In Government, Access Control Means Cybersecurity
This article originally appeared in the January 2022 issue of Security Business magazine. When sharing, don’t forget to mention Security Business magazine on LinkedIn and @SecBusinessMag on Twitter.
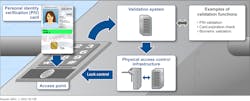
When it comes to access control for the U.S. federal government, most integrators in our industry immediately think of physical controls like cards and readers; however, this huge ecosystem of departments and agencies creates, disseminates, and stores significant amounts of often sensitive data – and it is no stranger to the scourge of cybercrime.
In 2018, more than 31,000 cybersecurity incidents were reported by federal agencies. The following year, the U.S. government accounted for 5.6 percent of all data breaches and 2.1 percent of exposed data in the United States.
On the heels of an October 2020 attack on state election websites and the recent ransomware attack against the Colonial Pipeline, President Biden signed a new Executive Order (EO) in 2021 under which all agencies must adopt multi-factor authentication (MFA) and encryption for data at rest and in transit wherever possible. MFA requires users to provide two or more verification factors to access data via applications, online accounts, or VPNs.
Additionally, the recently issued data breach notification bill – the Cyber Incident Notification Act of 2021 – would “require Federal government agencies, Federal contractors, and critical infrastructure operators to notify the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) when a breach is detected so that the U.S. government can mobilize to protect critical industries across the country.”
In August, the CEOs of technology powerhouses Amazon, Apple, and Microsoft met with President Biden to discuss how the private sector and government can better work together to detect and prevent future cyberattacks, especially those targeting critical infrastructure services.
One of the pervasive challenges to building impenetrable federal government cyber defenses is human error, often the weakest link in the security chain. Government employees are prime targets for cyberattacks because they have access to sensitive data, such as financial, economic, and military records. Hackers typically target government employees using phishing scams, posing as trusted sources to access login credentials.
Federal government agencies need to shift to a mindset where security is implicitly attached to data and the users who need to access it. If they fail to act decisively, they will face a future littered with data breaches that have far-reaching implications.
The good news? Hardware security keys put the power (literally) back into their hands and allow them to focus attention on what matters: protecting data and identities.
How Access Control Tech Fits into the Latest Protocols
A significant cybersecurity hurdle facing the federal government is the ubiquity of its data. Given the fluid and multi-faceted environment in which departments and agencies operate, most do not hold a firm grasp of what data they have or where it is located.
The 2021 Thales Data Threat Report (https://cpl.thalesgroup.com/data-threat-report) revealed that just 28% of federal government respondents said they have full knowledge of where their data is stored, and just one-third claimed to be able to fully classify their data.
Further compounding the challenge, cloud storage is now well on its way into the mainstream in this sector. More than a quarter (29%) of respondents to the same survey said they now store greater than half of their data in the cloud, and 57% indicated that 31% to 50% of the data stored in an external cloud is sensitive.
Adequate levels of encryption have not accompanied this large-scale cloud migration. Only 15% of respondents said more than half of their sensitive data stored in the cloud is encrypted. This is concerning given the Biden EO clearly states the directive on the matter.
The failure may be due partly to the fact encryption and key management can be complex to deploy and manage, and often requires scarce and expensive cybersecurity skills.
Federal government agencies must become more intentional about aligning their operations to the latest and most robust industry standards and protocols, which could easily involve government access control programs.
For example, a good best practice would be pairing Common Access Card (CAC) and Personal Identity Verification (PIV) access with smart card readers, where the CAC/PIV card is the authenticator, and the smart card reader is used in the authentication process. Another example would be to secure login.gov accounts with a FIDO security key to prevent phishing attacks from hijacking user accounts and compromising credentials.
Overview of Federal Government Smart Card Programs
Smart card technology is currently recognized as the most appropriate technology for identity applications to meet critical security requirements. Around the world, countries use smart cards for secure identity, payment, and healthcare applications.
The U.S. federal government has standardized on smart cards for employee and contractor identification cards. It is also specifying smart cards in new identity programs for citizens, transportation workers, and first responders.
CAC: One of the most advanced smart ID card programs in the U.S. is the Department of Defense (DoD) CAC, a smart card serving as DoD standard identification for active-duty military personnel, selected reserve personnel, civilian employees, and eligible contractor personnel.
CAC is the principal card used for logical access to DoD computer networks and systems and is the main method of enabling physical access as systems are installed for authentication and access at DoD facilities.
- Authentication for all privileged users, including servers, networks and applications;
- Network authentication for all users;
- Application authentication for all users of an application protecting or containing sensitive information; and
- Access to facilities and buildings.
FIDO Government Deployments
Through its login.gov program, the U.S. General Services Administration (GSA) has rolled out a single sign-on approach across different agency applications. FIDO (Fast Identity Online) is one option.
FIDO2 is a set of strong authentication standards enabling users to leverage common devices like on-device biometrics and FIDO security keys to authenticate to online services with phishing-resistant cryptographic security. After a thorough review, GSA found FIDO2’s phishing resistance made it the most appropriate approach to address its security challenges.
The login.gov platform provides single sign-on for U.S. public and federal employees to interface and transact with federal agencies online. With one account, users can access services like the federal government’s job board, USAJOBS, and the Department of Homeland Security’s Trusted Traveler Programs, such as Global Entry.
Other federal bodies have made recent legislative and programmatic moves to boost their levels of data security, including:
- National Cybersecurity Center of Excellence: Mobile Single Sign-on for Public Safety/First Responders;
- NIST: Digital Identity Guidelines: Implementation Resources for SP 800-63-3 Program
- Office of Management and Budget: Implementation of OMB memo M-19-17 – FICAM Policy
- Drug Enforcement Administration: Electronic Prescribing of Controlled Substances
While these moves are welcome and warranted, is it feasible to bring a standard, robust approach to what still remains a piecemeal legislative patchwork? The easiest and most effective option is to invest in hardware-based security keys supporting FIDO2 specifications.
How Security Keys Help
Hardware security keys are increasingly being recognized as the sensible and responsible way to solve the federal government data security challenge. The beauty of this approach is the authentication process: it is one-touch.
When users sign into their email or applications, for example, they enter their password and click “sign in”. But the process does not end there. They are required to supply a secondary authentication factor to prove they are who they claim to be and are authorized to sign into the account.
At this stage, the user inserts their unique, personal key into their device, presses the button, and access is granted immediately.
In technical terms, what happens here is in the background. A challenge-response exercise is initiated using public-key cryptography between the security key and the service provider. This eliminates the threat of users’ accounts being accessed via compromised credentials or a phishing attack.
Dr. Manfred Mueller is COO and General Manager for Identity at Identiv. Request more info about the company at www.securityinfowatch.com/10492079.
About the Author

Dr. Manfred Mueller
Dr. Manfred Mueller is COO and General Manager for Identity at Identiv.