Automated STIG “hardening” finally comes to government IT
For the thousands of hard-working men and women responsible for securing government IT networks to the Defense Information Systems Agency’s mandatory “STIG” standards, the task can be daunting and even somewhat thankless.
That is because of the STIGs (Security Technical Implementation Guides) outline hundreds of pages of detailed rules that must be followed to properly secure or “harden” the government computer infrastructure.
Given that this work is typically a manual process, it can be extremely tedious and time-consuming for IT personnel. In fact, it is estimated that the government spends hundreds of millions annually to remain in compliance with the STIG standards.
So, as new software tools enter the market that automate the process to near push-button simplicity, the first reaction after “sounds too good to be true,” is considerable relief.
By automating the process, a task that once took weeks – or even months – can be completed in a few hours across all endpoints. Ongoing security updates are also automatic and can be completed in minutes.
Explaining the STIGs
To be fair, there can be a considerable “fog” surrounding the STIGs.
The STIGs essentially exist because government networks are largely built using commercial operating systems (Windows/Linux), database management systems, web servers, and other network devices. The STIGs, therefore, define alterations in operating environment settings so these environments can be configured in the most secure manner possible.
Unfortunately, once an application environment is hardened to the STIG specifications, it can cause installed application to “break,” meaning it won’t install and/or run properly. This impacts both new and legacy applications installed on the system.
Why do applications break? Because they are rarely designed or tested to operate in STIG environments.
For example, if the STIGs require altering some of the controls of the Windows or Linux operating system the application is built on, the application will break. If an application requires specific capabilities to operate and the STIGs prohibit or blocks those capabilities, the application will fail to load or operate. And so on.
Unfortunately, there are no generic set of STIG “rules” that can be applied to all applications. Instead, server policies must be manually adjusted on an application by application, server by server basis - which can take many weeks and cost in excess of $10,000 annually, per server instance.
“If the same policies and configurations could be implemented on all systems, STIG compliance would be a rather easy exercise,” explains Brian Hajost of SteelCloud and an expert on automated STIG compliance. “Commercial and government applications respond to security policies differently. The controls for each system, therefore, have to be uniquely adapted or tuned to each application environment.”
This painstaking task often falls to system administrators, application administrators or information assurance staff.
“There are thousands of IT people across government that are asked to address the STIG compliance manually, but many times are not experienced or trained to do so,” says Hajost. “So, they muddle through, but the initial hardening effort can take weeks or even months.”
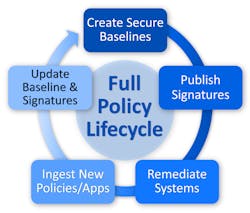
Fortunately, new automated tools are available that automate STIG compliance. Products such as ConfigOS from SteelCloud harden existing government networks automatically, even across complex and disparate infrastructures with varying security levels.
ConfigOS identifies and hardens all controls considered a potential security risk. As outlined in the STIGs, risks are categorized into three levels (1/2/3) with Category 1 being the most severe and having the highest priority.
The software then produces a domain-independent comprehensive policy “signature” including user-defined documentation and STIG policy waivers. In this step alone, weeks, or months of manual work can be completed in an hour.
The signature and documentation are included in a secure, encrypted signature container that is used to scan endpoints (laptops, desktops, physical/cloud servers) without being installed on any of them. The time it takes to remediate hundreds of STIG controls on each endpoint is typically under 90 seconds and ConfigOS executes multiple remediations at a time.
“The government publishes the [STIG] book and we are just automating the tedious work to get the job done,” says Hajost.
ConfigOS supports over 6,000 standard STIG controls in a wide range of tested content. However, the software is also designed to allow users to tailor controls to respond to an application’s requirements.
“We could enforce the STIGs to the letter, but that doesn’t work if it means the application will not run,” explains Hajost. “So ConfigOS creates an operational policy that is as close to the published STIGs as possible, but still allows the application to function as designed,” explains Hajost.
The signature containers can then be transported across large and small networks, classified environments, labs, disconnected networks, and tactical environments with connected and disconnected endpoints. No other changes are required to the network, security and no software is installed on any endpoints.
To date, ConfigOS has been licensed by just about every branch of the Department of Defense, as well as parts of DHS, HHS, and Department of Energy. The product is also used by large defense contractors and in programs for all branches of the military.
Hajost adds that automation is even more important given that STIG compliance is an ongoing process with new security updates introduced periodically
Keeping Current
The STIGs, for example, are updated every 90 days to account for newly discovered vulnerabilities as well as changes and updates to by the vendors supplying the major operating environment components.
With ConfigOS that means that within two business days after DISA publishes a new version of the STIGs, new tested production content is made available to customers.
“When it is a manual task, security updates to existing applications and operating systems are typically delayed by months,” says Hajost.
The software can also speed implementation of new network applications, servers and appliances by evaluating and hardening each prior to installation.
Hajost estimates automating the process reduces initial hardening time by 90 [ercent while reducing system security policy maintenance expenses by about 70%.
Given the potential cost savings of automating STIG, policy compliance exceeds hundreds of millions of dollars annually, IT personnel struggling to secure government networks manually may find this one task they are happy to automate.
For more information about ConfigOS from SteelCloud call (703) 674-5500; or visit www.steelcloud.com.
About the author: Jeff Elliott is a Torrance, Calif.-based technical writer. He has researched and written about industrial technologies and issues for the past 20 years.
About the Author