When the term “convergence” became a buzzword in the security industry, we all saw it plastered across tradeshow banners and in bold magazine ads, but it pretty much disappeared after just a few years. After all, “cloud” is the hot new buzzword these days.
Lately, a remarkable number of people have told me that convergence “is over” or “has come and gone.” One person said, “Convergence arrived a long time ago.” More than one has advanced the idea that we should drop the word “convergence” altogether, as it lacks clarity and refers to too many things.
If statements about convergence being passé cause security practitioners to stop thinking about security convergence — not just the word, but the actions and concepts it is intended to embrace — then organizational security will be taking a big step backward. Instead of dropping the term, let’s clarify what is meant by convergence, as I would have to agree that “the word” has only gotten us so far down the path.
There are two types of security convergence, and here’s a news flash: Neither one is anywhere near the end of its evolution. Many of us are still missing out on the tremendous value that convergence has to offer.
Technology Convergence
The first type of security convergence is technology convergence, which impacts electronic physical security systems, and is the result of the more general information technology convergence. IT convergence is everywhere, not just in security. Back in the ’90s, IT convergence was touted as “voice, data and video all on the same cable.” But it did not stop there.
Before long, we had voice, data and video interacting with each other. The first stage of IT convergence, same cable, was a big cost-saver; however, outside of cost savings, it did not impact customer value. The second stage, interaction, is where tremendous customer value has been and continues to be created. Second-stage convergence requires innumerable standards to be developed and deployed. It also requires evolving the cable and wireless communications infrastructure with enough bandwidth to support the high level of data throughput, as well as the interactions among systems and devices.
These days, what we used to call a mere telephone is a class of devices that includes iPods, Droids and Kindles. Consider the level of customer interaction with The Daily — the first iPad-only newspaper. It is so radically different from any previous newspaper interaction that it defies comparison. That typifies the benefits that should result from full convergence.
Where does security technology convergence stand? The security industry is still trying to get its “same cable” act together, and has hardly scratched the surface on “interaction.”
For more insight into some of the “same cable” problems, download the report “Convergent Security Risks in Physical Security Systems and IT Infrastructures” from the Alliance for Enterprise Security Risk Management (AESRM) at www.aesrm.org.
Organizational Convergence
The second type of security convergence is organizational convergence, which involves eliminating organizational silos that keep security functions walled off from the rest of the organization in critical ways, and in particular between IT security and physical security. For example, consider information protection. Physical security protects information; IT security protects information. But to the organization, it is all “information protection,” and that is the business focus.
Few organizations have an overall “information protection” plan that is focused on the critical information assets and includes physical, electronic (IT) and human knowledge aspects. Instead, most companies have separate physical security, IT security, privacy protection and other plans — they are rarely synchronized, and they are often not covered by a single change management process to update security planning where assets require protection from more than one area.
Convergence is a Necessity
When electrical utility companies were not getting the picture on convergence, the North American Electrical Reliability Company (NERC) developed Critical Infrastructure Protection (CIP) standards that mandate many elements of convergence. For facilities covered by the regulations, the security plan has to define both “physical security perimeters” and “electronic security perimeters.”
Physical security perimeters are the physical borders surrounding computer rooms, telecommunications rooms, operations centers and other locations in which critical cyber assets are housed and for which access is controlled. Where a complete six-wall border (four walls plus a ceiling and floor) cannot be established, alternative measures of protection are required.
Electronic security perimeters are the logical border surrounding a network to which critical cyber assets are connected and for which access is controlled. Network connections to computers and control equipment are the “doors” through which to gain passage beyond the electronic security perimeter.
The NERC CIP standards actually specify that physical access control systems must protect the electronic security perimeter, and that cyber security measures must be applied to the physical access control systems. In other words, the physical and logical access control systems must protect one another. But the standards don’t stop there. Change management processes must include review and application of physical and logical security measures. Why? Because the converged application of security measures is necessary in order to establish acceptable security for critical electronic assets.
Exelon Corp. operates the largest fleet of nuclear energy plants in the United States. In a keynote address last September to the Nuclear IT Strategic Leadership (NITSL) Symposium, Susan Landahi, Exelon’s senior vice president of Operations said, “Cyber Security is going to rival physical security in importance. Physical and Cyber better learn to get along; in fact, we need to co-locate them now in the same organization.”
The State of the Union
In leading organizations, the union between corporate and physical security and IT is established around key touch points, with increasing collaboration under an overall objective to benefit from convergence that is followed up by specific planning. Organizations that are achieving the greatest benefits with convergence are those with strategic risk planning collaboration at senior levels, and who also have tactical collaboration in appropriate projects, initiatives and ongoing operations.
However, most organizations still struggle with technical and organizational convergence issues, mainly because of a lack of active convergence knowledge and planning. They do not get out in front of convergence issues — they work reactively, addressing problems as they arise, but without thought of advancing their organization into a stronger position, and without understanding the full convergence landscape.
Top-to-Bottom Convergence
Organizations that have been most successful at advancing through convergence have been those with convergence dialogs and planning going at all levels from top to bottom in the organization. These are rarely discussions about convergence itself, as a subject or topic. They are discussions about identifying and addressing risks at various levels of the organization.
How Do You Start?
Dave Tyson is Senior Director and CISO at Pacific Gas & Electric Company (PG&E). Incorporated in California in 1905, PG&E is one of the largest combination natural gas and electric utilities in the United States, serving more than five million electric customer accounts and four million-plus natural gas customer accounts. Tyson is also the author of the book “Security Convergence: Managing Enterprise Security Risk” — the working reference that I use when my security practitioner clients want to address security convergence to improve their organization’s risk profile. The book covers the full convergence spectrum in a very practical way.
Making a good start should include an important convergence insight: it is people who advance the organization’s risk awareness, set strategies and policies, collaborate and develop security plans, and put such plans into effect. People change the organization, not technology. So although there has been a great focus on “convergence” products and features in the security industry, the place to start is with people.
Here are six steps to approaching convergence in your organization:
1. Get the book. Get Tyson’s Security Convergence book referenced above.
2. Identify Potential Convergence Contacts – Part one. Begin reading, and make a note by page reference as you come across material that relates to a part of your organization. If you do not have a contact in that area, look them up in your organization’s directory or org chart, or ask someone a little higher up in the organization to suggest a contact.
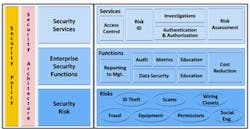
3. Identify Potential Convergence Contacts – Part two. After finishing the book, go back to the Enterprise Convergence Points chart on page 91 (or use the chart above) to help you identify convergence points in your organization. Technology convergence points are those points where physical security systems and processes interact with IT or IT security. Organizational convergence points are those where physical and IT security risks connect or cross over in the organization.
4. Share the Book with Your Key Organizational Contacts. This is an important step, as it will help facilitate collaboration with others in your organization, and keep you from having to explain your convergence ideas at length over and over again. Eventually your convergence contacts should all have a copy as a reference, or access one from your organization’s in-house library if you get a few copies placed there.
5. Proceed with a Plan or Outline. As Tyson says in the book, “It is safe to say that, in most organizations, convergence needs to be slow and measured. Introducing any organizational and cultural change can be challenging, to say the least; changes with such far-reaching potential impact must be approached methodically.” Once you have had initial discussions and found common interests in the convergence landscape, work together to outline an initial plan — even if it is exploratory in nature — and proceed methodically.
6. Prioritize Based on Risk and Organizational Alignment. Especially with technology convergence, there can be a tendency to want to jump right to the ideal state immediately. Be sure to understand the organizational impacts, and realize that you must keep your eyes and ears open for unintended consequences and organizational misalignment. Some things may have to wait until the next budget cycle or until a project or initiative is completed, in order for the right resources to become available. Educational steps are also important, and when action is not a readily available course, continued education often is. When immediate action is warranted because of risk concerns, then education about the risk factors and security options should be the first part of any request for action or resources.
I’ve saved one of Tyson’s important points for last: “Convergence is about optimizing the risk profile so that all risks are identified, considered and either mitigated or accepted — ideally with some form of compensating control.
I urge you to truly ponder this thought in detail: Identify and mitigate ALL RISKS in the environment. This is what the convergence security practitioner, or group of practitioners, must do. Senior management should not be accepting any more risk than they are aware of, and if all the risks are well understood in the new and increasingly complex environment, then the first part of the job is done.”
About the Author

Ray Bernard, PSP, CHS-III
Ray Bernard, PSP, CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon. Ray has recently released an insightful downloadable eBook titled, Future-Ready Network Design for Physical Security Systems, available in English and Spanish.
Follow him on LinkedIn: www.linkedin.com/in/raybernard.
Follow him on Twitter: @RayBernardRBCS.