Security gap-closing strategies for 2023
Thanks to the twin IT megatrends of exponentially rising technology capabilities and exponentially falling prices, it is now feasible to close many physical security gaps that could not be sufficiently or affordably addressed until now.
Physical security risk mitigation is based on reducing security risks to acceptable levels, at an acceptable cost.
The two IT megatrends, combined with new AI-based processing capabilities for security devices and applications, are making it possible to use a high-ROI security technology strategy based on addressing critical security gaps that haven’t been sufficiently mitigatable until now.
This article presents six examples of using advanced technologies to address long-standing physical security challenges, such as tailgating detection/prevention, biometric authentication for critical areas, comprehensive management of access control privileges at large scale, automated AI-based security video tours, and achieving “living” emergency response plans that don’t get outdated, maintaining security operations center physical situational awareness throughout the entirety of an incident.
This is not intended to be a complete list or catalog, but to provide sufficient examples to make the case for considering a new-technology security-gap-closing strategy for the coming year.
Touchless Biometric Authentication
In the past couple of decades, deploying facial access authentication for only a few critical locations has been challenging due to the high cost per access point, the complexity of integrating the facial recognition system to the access control system (ACS), and the onerous process of enrollment.
Imagine instead a facial authentication solution that:
- combines AI and 3D sensing technologies
- connects to the ACS like a standard card reader (via Wiegand or OSDP), requiring no system integration
- performs automated authorized user enrollment at the door device
- works without needing to store or transmit video images
- collects no personally identifying information (PII)
- protects data end to end with military grade encryption
- does not collect any data for non-enrolled users
- operates in full compliance with EU and U.S. privacy laws
Its Wiegand and OSDP connectivity makes it automatically compatible with nearly all existing card access systems. Additionally, it is also ONVIF Profile S and Profile T compliant and can optionally transmit video images of enrolled users to a VMS if desired. It can also notify an ACS and VMS of tailgating events.
The reader device made in the U.S. by Alcatraz AI is named The Rock. The Alcatraz Administration Portal software is hosted on AWS, or can be run in an Alcatraz on-premises appliance, or on customer-provided IT infrastructure.
Importantly, Alcatraz is the third company in the physical security industry to join the Cloud Security Alliance STAR Registry and submit its cloud security self-assessment. (The first two companies to do so are Brivo Systems and Eagle Eye Networks.)
Power plants, banks, headquarters’ senior executive spaces, data centers, laboratories, healthcare medication storage and dispensing areas, industrial hazardous material storage, and areas with critical or highly confidential operations -- including NOCs and SOCs -- can now easily utilize facial authentication using their existing access control systems.
Crossing, Piggybacking
and Tailgating Detection
DoorGuard by Orion Entrance Control utilizes an advanced LIDAR (light detection and ranging) technology -– a key component in autonomous vehicles –- combined with specially developed deep learning AI, to build a 3D model of the area in front of a doorway and analyze the objects and activities within it. (Video-based machine vision anti-tailgating technology is two-dimensional, and radar-based anti-tailgating technology is one-dimensional.)
The DoorGuard sensor component is roughly 4.43 inches x 6.63 inches x 2.27 inches and mounts above the door either on the wall or the ceiling. Its deep-learning analysis detects and reports three distinct conditions.
Crossing: In the case of a bi-directional door, including a free exit-controlled entry door, an unauthorized person can sneak in as someone leaves. Likewise, as an individual is leaving the secure area, they might hold the door open to allow someone to enter without having to present a credential.
Piggybacking: An unauthorized person gains entry to a secure area by following an authorized individual, with that individual’s permission, as may occur if the authorized individual holds the door open to keep it from closing, or the unauthorized person tries to outsmart the system by walking very closely behind the authorized individual.
Tailgating: An unauthorized person gains entry to a secure area by following an authorized individual, without that individual’s knowledge or consent, such as by slipping through an almost closed door.
DoorGuard can cover a single or double door and has 8 operating modes.
- Deny access: Deny access until the door detection area contains a single individual and alert if a crossing violation occurs.
- Alert on violation: Alert on crossing, piggyback, tailgate or wrong way violation.
- Closed mode – Will not accept ACS inputs.
- Disabled mode – Free entry and exit with no alarms.
- Free Entry mode – Can enter without using the ACS and no entry alarms. Card exit required.\
- Free Exit mode – Can exit without using the ACS and no exit alarms. Card entry required.
- High security mode – Only 1 person in the sensors field of view is allowed for DoorGuard to accept a credit.
- High throughput mode (also called “Card Stacking”): Allows crowding and accumulation of multiple authorizations, permitting authorized entries through continuously open door until the number of authorizations has been used or until the door is closed or a specified timeout is reached.
One reason for its accuracy is that it correctly recognizes and differentiates between the following target object types and conditions within the door entry detection zone:
- Adult height Person
- Child height Person
- Person carrying an object
- Person wearing a hat
- Person pulling or pushing an object, such as a stroller or rolling laptop case
- Multiple people in close proximity, down to 0.0 inches of separation.
- Dog or other walking pet animal
- Wheelchair occupied
- Wheelchair unoccupied
- One way or wrong way traffic
- Crawling on knees or belly
There is additional functionality, but the point of the details provided above is to show the huge difference between earlier generations of tailgating detection and today’s advanced sensor and AI-based product functionality.
Maintaining Situational Awareness
Liquid360 is software that utilizes a custom-built digital twin of a facility, into which it embeds live video from the facility’s surveillance cameras. Liquid360 presents navigable visual depiction of events in real time, with semi-transparent building walls and the ability to adjust the view by -- for example, remove building floors -- so as to look at what’s happening inside the building.
Multiple incident response stakeholders, each with their own tablets, can manipulate their own views to see what they need to see as the incident unfolds. A touch on the screen will automatically select the PTZ camera with the best view of the area of interest and move/zoom it to obtain the fullest view. From there the PTZ camera can be further manipulated manually. Liquid360 can also utilize building sensors to depict building occupancy. Tablets can be shared with first responders as they arrive.
The system, for the first time in the history of security incident response, extends situational awareness beyond the security command center and out where responders and incident stakeholders are. See the videos and images and further information on the Liquid360 Website.
This is invaluable security technology for schools and universities, sports stadiums and other large venues. Expect to see integrations with outdoor and indoor video drones, as through these responders can eyes and ears anywhere in the field of action without putting first responders at risk.
Auditable Integrity for Large Scale
Physical Access Management
Over the past 50 years, physical access control systems have grown from standalone products for single buildings with 8, 16 or 32 controlled doors and up to a few hundred cardholders, to large enterprise systems for companies with thousands of doors and tens of thousands of credential-holders.
Access privilege factors became complicated, including elements such as safety training requirements and contractor insurance requirements.
Between 10% and 25% of people records in a large company change every year. The situation can lead to significant access privilege creep, where privileges are expanded as responsibilities change, often leaving outdated and inappropriate privileges in place.
It can be very hard to keep up with changes due to mergers, acquisitions and sell-offs. Furthermore, people generally don’t complain about too much access. They only complain when their credentials don’t allow them access they need or want.
Part of the problem has been that database technologies didn’t exist that could deal with the complexities of access management for large enterprise employee populations. Some of the access privilege data resides outside of the access control systems in other systems or records, and there hasn’t been an easy way to establish and maintain the data connections required.
How, however, the problem is now solvable using a special type of database called a graph database, which is not based on traditional rows and columns of data, but is designed to store information about people and assets and the requirements and relationships that relate to them.
A graph database is built to hold and navigate billions of relationships and query them with millisecond latency. It’s how LinkedIn can show all your 1st-, 2nd-, and 3rd-degree connections, and the mutual contacts with your 2nd level contacts, all in real-time.
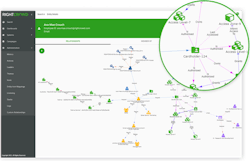
Now, using graph database technology and some patented software, RightCrowd has produced a cloud-based application named Access Analytics.
It allows physical security, OT teams, IT, HR and business personnel to collaborate, review and take action to correct inappropriate physical or logical access to any assets and enterprise systems using a single graphical view that can present the access privilege information from multiple perspectives.
It can answer simple questions like, “Whose safety training is expiring within the next 30 days?” Access Analytics can initiate a notification to the individuals who need to redo their training, the people who manage their access privileges, and the supervisors who may need to help facilitate the time off work for training.
Access Analytics is a lightweight software that works with daily input feeds, typically a simple CSV file exported from the systems with access privilege information.
Access Analytics works with any access privilege management software, including traditional physical access control systems, Microsoft Active Directory, visitor management systems, parking access management systems, physical lock and key management software, HR systems, learning management systems and so on. It works for physical card credentials of all types, as well as mobile device digital credentials. The application is future-proof in the sense that it can work with all the systems and credentials in place now, plus those that will be adopted in the future.
The brilliant thing is that Access Analytics is a tool that uses your existing access management roles, responsibilities, processes and procedures to correct access privilege errors.
It does this by providing notifications to the access decision-makers, who can use the Access Analytics main view (see Figure 1) to see the full context for the recommendation, if needed.
Often there is no need to consult the main view, because the rationale behind the recommendation is obvious, such as to remove a cardholder because the person’s employment was terminated.
This process amounts to a daily audit of access privileges. The Access Analytics data records can also be used to view any previous state of access privilege assignments at any time. This can be important to security investigations where determining who had access to specific assets at a specific time is a critical element of the investigation.
Many companies are currently considering upgrading multiple disparate physical access control systems to standardize on a single access management software product. Sometimes that upgrade is software-based, such as for deployments bases on Mercury Security hardware, and sometimes it involves hardware changeout as well.
Any such deployment project can be simplified by performing access-privilege cleanup prior to performing the upgrade.
Historically, some companies have decided to fix their access privilege problem by re-credentialing all individuals and starting from scratch with the assignment of access privileges. That approach is highly disruptive, always takes longer than estimated, and doesn’t keep access privilege problems from creeping in again, which is what always happens.
Other companies have simply exported the cardholder and privilege data from their existing access control systems and imported it into the new system. This preserves the access privilege problems without providing a means to correct it.
Companies take this approach when they don’t realize the full extent of their access privilege problems, and wrongly assume that somehow the new system will let them manage access privileges better.
Using access analytics to resolve the access privilege problems prior to large-scale upgrades will lower the cost and shorten the timeframe of the upgrade. It will enable progressive upgrades at any pace that makes sense and ensure that access privileges are always correct throughout the upgrade. There will be no “limbo” state for access privileges where no one is sure where access privileges stand until the upgrade is complete.
‘Living’ Emergency Response Plans
Planning for business emergency and crisis response (often labelled business continuity and disaster recovery planning) has gone through three stages already: paper documents (in binders sitting on shelves), electronic documents (PDF files and web pages), and applications (both client-server and cloud). All have required training and drilling.
However, often training and drilling do not closely match the emergency or crisis that unfolds, and the infrequently trained and drilled actions aren’t automatically called into play under the high stress of actual events.
Now that mobile devices (smartphones, tablets, etc.) are ubiquitous, everyone impacted by an unfolding situation can be kept up to date in real time as to their individual situation and how to protect themselves and others.
But that would take cloud-based applications that are far more configurable, scalable and usable than traditional emergency response applications have been.
Emergency response plans must be easily updatable. Each individual with a responding or self-protection role needs a playbook to follow and must be able to revise it as required (without losing the original) to fit unfolding events.
The application must provide a common operating picture (COP) that is a continuously updated overview of the incident compiled throughout the incident's life cycle from data shared between emergency management, individuals executing their parts of the response plan, and those with self-protection roles -– plus data obtained via social listening and risk monitoring services. It must enable situation reports that can flow into the COP for true real-time situational awareness.
It must be a lightweight application that is easily accessible via existing services used by the organization (such as Microsoft Teams, Slack, ServiceNow and so on) without placing any data inside those services, so as to maintain the confidentiality, integrity and availability of data and application functionality.
It must support and enable the best practice workflows and actions of Environment, Health, Safety, Security, and Corporate Communications – enabling their leaders to manage the response realms that are within their scopes of responsibility – while subscribing to the overall incident command or crisis management structure that is the framework for response and situation management.
It must provide timestamped records of actions taken and communications given and received, including all modifications and elaborations to response plan elements, such as role and task assignments, polls launched and answers received, checklists issuance, notifications issued, and action progress.
It must also enable simple generation of after-action reports. It must also support table-top drilling of all or part of a response plan, including COP generation and after-action reporting.
Playbooks must have an “expiration date,” which means a date by which the person or persons responsible must review the playbook and update it as needed so that contact information is kept current, and that the playbook is kept in sync with related playbooks. This practice is what makes “living emergency response plans” feasible.
This is no longer pie-in-the-sky thinking. At least one such application does exist, In Case of Crisis 365 by RockDove Solutions (www.rockdovesolutions.com).
Robotic Services Combine
Human, Artificial Intelligence
For decades, companies have relied on traditional guard service security officers to perform patrols, observe and report, escort visitors and vendors, detect abnormal building conditions such as pipe and roof leaks, thermal anomalies, fire extinguisher checks, hazardous spills and gases, emergency exit path obstructions, trash on building grounds, unoccupied desks with computer logons still active, check on lone workers, and so on.
But humans aren’t perfect, and they don’t always perform their tasks perfectly. They get tired, need breaks, make mistakes, have lapses in judgement, have imperfect memories, get distracted, aren’t always fully observant, and so on.
However, previous attempts at creating security robots didn’t succeed because the robots weren’t “human enough” and thus required burdensome attention and oversight. They also weren’t technically capable enough and had limited intelligence. However, they could work continuous 24/7 shifts with no overtime and no drops in performance. They didn’t need meals and bio breaks. They didn’t require employment benefits.
Today – thanks to advances in artificial intelligence, video cameras, environmental sensors, and robotic machinery – many of the routine repetitive security patrol tasks can be performed better and more cost-effectively by a robot whose sensor capabilities and artificial intelligence allow it to learn the environment, identify abnormal conditions, and report accurately on them with video and audio evidence. They have perfect recall, have no biases, and have faster responses.
But what about the need to respond to unusual situations and interact with humans? Such as expediting the full evacuation of a building. If a robot can’t do that, it can’t replace a human security officer.
The founders of Cobalt Robotics realized that what was needed is a fleet of security robots that were aesthetically designed and didn’t resemble TV and science fiction movie robots, weren’t physically imposing or intimidating, used state of the art self-driving technology to navigate its environment and operate autonomously for routine tasks, and could be piloted remotely by a human when incident response actions or human interaction were necessary.
Two-way audio and video must allow a remote operator to interact with nearby people, provide a friendly face and confident disposition, as may be required by the situation.
Thus, the Cobalt founders established the first robotic service company, with a command center staffed by highly-trained analysts, backed by personnel with decades of military and physical security experience.
The purpose of Cobalt Robotics is not just to provide better observation and reporting than human security officers at a lower cost, but to continually improve the risk mitigation of the facility’s security program and the business benefits received through its robotic services.
Closing Long-Standing Security Gaps
The technologies described above are examples of ways to close some of the long-standing security gaps that we’ve learned to live with and accept because there were no effective-enough and affordable-enough solutions.
Advances in information technology and artificial intelligence are now making the impossible possible, in terms of closing security gaps and improving security operations and the overall effectiveness of physical security programs. Consider planning to make 2023 the year that your long-standing security gaps get effectively closed.
About the Author: Ray Bernard, PSP CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). Mr. Bernard is a Subject Matter Expert Faculty of the Security Executive Council and an active member of the ASIS International member councils for Physical Security and IT Security.
About the Author

Ray Bernard, PSP, CHS-III
Ray Bernard, PSP, CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon. Ray has recently released an insightful downloadable eBook titled, Future-Ready Network Design for Physical Security Systems, available in English and Spanish.
Follow him on LinkedIn: www.linkedin.com/in/raybernard.
Follow him on Twitter: @RayBernardRBCS.