHS-III
Ray Bernard, PSP, CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon. Ray has recently released an insightful downloadable eBook titled, Future-Ready Network Design for Physical Security Systems, available in English and Spanish.
Follow him on LinkedIn: www.linkedin.com/in/raybernard.
Follow him on Twitter: @RayBernardRBCS.