Security Data Intelligence is an Organization’s Best Risk Management Tool
We've been reactive toward security risks for years, waiting for an incident to occur before responding. But what if I told you that a proactive approach, identifying and mitigating security risks before they manifest, can significantly benefit the enterprise? This shift can lead to a more secure environment and a stronger defense against potential threats, providing a sense of reassurance about the strategy's effectiveness.
Our colleagues in the medical industry have been pioneers in proactive risk management. They use predictive analytics to improve operational efficiency, predict disease outbreaks, and improve patient satisfaction. This same approach can be applied to security, allowing us to anticipate and prevent potential threats.
Industrial Revolution 5.0
As a society, we are starting to experience the next phase of the Industrial Revolution, Digital Transformation 5.0. In 1.0, we saw steam and coal-powered machines that boosted manufacturing processes. During 2.0, electrical technology and petroleum came into the picture. The development of new technologies such as the electric power grid, mass production techniques like the production line, and the internal combustion engine marked this era.
As 3.0 approached, computers and programmable logic controllers, robots, in-circuit test electronics, and other aspects of the Information globalization Industry entered the workforce. In our industry, we saw the beginnings of convergence and the move away from analog security systems to digital security systems. 4.0 started blurring the lines between the physical and digital worlds. The Internet of Things, robotics, smart devices, smart buildings, drones, cloud computing, and cognitive computing have integrated the role of technology into everyday life.
Just ask Alexa.
Now, we're entering the era of Digital Transformation 5.0. This phase goes beyond the traditional boundaries between humans and machines, fostering greater collaboration and synergy. It brings the benefits of artificial intelligence and machine learning, revolutionizing security technology and paving the way for more advanced and efficient security measures.
Artificial intelligence and Machine Learning
There's often a lot of confusion about the distinctions between artificial intelligence and machine learning. Artificial intelligence is the theory and development of computer systems that can perform tasks typically requiring human intelligence. On the other hand, machine learning is the field that focuses on developing and researching statistical algorithms that can learn from data.
In simpler terms, if I ask Alexa to build a grocery list consisting of butter, eggs, milk, and oil and Alexa sends it out for fulfillment, that is A.I. If Alexa were to come back to me and say, Jeff, the last time you ordered butter, eggs, milk, and oil you were baking a cake. Did you need flour, too? This would be an example of machine learning.
Data Analysis and Data Analytics
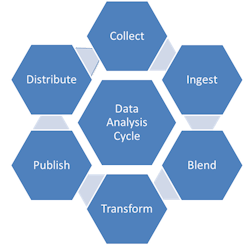
According to Tableau, data analysis is a comprehensive method of inspecting, cleansing, transforming, and modeling data to discover useful information, draw conclusions, and support decision-making. It involves various techniques and methodologies to interpret data from various sources in different formats, both structured and unstructured.
The process of data analysis typically moves through several iterative phases:
- Identify the business question: What problem is the company trying to solve? What do you need to measure, and how will you measure it?
- Collect the raw data sets: Data collection might come from internal sources, like a company’s client relationship management (CRM) software, or from secondary sources, like government records or social media application programming interfaces (APIs).
- Clean the data: This often involves purging duplicate and anomalous data, reconciling inconsistencies, standardizing data structure and format, and dealing with white spaces and other syntax errors.
- Analyze the data: By manipulating the data using various data analysis techniques and tools, you can find trends, correlations, outliers, and variations that tell a story.
Data analysis is a tool that empowers organizations to make informed decisions, predict trends, and improve operational efficiency. As mentioned earlier in the document, data analysis supports strategic planning in businesses, governments, and other organizations.
Similarly, data analysis can help the security industry make proactive decisions regarding risk assessment, fraud detection, and workplace violence events.
Data analysis is a tool that empowers organizations to make informed decisions, predict trends, and improve operational efficiency.
Data analysis has become more critical than ever in the Industrial Revolution 5.0 digital transformation era. The explosion of data generated by digital technologies has led to the advent of what we now call the analysis of big data and data lakes.
Predictive Analytics
Predictive analytics is a branch of advanced analytics that uses historical data, statistical modeling, data mining techniques, and machine learning to predict future outcomes.
Predictive analytics involves examining current and historical data patterns and using that information to predict future trends and events. This can be done manually or using machine-learning algorithms.
An example would be an employee who is having workplace issues. The employee typically works from 8:00 a.m. to 5:00 p.m. Through the access control and building management systems, we learned the employee entered the building at 10:00 p.m. and left at 12:30 a.m. There may be a legitimate reason for the employee to be there. With the system informing us of these facts, the company may want to speak with the employee to determine the nature of their presence at that unusual hour.
In this case, data from the access control systems, correlated with security video cameras and the building management systems, provide precise predictive information.
The Benefits of Predictive Risk Modeling in Security
Reliable data integrated with business data enhances situational awareness in the common operating picture, including reports, dashboards, and business reviews, reducing operational risk beyond physical security. This approach benefits everybody. This will result in better security, risk reduction, operational efficiency, and improved decision-making.
Other benefits include safety near-miss reporting, asset management, life safety, natural disaster and environmental monitoring, compliance with regulatory standards, and supporting consequence of failure frameworks.
What Do Artificial Intelligence and Machine Learning Contribute?
Earlier, we discussed the definitions of Artificial Intelligence and Machine Learning. In practice, we can examine existing data feeds and patterns to learn from them, identify system anomalies, detect impending incidents earlier, and prevent malicious attacks, such as hostile acts toward the organization, its employees, or principals.
The Data Lake -- According to Microsoft and Amazon Web Services, A data lake is a centralized repository that allows you to store all your structured and unstructured data at any scale. It’s a storage repository that can rapidly ingest large amounts of raw data in its native format. The data can be stored as-is without having to structure it first and run different types of analytics—from dashboards and visualizations to big data processing, real-time analytics, and machine learning to guide better decisions.
Data lakes can accommodate all types of data from any source, from structured (database tables, Excel sheets) to semi-structured (XML files, webpages) to unstructured (images, audio files, tweets), all without sacrificing fidelity. The data files are typically stored in staged zones—raw, cleansed, and curated—so that different types of users may use the data in various forms to meet their needs.
Data lakes are essential for businesses as they provide core data consistency across various applications, powering big data analytics, machine learning, predictive analytics, and other forms of intelligent action. They enable organizations to generate different types of insights, including reporting on historical data and doing machine learning, where models are built to forecast likely outcomes and suggest a range of prescribed actions to achieve the optimal result.
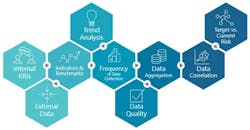
Data Sources -- Many data sources are available to support risk intelligence in security. So, before we consider what data sources we put into the lake, we must determine what problem(s) we are trying to solve. In many practice areas, we call this a “problem statement.” In our work for one global corporation, the problem we were trying to solve was the risk to facilities and developing a risk factor for each building. One particular problem we had to solve was the dynamic risk factors that constantly changed due to political risk, area crime, building function, building occupants, and many other variables. Creating a working group to assist in identifying the variables helped us to select the correct data feeds to solve the problem.
Here are some data points we used.
Physical Security Devices --There are many different physical security devices that we use today that produce data including access control systems, video surveillance systems, alarm systems, lighting, credentialing solutions, cameras, visitor management systems, automated locking devices, robotics, threat intelligence feeds, guard force optimization tools, crime data, historical data, risk assessment data, and other sources that are typically communicated to a Security Operations Center (SOC). Remember, the data collected from these devices can be used to track trends in security incidents, patch up vulnerabilities, and inform future approaches to physical security. It’s essential to have a comprehensive physical security system to protect against theft, vandalism, unauthorized entry, and cyber threats.
Keyword searches are an often overlooked source of data. They can identify mentions of a company, situation, or person on the World Wide Web or the dark web. Keyword searches can be accomplished using industry tools designed for this purpose or a botnet search.
A bot is an application programmed to perform specific tasks. It can run on its own, following the instructions given to it without needing a person to start it. Many bots are designed to do things humans usually would, such as repetitive tasks, accomplishing them much faster than a human can. There are many commercial providers of this service.
Once we have identified the problem and the data, we subject the data to an analysis process.
What Does This All Mean?
Is it worth it to engage in a risk intelligence program? Mature risk intelligence programs increase the enterprise's capability for quicker, more efficient critical decision-making, superior forecasting abilities, optimized variable selection processes, real-time risk mitigation, and business transformation.
The threats, consequences, and resulting impact can devastate an enterprise. Risk can be far costlier than the funds spent implementing a risk intelligence program. The potential loss of an executive, proprietary research, terrorism, workplace violence, large thefts, and natural disasters directly impact a company's financial stability and reputation. Let's use what technology provides us to minimize the impact of risk.
The future is now.
About the Author
Jeffrey A. Slotnick CPP, PSP
President of Setracon ESRMS
Jeffrey A. Slotnick, CPP, PSP
President, Setracon ESRMS
Chair, Board of Advisors Robotic Assistance Devices
Community Vice President, ASIS International
Board of Directors, Jewish Federation of Greater Seattle
Founder Safe Washington
United States Army Engineer Corp, CSM Retired
Trusted Advisor | Leader | Change Agent | Risk Consultant | ESRM Advocate | Security Management Professional | Physical Security Specialist | Master Quality Management Systems Professional | Public Speaker | Author | Media Consultant.
Mr. Jeffrey A. Slotnick, CPP, PSP, is an internationally known Enterprise Security Risk Consultant with over 28 years of experience. Jeff is peer-recognized as a “Thought Leader and Change Agent. He focuses on all Enterprise Security Risk Management facets, including quality management programs, risk, vulnerability, threat assessments, Emergency Response Planning, Business Continuity Planning, and Physical Security System Master Planning, Design, and Integration. As a curriculum developer and master trainer, Jeff advocates for quality professional development and training of security, law enforcement, and military personnel. He is a former member of the North American Board. He is a Community Vice President for ASIS International and a Faculty Advisor for the University of Phoenix Bachelor of Science in Cyber Security and Security Management Degree Program.
Jeff is a regular contributor to Security Executive Magazine and SecurityInfoWatch.com