Why VPN and MFA Alone Fall Short in Securing OT Environments
Key Highlights
- Traditional VPN and MFA are necessary but insufficient; OT environments require additional, context-aware security controls that consider operational risks and system behavior.
- Incident data show that a significant percentage of cybersecurity breaches originate from remote access pathways, underscoring the need for ICS-specific protections beyond identity verification.
- Organizations with comprehensive remote access inventories and ICS-aware monitoring demonstrate stronger detection capabilities and more effective incident response.
- Recovery in industrial systems is complex and slow, underscoring the importance of visibility into user actions and system changes for safe reconstitution.
For many industrial organizations, securing remote access follows a familiar formula: deploy a Virtual Private Network (VPN), require multi-factor authentication (MFA), and consider the risk largely addressed. These controls are essential and form the backbone of secure connectivity in both IT and OT environments.
However, operational technology systems support safety-critical processes, specialized devices, and tightly coupled engineering workflows that demand far more than basic identity verification. VPN and MFA confirm who is accessing the environment, but they do not address the actions a user may take, the systems with which they can interact, or how those actions may affect physical operations. As industrial environments become more interconnected and increasingly reliant on remote capabilities, identity alone is no longer enough.
Incident Data Shows the Limits of Traditional Remote Access Controls
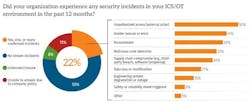
Recent industry data clearly illustrates this gap. Over the past year, 22% of organizations experienced an ICS/OT cybersecurity incident, with half originating from external connectivity or remote access. Another 38% involved ransomware, which frequently exploits remote access pathways bridging IT and OT environments.
These findings do not suggest that VPNs or MFA are ineffective. Rather, they highlight the need for ICS-specific layers of protection that extend beyond identity management and account for engineering context, operational risk, and system behavior.
Detection Has Improved—But Recovery Remains Slow and Complex
The data reveals an important contrast. Many organizations are improving their ability to detect incidents—nearly half identify ICS/OT incidents within 24 hours, and more than 65% take containment action within the following day. This reflects stronger monitoring, better SOC alignment, and improved collaboration between IT and OT teams.
However, remediation timelines remain long. Twenty-two percent of organizations require two to seven days to fully recover, while others take months—or longer—to return to normal operations. This is not a failure of identity controls. It reflects the inherent complexity of safely restoring industrial systems.
OT Security Requires Context-Aware Access Decisions
Even when a user’s identity is verified, OT environments must answer additional questions:
- Which systems should this user access?
- What activities are appropriate for their role?
- Are their actions safe for the process and equipment?
- Who authorizes, monitors, and validates those actions?
These are contextual decisions that VPNs and MFA cannot make independently. In industrial settings, a seemingly benign configuration change can affect physical equipment, disrupt production, or compromise safety. Remote access must therefore be governed as an engineering-controlled activity rather than simply an IT service.
OT Reconstitution Demands Visibility into Actions, Not Just Access
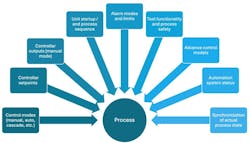
Unlike IT assets, ICS devices cannot simply be reimaged or replaced. Recovery often requires validating alarm limits, controller logic, process sequences, and operational modes against current conditions. Without visibility into what actions were performed remotely, organizations struggle to safely and efficiently reconstitute systems.
This underscores a critical requirement: OT security teams must track user actions, not just user identities.
Cloud Connectivity Expands the Remote Access Attack Surface
Cloud adoption adds another layer of complexity. Only 17% of organizations report no cloud usage across their IT/OT environments. OEM portals, predictive maintenance platforms, analytics tools, and enterprise historians increasingly provide remote access pathways that may not traverse traditional VPNs.
Only 13% of organizations have fully integrated cloud activity into monitoring and detection workflows. This is not a weakness in VPN or MFA; it reflects the reality that modern industrial architectures now include multiple authentication models, embedded agents, and third-party access channels that operate outside traditional controls.
You Can’t Secure What You Haven’t Inventoried
A particularly concerning finding: 31% of organizations do not maintain a formal inventory of remote access points.
Remote access in OT extends far beyond corporate VPNs. It includes vendor portals, OEM support channels, cloud dashboards, portable engineering laptops, contractor sessions, cellular modems, and temporary diagnostics tools. Each exists for a valid operational reason, but without centralized governance, they create blind spots.
Organizations with comprehensive remote access inventories demonstrate stronger detection capabilities, more consistent policy enforcement, and better IT/OT coordination. In OT, visibility is not optional—it is foundational.
Detecting Misuse Requires ICS-Aware Monitoring
Only 13% of organizations report full visibility across the ICS Cyber Kill Chain, with the largest gaps at remote or unmanned facilities that rely heavily on remote access.
Indicators of misuse often include after-hours sessions, unusual cloud-originated access, unauthorized PLC or HMI changes, firmware manipulation, or unexpected activity on engineering workstations. Detecting these behaviors requires tools that understand ICS protocols, engineering workflows, and normal operational patterns, capabilities that identity controls alone cannot provide.
Remote Access Must Be Treated as a Safety-Critical Function
Remote access is one of the most impactful components of industrial cybersecurity. VPN and MFA are essential, but they represent only one layer of a far more complex risk landscape.
Organizations demonstrating the highest levels of preparedness share common traits: complete remote access inventories, ICS-aware access controls, integrated IT/OT monitoring, engaged engineering teams, and regular operationally realistic exercises. They treat remote access not as an IT convenience, but as a safety-critical function requiring engineering-grade rigor.
VPN and MFA remain vital, but true OT defensibility requires controls that account for context, behavior, and consequences. By building on this foundation with ICS-specific access governance, organizations can transform remote access from a persistent risk into a transparent, resilient, and well-controlled component of modern industrial operations.
About the Author

Mike Hoffman
Field CTO at the industrial cybersecurity company Dragos, Inc.
Mike Hoffman is a Field CTO at the industrial cybersecurity company Dragos, Inc., where he focuses on Oil and Gas customers worldwide, helping them increase their ICS/OT cybersecurity maturity and operational resilience. He has over 25 years of experience in Leadership, ICS/OT Security, Controls and Automation, Analyzers, and Instrumentation. He graduated from the SANS Technology Institute's MSISE program and holds more than 17 GIAC certifications, including the GSE. Mike is a SANS Certified Instructor and teaches ICS410 and ICS612.