Technology in Focus: ROI reinvented
Note: This is the next in a series of technology and application blogs sponsored by Axis Communications. SecurityInfoWatch.com will host these periodic updates throughout the year. We welcome your feedback.
“Get closer than ever to your customers. So close that you tell them what they need well before they realize it themselves” – Steve Jobs, former CEO, Apple
It is a great challenge to tell a customer what they want. However, you may be able to approximate and even predict what they want before they realize they want it. When you think about it, IT and physical security managers often have to predict their users’ needs even before they know what they need - they are in a reactive mode. Each time an end-user reaches out, browses product or services information and offerings, you have the opportunity to gather data. And if you have the right solution and resources in place to analyze this data, you can spot trends, opportunities and even predict what your customers will want in the future.
It is time to connect your products and services now.
With some ROI goals, there’s no reverse gear; some of the best data you can capture is what does not work. Cameras, entry control devices and environmental sensors are all capable of producing event and scene data, often valuable to analyze forensic data about facility breaches or unauthorized personnel entry.
IoT Value Propositions and ROI Models
If someone asked you to create ROI for an investment in the Internet of Security Things or Security IoT devices and their connectivity, where would you start? How do your manufacturers deliver a higher quality of products and systems integrators, those working solutions and services at lower costs?
Security device cost is just one piece of the ROI equation. Today’s market leaders understand that ROI is multi-dimensional and that, in many cases, the cost-savings component can be secondary to other returns such as improving customer satisfaction, brand differentiation, and the collection of accurate data, all of which can also drive increased revenues.
ROI is reinvented and redefined as not just about device product costs, but the use of the data they produce.
Security manufacturers, solution providers, and integrators are focused on something new and significant - doing everything they can to retain and expand relationships with existing customers, their most valuable assets, with new business models, value-added services, and devices delivering rich data for creating ultimate value for the enterprise - security intelligence.
How do you unlock connected security device data? With the industrial Internet and interoperable "smart" IoT devices, you can then unleash the actionable security data into your enterprise and unlock the value of that intelligence.
What is Your ROI Scorecard?
One of the most interesting events I attended this year was "The Great Conversation" by Seattle's Sage Group which highlighted the scorecard a CSO would use to select and deploy the most useful applications. During the event, each solution vendor presented their contribution to the CSO’s scorecard for final "grading" by the audience. Our Security ROI Scorecard can be arrived at in similar fashion. But first, it’s important to consider where does your company stand with today’s public safety and security business and are you using all the tools and data available to you.
- Today’s interoperable security device opportunities offer rich data and intelligence for the taking – and using! With the appropriate authentication, authorization, and cyber security, of course.
- Are you leveraging today’s service opportunities? Proactive monitoring, remote delivery of software updates, remote access, and solution management are all in play.
- Are you analyzing? from predictive maintenance to real-time analytics, leveraging the Forensic-Predictive-Prescriptive data science cycle of your solution is vital.
- Is the solution integrated? Does it share and exchange data from devices to other ecosystems that would find it valuable?
- Are you innovating customer-facing widgets, tools, alerts and automatic processes that continually deliver value and "ultimate" ROI?
The Internet of Security Things, when deployed with open, easily integrated connected devices deliver data, enable remote monitoring, remote service and drive security program cost reduction.
With the Internet of Security Things, no product or asset will be on an island.
Security devices, infrastructure, solution platform, data ingested, analysis and output all coexist in a connected world, interacting and being interdependent. Just as social media drives adoption of IoT, the IoT devices and systems need to be "socially" connected to deliver ROI.
Metrics
How do we measure the smart, connected security product and solution ROI? A metric is itself a success story that describes a quantifiable benefit. This can be any result valuable to the end-user consuming the security data.
For a service-oriented business, the ability to identify, diagnose, and resolve issues remotely is incredibly important to the solution ROI. Video stream monitoring, access transaction, and intrusion event monitoring can be done from anywhere in the world - companies can allocate the best people for the right job, reducing costs and improving the end-user experience.
Connecting and integrating security products so proactive services are a reality increases the first-time fix rate (FTFR), an important metric.
What are the labor cost savings from solution provider or systems integrator to end user when connected security devices are used? With an example, average field service visit to an end user location at about 2.5 hrs., a “loaded” labor rate of $150/hr., and a minimal reduction of 25 percent field visits due to remote diagnosis, the impact across an entire organization can be significant for ten technicians each running 40 service calls a week:
40 hr per week /2.5hr per visit = 16 visits per technician per week
16 visits x 25% savings/visit x 2.5 hrs. per visit = 10 hrs. saved by each technician every week
10 hrs. x $150/hr. = $1500 per technician per week saved
$1500 x ten technicians = $15,000 saved per week
There are costs associated with the benefit of remote diagnosis of security devices, and in our ROI analysis, we would consider those and the payback period after the investment.
A sample ROI analysis template might be organized like this:
- Projected benefits: Year 1 – Year 2 – Year 3 – Year 4 - Total
- Remote diagnosis
- Automated entry controls
- False alarm reduction technology
- Total benefits
- Estimated costs: Year 1 – Year 2 – Year 3 – Year 4 - Total
- Software licenses
- Device and Software maintenance
- Embedded devices and microcomputers
- Storage, distributed and cloud-based
- Professional services
- Net Benefits, Cumulative Net Benefits: Year 1 – Year 2 – Year 3 – Year 4 - Total
Looking Back Quickly; Seeing Before it Happens
There is a strong relationship between validated, predictive analytics and better security-related decisions. To get greater value from the data beyond improved service, you need to analyze the data and utilize the tools and applications that provide insights into the devices providing the connected product data.
Automating physical security processes are the future and provides direct ROI to the security program and cross-platform ROI to other ecosystems that depend on security. At Super Bowl 50, a significant test deployment of self-service security baggage screening was conducted. Is this an economically significant opportunity or are we inviting trouble? All the pieces are available – package pass-through with remote screening, security turnstiles with biometrics, facial recognition and pre-registration and access control anomaly detection. Automated screening line management at major airports is already being considered.
Automating deliveries through fleet autonomous vehicles could dramatically lower vehicle screening costs, improve loss prevention and increase ROI. Although self-driving cars may be years away from maturity, about a dozen trucks from major manufacturers like Volvo and Daimler recently completed a week of largely autonomous driving across Europe, the first such major exercise on the continent, known as the European Truck Platooning Challenge. One set of tandem tractor trailers, made by Scania, traveled more than 2,000 km and crossed four borders to get there. The U.S. Department of Transportation Volpe Center in Cambridge, Massachusetts recently revealed that few barriers remain for automated fleet vehicles to comply with Federal Motor Vehicle Safety Standards.
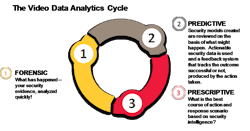
All the above leverage the ability to quickly analyze forensic security data and apply predictive modeling. The ability to apply analytics from forensics to predictive behavior in security technology systems can reduce breaches, hacking, and other threats to safe operation over great distances. (Figure 1: Video data analytics cycle).
The value of smart, connected product data integration IoT data from connected assets can provide a vision of automation not previously possible. In our video analytics data cycle, we can move from “predictive” to the valuable “prescriptive” analytics, on which many automation systems are based. Gathering data that shows personnel, object, and vehicular usage patterns can enhance security screening in prominent areas such as air transportation. Today’s operations and security management at airports are finding a new use for network video surveillance cameras to measure passenger activity and flow during periods where manpower allocation is critical to keep airport operations costs low, passenger safety improved and staff allocated appropriately. Solutions like this that leverage data science, analytics and deliver ROI are becoming a greater focus for public safety.
Recently, the National Institute of Standards and Technology (NIST) and the Video Quality in Public Safety Group (Department of Homeland Security Science and Technology Directorate, DHS S+T) held their first annual Video Analytics in Public Safety event. The unique event brought public safety professionals, academia, industry, and standards development organizations together to share and develop a strategic vision for leveraging technologies valuable in improving public safety, crime reduction, healthcare, airport operations and leveraging smart cities.
“We can only query against that which we have collected, and so if someone has never made a ripple in the pond…in a way, that would get their identity or their interest reflected in our database… nothing will show up because we have no record of that person.” -FBI Director James Comey
With that succinct statement, we can see how being “selective” of what data collect does not necessarily serve our customer needs in the future. Instead, ingesting unstructured data, then applying specialized cognitive processing engines that can be added and optimized later, followed by notification and identification of trends and triggers is our future. One company that has developed such a cognitive platform for ingesting and analyzing video, audio, and metadata is Veritone. For example, the Axis network video cameras running embedded AgentVI analytics processes can be one source of unstructured data. An illustration of the data process for applying multiple, specialized analysis engines for maximum ROI to end users is shown in Figure 2 (Veritone data ingestion and cognitive processing architecture) in the image carousel above.
Just as remote diagnosis has ROI and value to a security systems integrator, the value of a cognitive analytics engine is to the end-user. The connected customer ingests data using a wide range of platforms, the most popular being mobile. Mobile applications for smartphones and tablets are emerging as a way to put applications that interact with products in the hands of field personnel and end users who need remote access from anywhere.
“The customer experience is the next competitive battleground” – Jerry Gregoire, former Dell CIO
This quote reflects the growing importance of customer experience. Providing good service has always been important – and always will be – but now it’s reached a point where it’s absolutely essential. The “connected customer” not only has more power in today’s market, but it’s harder for businesses to differentiate in any other way than the service they provide. [1]
Putting It All Together
So how do we assemble our maximum ROI solution?
What are the benefits of making connected security product data available to multiple systems? The answer is simple: many business processes can be improved by using connected product data. The following is a security business process example improved with connected IoT device data.
Consider a six-step process that incorporates a customer-facing framework, smart IoT devices capable of delivering rich data, a cognitive data ingestion and analysis process and finally monetization through tools, signals, and processes that directly reduce costs.
- Architect
- Ingest data
- Process – analyze
- Integrate
- Innovate
- Activate
The first step is to architect or develop strategy, architecture and technology framework to support a scalable, agile, customer-facing data-rich environment. But how do you make sure the highest percentage of the solution yields ROI?
The key lies in assembling the system so that it no longer lives in a standalone security data “bubble.” Every component, step, process, analysis and output must be either customer/user-facing or at least provide data useful to other systems. And when we refer to additional systems, the level of differentiation can and should range from services, operations, traffic management, public safety, location services, life safety, resource management and energy savings. Strive for a limitless use of sensor data and you’ll get closer to making your solution the most valuable to other ecosystems.
How can you consider ROI on current and future systems if you’re not familiar with what components, services, and output will be most valuable to an end user, public safety agency, a corporation or even a city? Just like starting to put together a complex puzzle, you first look at the overall framework or puzzle picture, work with what you’re familiar with that will fit and deliver business. If you're working in a compressed time frame and miss something critical, you may wind up falling short on a design that’s scalable and agile. “Bottom-up” approaches that use the security device data for multiple solutions will contribute to the solution’s value. (Figure 3: architecting security ROI).
Our model moves from architect to selection with devices that balance security with useful data production and interoperability. See Figure 4 which illustrates the multi-step process.
Too often we confuse protocol interoperability with data interoperability. Today’s network cameras are microcomputers with advanced image processing advanced compression technology for efficiency and applications. What may look appealing price-wise may come with data interoperability and performance issues later. Many network cameras include pre-installed video analytics from the same manufacturer as the camera device. This approach may offer “one-stop shopping” convenience yet yield a limited upgrade path.
Would you buy a smartphone or tablet with applications only developed by the platform vendor? This is the value of solution application developer programs managed by the device or core platform vendor and offering a wide range of choices. For example, Axis Communications Camera Applications Platform (ACAP) offers video analytic solution providers like the following to offer unique processes that run right inside the camera and increase the value of its data:
- People counting, crowd detection and behavior and object detection processes running as “agents” inside the camera and delivering data to a server or cloud application (AgentVI)
- Vehicle license plate recognition application running inside the camera and feature-rich video management system running in a microcomputer system device (IPConfigure)
- Advanced long-range object and perimeter breach detection process inside the visible light or thermal imaging network camera (Eagle-I Edge by Jemez Technology)
- Perimeter Intrusion Detection Device capable of confirming alarm with an AXIS network camera video motion detector to reduce false alarms (Optex America)
- “Smokecatcher” application detecting the visual characteristics of a smoke “plume” for early detection and life safety (Aranni)
- Acoustic signature detection application running inside the network camera, connected to an advanced microphone device and capable of gunshot, glass breakage, aggressive vocal patterns and vehicular crash (Sound Intelligence and Louroe Electronics)
In each of the above cases, ROI is delivered by the “smart” IoT security device powered by the embedded application, delivering valuable data and improved ROI to the end user. Let’s take another look at the above list, but now list the function and ROI benefit(s):
- People counting – allocate staff with customer activity patterns and temporal behavior
- Vehicle License Plate recognition for remote gate control and monitoring from mobile security officer or centralized location – better staff allocation and employee security experience, increased parking revenue
- Long Range Object Detection – early warning of perimeter breaches for high risk and critical infrastructure facilities
- Perimeter Intrusion Detection alarm confirmation (two modes) for reducing the costs associated with false alarms
- Smokecatcher for early warning of potential life safety issue
- Acoustic signature detection for rapid response in active shooter scenarios
Next Generation Codecs: Direct Security and IT ROI
An example of direct ROI for both security and IT management processes considers optimizing storage through advanced video compression and analysis.
A video clip contains 25 or more frames per second. Instead of sending the entire frame every time, a video codec can save a lot of data by only sending the differences between frames. The digital multimedia content (video, audio, metadata) carrying capacity of a network connection is commonly known as bitrate or bandwidth and is measured in megabits per second. A 4G mobile connection might be capable of carrying multiple megabits per second; a home broadband connection may support ten times that amount. To encode and stream video efficiently, the bitrate or bandwidth capacity of the network connection must be greater than the bitrate of the streaming media file.
Significantly more efficient implementation of AVC/h.264 video encoding, and purpose-built for surveillance applications, Zipstream analyzes and optimizes the video stream in real time to save bandwidth and storage while maintaining image quality. This technology makes it possible to continue using VBR for optimum video quality while reducing the storage requirements. Important forensic details such as facial features, vehicle plates are preserved, while scene elements that stay constant like walls, land, and other surfaces are rendered at a higher compression. In Figure 5, Zipstream rendering preserves moving scene elements represented by the green areas while static areas are rendered at a higher compression. Should movement enter the static areas, the scene rendering is adapted quickly to preserve details. (Figure 5: Example Zipstream Rendering Preserves Moving Scene Elements)
Next generation codecs like Zipstream are backward compatible with existing h.264 (AVC) decoding solutions, including video management systems (VMS), physical security information management systems (PSIM), video communications (VC) solutions, Axis Camera Management and Axis Camera Companion Software. What is interesting to note is that the algorithm to compress video according to the h.264 codec is not standardized by the video industry, only the syntax and the method to do decoding and playback.
So how do the next generation codecs compare? HEVC Verification tests were conducted by the Joint Collaborative Team on Video Coding of ITU-T SG 16 WP 3 and ISO/IEC JTC 1/SC 29. The paper “Video Quality Evaluation Methodology and Verification Testing of HEVC Compression Performance,”[2] presents the subjective and objective results of a verification test in which the performance of HEVC and AVC.
The test used video sequences with resolutions ranging from 480p up to UHD, encoded at various quality levels using the HEVC Main profile and the AVC High profile. The tests showed that bit rate savings of 59 percent on average can be achieved by HEVC for the same perceived video quality; however, it has been shown that the bit rates required to achieve good quality of compressed content, as well as the bit rate savings relative to AVC, are highly dependent on the characteristics of the tested content.
Since there is also data comparing Zipstream’s bitrate savings to AVC, and several scenes in the IEEE study are similar, we are able to provide an approximate comparison between HEVC, AVC, and Zipstream. The results are presented in Figure 7 (Comparison of Zipstream and HEVC bitrate savings over AVC, HDTV 720p resolution).
We can see that both Zipstream and HEVC have approximately the same savings for the three Zipstream use cases, similar to the HEVC use cases. Since Zipstream provides backward compatibility with existing video management solutions and smartphones, bitrate reduction, less processor encoding resources, multiple parameter configurations and avoids the threat of additional HEVC licensing, it represents a significant opportunity for tactical and forensic video professionals to significant performance increases.
Healthcare Security and Telemetry ROI
We can see that both Zipstream and HEVC have approximately the same savings for the three Zipstream use cases, similar to the HEVC use cases. Since Zipstream provides backward compatibility with existing video management solutions and smartphones, bitrate reduction, less processor encoding resources, multiple parameter configurations and avoids the threat of additional HEVC licensing, it represents a significant opportunity for tactical and forensic video professionals to significant performance increases.
Some healthcare assets, such as surgical pumps, are designed to be mobile and may be transported with a patient or possibly even out of the hospital. Video surveillance devices can help verify the delivery of this vital care, via remote monitoring. This contributes to giving customers a seamless experience that needs to both manage their assets and verify critical patient care delivery.
The "Ultimate" ROI – Public Safety
Make security great business again – it’s not just about individual projects, but entire cities of intelligence.
In its essence, return on investment (ROI) is a simple concept: it allows a company to check whether or not investing money in a project is worthwhile. However, there is an evolution of thinking that the security project should not have to stand on its own economic merits, but contribute to multiple ecosystems.
Old thinking:
The costs involved in security investment are clear; it is the expected return that is not easy to define.
New Thinking:
Merge security into services, safety and operations. Leverage security sensors to contribute to smart cities, energy savings and other measurable goals. The most amazing benefit immediately follows with the right deployment: life safety. See Figure 6 (Direct and Cross-Platform ROI) above.
Since we can only predict the likelihood of a security event this makes showing ROI much more difficult.
ROI Calculation Risks
Old thinking:
The quality and quantity of the data used for the ROI calculation is the main risk. “Even if you have a formal methodology and a verified tool to perform ROI calculations, you still need to collect reliable data and the “garbage-in/garbage-out rule” applies whenever data collection is performed. Without reliable data, the ROI calculation will also not be valid.
New Thinking:
Ingest everything and have superior analysis tools and specialized cognitive engines to interpret events, alarms, costs and opportunities.
Future Drivers of ROI
Let’s take one example where a better strategy, architecture, and technology solution actually can lower cost, reduce risk, scale quickly, maintain evidence quality levels, and provide business value.
Today’s powerful microcomputing platforms can run entire video management systems on a lower cost device that can be distributed and located closer to the cameras. In a distributed platform video could be recorded without streaming continuously over a city-wide or corporate network. The result is improved quality for evidence and significant reduction in bandwidth, scalable cost savings.
This is the ROI case for applying IoT, Mobile Edge Computing (MEC) and distributed intelligent appliances in network video surveillance appliances.
Recently the solution provider IPConfigure announced the Orchid Community Edition, an IP video management software (VMS) platform with no limitations on camera count or storage and running on a Raspberry Pi 3 microcomputer. Leveraging sophisticated remote access capabilities such as a low-bandwidth mode, the use of this low cost high featured solution is probable our most significant ROI example.
The connected Internet of Security Things is moving rapidly to delivering intelligence and public safety, faster and with the ever-increasing return on security investment.
About the Author: With thirty years of security industry experience, Steve Surfaro is Axis Communications Industry Liaison and Chairman of the ASIS Security Applied Sciences Council. He is also Standards Team Leader for the DHS Video Quality in Public Safety Group. Steve is published in a wide range of security publications and delivers an average of 100 industry-accredited sessions each year. He is author and contributor of the Digital Video Handbook, a DHS S+T publication. Steve recently received the Roy N. Bordes Council Member Award of Excellence from ASIS International. He was also recently honored by BICSI by receiving the Harry J. Pfister Award for Excellence in the Telecommunications Industry recognizing lifetime achievement, sponsored by the University of South Florida, College of Engineering.
Attributions:
[1] “Top 20 customer service quotes and what you can learn from them,” New Voice Media Blog http://www.newvoicemedia.com/blog/top-20-customer-service-quotes-and-what-you-can-learn-from-them/
[2] Video Quality Evaluation Methodology and Verification Testing of HEVC Compression Performance: link here.
About the Author

Steve Surfaro
Steve Surfaro
Steve Surfaro is Chairman of the Public Safety Working Group for the Security Industry Association (SIA) and has more than 30 years of security industry experience. He is a subject matter expert in smart cities and buildings, cybersecurity, forensic video, data science, command center design and first responder technologies. Follow him on Twitter, @stevesurf.