CyberTalk with Ray Canzanese
The defender’s most valuable tool is their knowledge of the adversary. Netskope Threat Labs recently published its quarterly Cloud and Threat Report: Top Adversary Tactics and Techniques, aimed to figure out attackers’ motivations, objectives, and tricks of the trade so defenders can design systems to be resilient to those techniques and implement controls to detect malicious activity. In the report, we detail which attack techniques were most used against Netskope customers during the first nine months of 2023.
If you can implement defenses against the key techniques outlined in this report, your organization will be protected against many adversaries and their attacks. No matter what threat group you’re up against, you can have proper defenses in place. One of the key findings from this report was a significant number of criminal adversaries attempting to infiltrate customer environments, with Russia-based Wizard Spider targeting more organizations than any other group.
SecurityInfoWatch.com recently caught up with Ray Canzanese, the Director of Netskope Threat Labs, which specializes in cloud-focused threat research. His background is in software anti-tamper, malware detection and classification, cloud security, sequential detection, and machine learning.
SIW: Can you tell us more about the significant takeaways from this report when it comes to top adversary groups?
Canzanese: We found that the top criminal adversary groups motivated by profit were based in Russia and Ukraine, and the top geopolitical threat groups were based in China. Adversaries typically fall into one of two categories based on their motivations. Financially motivated actors tend to develop playbooks using tools like ransomware so they can easily repeat attacks without having to customize based on their victim. Many criminal groups now operate in an affiliate model, spreading their criminal enterprise all over the globe. As a result, defenders typically categorize threat groups with the country or region from which its core members are believed to be located. Wizard Spider is one example of this kind of cybercriminal group, credited with creating the notorious, ever-evolving TrickBot malware. Other top criminal adversary groups include the creators of Clop ransomware, TA505, and FIN7, who used REvil the ransomware and created the Darkside ransomware.
On the other hand, geopolitical adversaries target specific regions and industries for their intellectual property. Usually, these groups are affiliated with nation-states and their activities align with political, economic, military, or social conflicts. Their modus operandi typically includes cyber espionage against organizations (especially governments) and attacking critical infrastructure. Geopolitical adversaries also engage in information warfare, spreading propaganda, manipulating public opinion, and influencing popular elections. memupass (also known as Cicada, POTASSIUM, Stone Panda, APT10, Red Apollo, CVNX, HOGFISH) and Aquatic Panda were the top geopolitical groups attempting to target users of the Netskope Security Cloud platform this quarter.
SIW: What are the top techniques you are seeing these adversary groups use?
Canzanese: The most popular techniques for initial access so far in 2023 are spearphishing links and attachments. Social engineering attacks like this continue to be one of the easiest ways to successfully target victims. In fact, as of August, adversaries were three times more successful at tricking victims into downloading spearphishing attachments compared to the end of 2022. It’s even easier to convince victims to download malicious files when they’re delivered via cloud apps.
Organizations are generally doing a very good job of protecting against phishing emails coming into users' managed user accounts. Only a small percentage of people clicking on spearphishing links and attachments do so from managed email accounts. Instead, victims are clicking spearphishing links and downloading spearphishing attachments in other places, like social media, search engines, and personal email. We found that 16 times as many users attempted to download a phishing attachment from a personal webmail app compared to managed organization webmail apps so far in 2023.
After reporting an increase in malware downloads from Microsoft Live Outlook, we dug a little deeper and found that a major contributor to this rise was the variety of Amazon-themed PDF attachments. In a recent campaign, we found attackers using the common social engineering technique of creating an urgent call to action, targeting personal Outlook accounts in North America, Southern Europe, and Asia. Scammers abuse legitimate redirector domains and URL shorteners to evade detection- providing evidence for why you should never enter sensitive information like passwords or credit card information after clicking on a link.
SIW: Are there any significant differences in threats among different key verticals or regions?
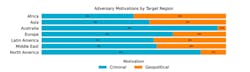
Canzanese: Compared to geopolitical adversaries, criminal adversaries are more active in Australia and North America. Other parts of the world, such as Africa, Asia, Latin America, and the Middle East led in geopolitical motivated attacks. The higher volume of geopolitical adversary activity globally appears to be the result of active conflicts and the broader geopolitical climate in those regions.
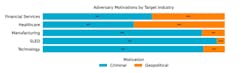
The financial services and healthcare industry verticals saw a significantly higher percentage of activity attributable to geopolitical threat groups as opposed to financially motivated groups. In those verticals, almost 50% of activity comes from geopolitical adversaries. On the other hand, manufacturing, SLED (State, Local and Education) and technology each saw less than 15% of activity coming from geopolitical-motivated actors. This means that, in general, cybersecurity teams in SLED and technology organizations can focus their attention on cybercriminal adversary activity, while organizations in financial services and healthcare need to invest resources to defend against both.
SIW: How is malware being delivered and why does it matter to enterprises?
Canzanese: Adversaries are constantly trying new ways to trick victims into clicking malicious links- we track those changes in our monthly reports. Cloud apps are the number one vehicle for successful malware execution, with 55% of malware that users attempt to download being delivered via cloud apps. The apps with the highest number of attempted malware downloads were also some of the most popular cloud apps in the enterprise, but there is a long tail, with users downloading malware from 477 different apps so far in 2023. The most popular cloud app in the enterprise, Microsoft OneDrive, was responsible for more than one-quarter of all cloud malware downloads.
SIW: What steps can organizations take to protect themselves from these threats?
Canzanese: The MITRE ATT&CK framework provides defenders with a common language for understanding an adversary’s tactics and techniques. Organizations need to evaluate their defenses to determine how their cybersecurity strategy needs to evolve- we can use the framework to match an organization’s defenses to their adversaries. Here are the 5 most pervasive techniques organizations need to be prepared to defend against.
Gaining Initial Access
- Spearphishing Links – Organizations need anti-phishing defenses that cover more than just email to ensure that users are protected against these malicious links- implement a Secure Web Gateway (SWG) solution that inspects domain name system (DNS) traffic, cloud traffic and web traffic for evidence of phishing to prevent users from falling victim to spearphishing links, no matter where they came from.
- Spearphishing Attachments – In addition to the above, employ more robust protections against users downloading spearphishing attachments by inspecting all HTTP/HTTPS downloads and all web & cloud traffic for evidence of spearphishing.
Malware Execution
- Malicious Links and Files – An effective defensive strategy against malicious links and files must inspect all traffic, especially high-risk file types, for malicious content using a combination of static and dynamic analysis before being downloaded. Block downloads from apps that are not used in your organization, and only allow apps and instances that are necessary.
Adversary C2 Traffic
- Application Layer Protocol: Web Protocols – Use a SWG and an Intrusion Prevention System (IPS) to block communication to known C2 infrastructure. Block newly registered & observed domains and alert unusual network traffic patterns to enable early detection.
Data Exfiltration
- Exfiltration over C2 Channel – In addition to the above, further protections against C2 include the identification of data transfer anomalies, like spikes of uploads to unusual locations and the transfer of encrypted or encoded content.